Integrity Monitoring - Bitdefender Techzone
GravityZone Integrity Monitoring: Ensures data integrity, detects changes, and meets regulations, Vital cybersecurity solution for organisations.
In today's increasingly connected digital environment, the preservation of data and system integrity has emerged as a paramount concern. Once an attacker has gained privileged access to a system, they commonly modify files to plant ransomware, exfiltrate data from businesses, and perform other nefarious tasks. Organizations concerned about the safety of their data require the capacity to identify unwanted changes in their environments. File Integrity Monitoring (FIM) offers an indispensable solution to this pressing issue, providing the necessary vigilance and control to maintain a stable and secure IT environment.
GravityZone extends the capabilities of traditional File Integrity Monitoring to entire systems. GravityZone Integrity Monitoring assesses changes compared to a baseline or good, known state of the monitored entities, such as files, directories, registries, installed applications, services, and users. It also provides powerful tools for the prevention of unauthorized changes, alerting when changes occur, and includes remediation capabilities. This document discusses the importance of integrity monitoring for organizations of all sizes, reviews critical control elements, outlines regulatory requirements mandating its use, and explores Bitdefender’s innovative integrity monitoring solution.
The Importance of Integrity Monitoring
Integrity monitoring involves continuously checking and validating the consistency of data and system configurations. It plays a vital role in identifying unauthorized modifications that could indicate a security breach or system malfunction. No organization, irrespective of its size or sector, is immune to cyber threats. Integrity monitoring is a potent tool that ensures that organizations' data and system configurations remain unaltered and secure from both external and internal threats.
Threats can include anything from sophisticated state-sponsored attacks to a disgruntled employee altering critical files. Organizations must consider that the cost of a breach—both in financial terms and reputational damage—can be disastrous. Hence, maintaining integrity through continuous monitoring is crucial.
Critical Controls for Integrity Monitoring:
Real-Time Monitoring: The system should provide real-time monitoring and alerting for any unauthorized change. This capability allows for immediate detection and action, limiting potential damage.
Remediation Actions: The solution should be able to perform remediation actions on unauthorized entity changes.
Baseline Snapshots: These are 'good state' captures of system entity states. Any deviation from the baseline can trigger an alert, making the detection of unauthorized changes possible.
Out-of-the-Box Default Rules: Security teams should not be burdened to manually create rules for known critical entities. The solution should be pre-configured to monitor these entities by default.
Performance Optimizations: Integrity monitoring can become a resource intensive process. As resources vary across systems, it’s imperative that the solution can be adjusted to perform best on different configuration types.
Integrity Monitoring and Regulatory Requirements
Several regulatory standards mandate the implementation of file and system-wide integrity monitoring. These regulations underscore the global importance of integrity in securing confidential and sensitive data. Some of the notable regulatory requirements include.
PCI DSS: The Payment Card Industry Data Security Standard (PCI DSS) requires file integrity monitoring for all system components to protect cardholder data.
HIPAA: The Health Insurance Portability and Accountability Act (HIPAA) mandates integrity controls to guard against improper alteration or destruction of electronic protected health information (ePHI).
SOX: The Sarbanes-Oxley Act (SOX) necessitates controls that assure the integrity of financial information.
GDPR: The General Data Protection Regulation (GDPR) also emphasizes data integrity, requiring organizations to ensure the ongoing confidentiality, integrity, availability, and resilience of processing systems and services.
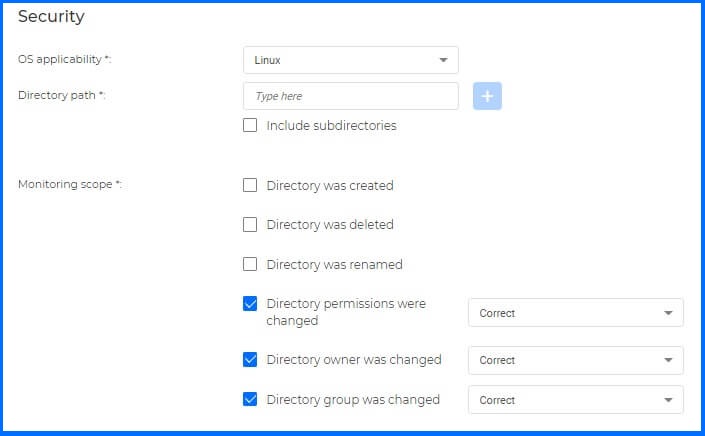
Figure 1: GravityZone Integrity Monitoring allows for various controls related to file creation, deletion, changes, ownership changes and more.
Integrity Monitoring as Augmented Security
Traditional cybersecurity tools, such as antivirus software and Extended Detection and Response (XDR) platforms, are invaluable assets in a comprehensive security approach. These tools primarily focus on identifying and mitigating known threats based on distinct signatures, heuristics, and behavioral patterns. In contrast, system-wide integrity monitoring technology shifts the approach slightly by guaranteeing the consistent state and integrity of system and application components.
By continuously checking for any unauthorized alterations to system and application configurations, Integrity Monitoring ensure systems and their components maintain a desired and secure state. This means that any deviation, regardless of whether it's caused by a known or a new unidentified threat, results in an immediate alert. Such monitoring can even detect anomalies that might slip past an antivirus or an XDR, especially in the case of zero-day exploits that don't fit any recognized pattern.
For instance, imagine a scenario where an administrator inadvertently modifies a security setting on a pivotal server. This action might leave the server vulnerable. While an antivirus or XDR might not immediately flag this change if no known malware tries to exploit this new vulnerability, the integrity monitoring tool would. It would alert the cybersecurity team about the unauthorized change, offering an opportunity to correct the issue proactively.
Similarly, consider a situation where a novel malware strain discreetly modifies a system file to ensure its persistence or to create a backdoor. If the malware's signature isn't recognized, traditional antivirus solutions might overlook it. An XDR might also miss it if the malware's actions don't match established behavioral patterns. Yet, the integrity monitor would pick up on the unauthorized change, drawing attention to the potentially compromised element.
GravityZone Integrity Monitoring Explained
Bitdefender offers a revolutionary approach to Integrity Monitoring by not limiting itself to only monitoring files. Through security agents installed on Windows or Linux systems, GravityZone Integrity Monitoring, depending on the operating system, looks for:
Files
Directories
Registry Keys
Installed Software
Services
User Accounts
Through a series of default and custom rules and rule sets, organizations can monitor and prevent changes to these entities and receive alerts when these changes take place.
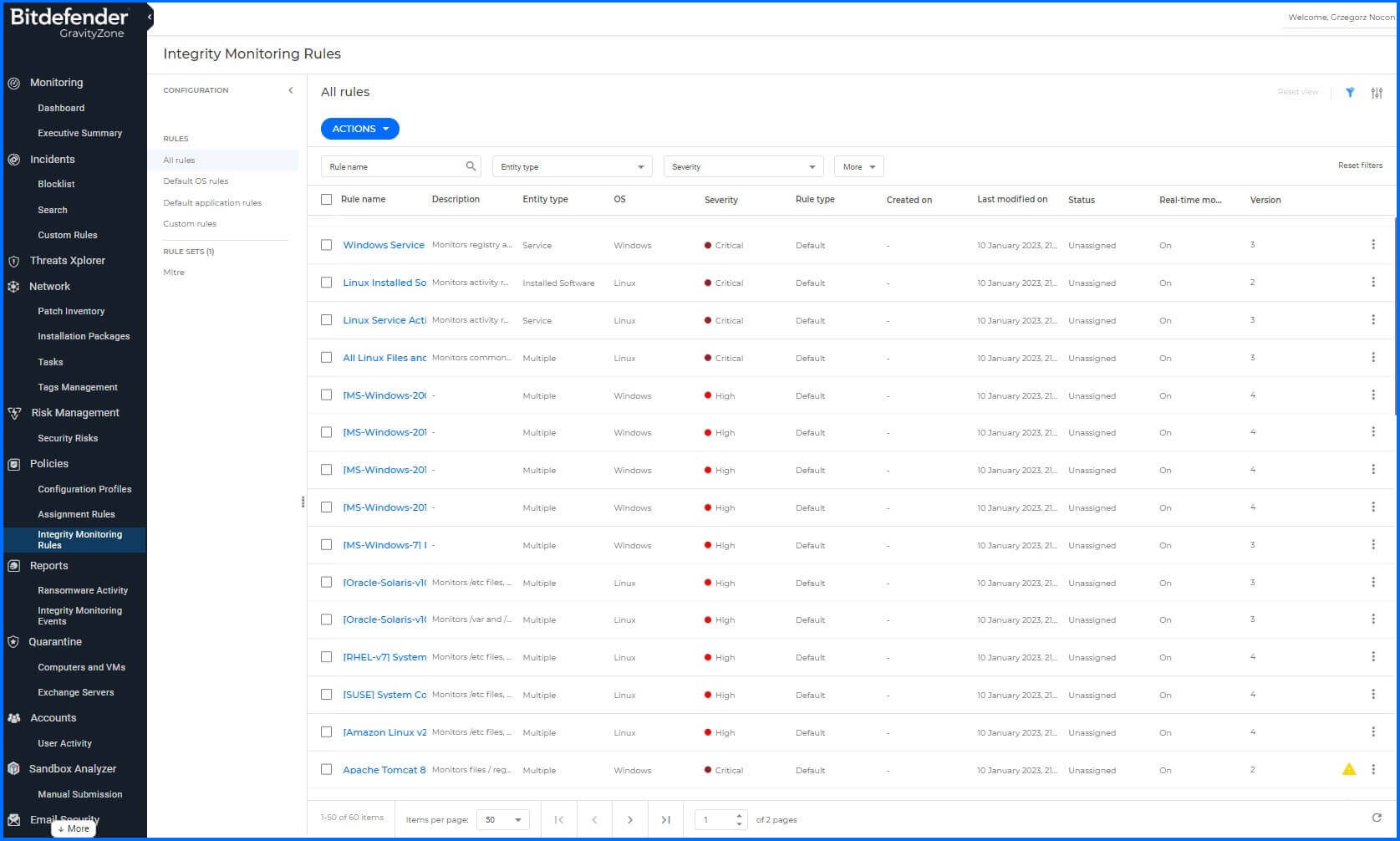
Figure 2: Several types of Integrity Monitoring Rules and Rulesets can be created, edited, and removed from the GravityZone console.
Default Rules
Default rules are created and supported by Bitdefender. These rules cover critical operating systems, applications files and registry keys, assuring that the integrity of the system is secure without requiring extensive configuration by the administrator. Specific details of all entities that are monitored using the default rules can be found at our Bitdefender Support Center here.
Custom Rules
Custom Rules allows security teams to specify the entities that they want monitoring and protected by GravityZone Integrity Monitoring. The Custom Rules must be configured with the following fields:
Rule name: must be unique. You cannot have two rules with the same name.
Description: a general description of the rule
Severity: this option can be set to low, medium, high, or critical
Entity Type: the following types of entities are available:
File
Directory
Registry Key
Registry Value
Once the Entity Type is selected, additional configuration fields are made available that empower the security teams with monitoring and remediation tools against unauhtorized changes.
Detailed information about Integrity Monitoring configurations can be found at our Bitdefender Support Center here.
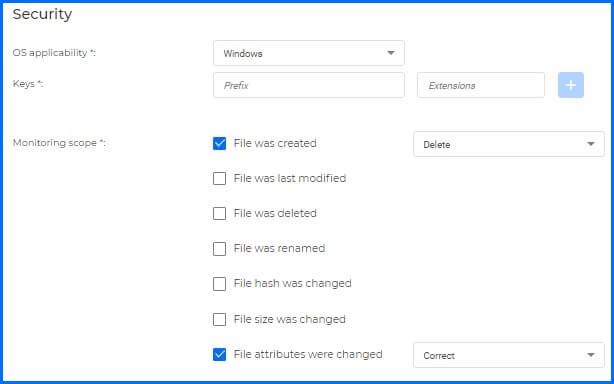
Figure 3: Entity Type configuration gives security teams extensive controls over how the entity is monitored and what remediation actions are taken if a change is detected.
Through the rules, security teams can configure a plethora of automatic remediation options once an unauthorized change is detected:
For files and directories:
Delete unwanted created files and directories
Correct attribute changes
Correct changes in permission, owner, and group
Correct modification in file name, or hash changes
For the Windows Registry:
Delete unwanted registry key and sub-key creation
Correct deleted and modified registry keys and values
Correct registry value hash and size changes
Restrictors
GravityZone Integrity Monitoring has implemented restrictors with the sole purpose of reducing alert fatigue. These restrictors are designed to cover human errors.
For example, if you create a rule to monitor every .log file on your endpoint, Integrity Monitoring is not going to allow you to add it, and thus prevent the endpoint from being flooded by notifications and/or events.
Customizable Performance Modes
Another key component of any suitable Integrity Monitoring technology is the ability to modify it’s performance impact on the system it is monitoring. GravityZone Integrity Monitoring provides just that by providing organizations with three distinct processing profiles that can be configured through the Integiry Monitoring policies:
Fast: Consumes events as they come without delay. Intended for critical systems with the highest urgency of alerting.
Normal: Buffers events for 3 seconds then consumes them. Intended for systems of high importance. This settings reduces the total number of alerts by allowing more time for deduplication.
Slow: Buffers events for 6 seconds then consumes them. Intended for systems of normal importance. This setting further reduces the number of alerts by running several deduplication actions on the events before creating an alert.
As organizations have systems with diverging processing power, it’s important that the Integrity Monitoring system can be fine-tuned to supervise those systems without negatively impacting their ability to perform their normal tasks. Additionally, the variable performance settings allows for deduplication of alerts, and the capacity to reduce alert fatigue.
Assigning IM Rule Sets to Policies
In Bitdefender GravityZone, a "policy" is a set of configurations that dictate how the security solution behaves on the devices where it's applied. The policy defines the security settings and rules for devices and users within a particular group or organizational segment. GravityZone Integrity Monitoring allows security teams to assign different Rulesets to systems that govern what Integirty Monitoring rules are applied to the systems with the assigned policies. Once the policies are applied, the endpoints start sending events to the GravityZone console and can then be reviewed from the Integrity Monitoring Events section of the console.
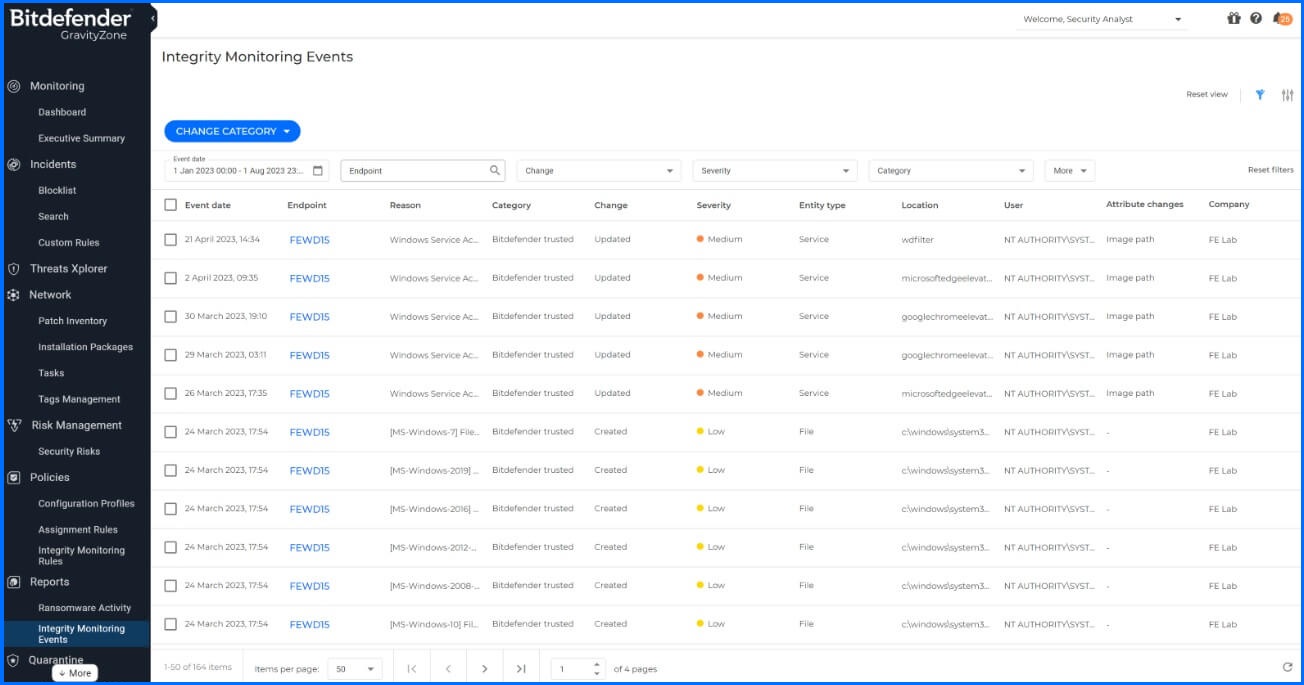
Figure 4: The Integrity Monitoring Events sections lets security teams quickly review and asses IM events from endpoints
Integrity Monitoring Reporting
GravityZone includes reporting options for Integrity Monitoring that allow security teams to easily discern the status of system changes. When a file is modified, a new entry is added in the Integrity Monitoring section of the GravityZone reports. Security teams have several available filtering options:
Event date
Endpoint FQDN
Change - This filtering option allows you to select one or multiple types of changes:
All
Created
Updated
Deleted
Renamed
Severity - This filtering option allows you to select the severity type
All
Low
Medium
High
Critical
More - This filtering option allows you to select other options:
All
Reason
Entity type
Location (of the entity that was changed)
User (account that initiated the change)
Various sorting options are also made available that allows security teams to search for events by date, Endpoint name or IP, change type, severity, category, and additional fields covering reason, entity type, location, and user. Selecting an event from the list will display additional event details including attribute changes and more.
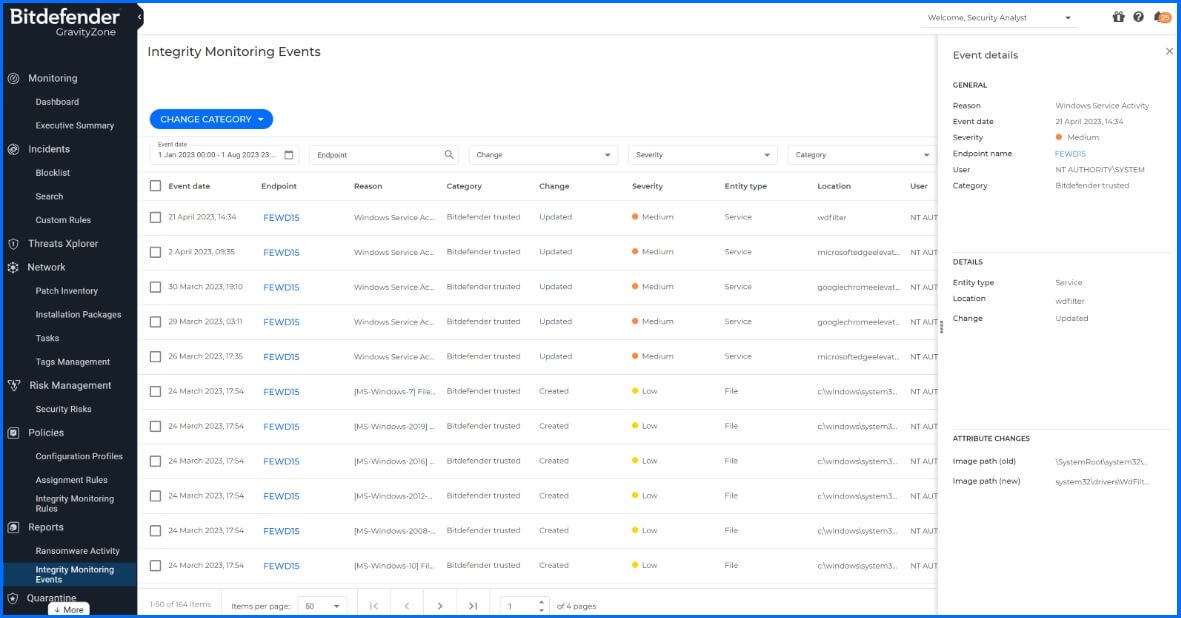
Reports can be exported in .CSV and .PDF format or emailed in either format directly from the GravityZone console. Additional visibility into reports can be obtained by creating a reporting dashlet in the GravityZone Dashboard. Additional information on how to manage GravityZone Integrity Monitoring, including how to suspend and/or disable the service on endpoints can be found at our Bitdefender Support Center here.
Recommended Content
To learn more about the technologies included in the Detection layer we recommend reading the next article Security Data Lake.
More Resources
GravityZone Integrity Monitoring official website: GravityZone Integrity Monitoring
Bitdefender Integrity Monitoring Guided Tour: Integrity Monitoring Guided Tour