Content Control - Bitdefender TechZone
Explore GravityZone Content Control: A cybersecurity multi-tool for web filtering, application control, and data protection. Learn how it safeguards against cyber threats, enhances productivity, and ensures regulatory compliance.
Securing systems from malicious sites and protecting sensitive data during online transmission is crucial for operational integrity and maintaining trust. Content control plays a key role in this. It's like a multi-tool for cybersecurity, combining features such as web content filtering and data protection right on your device, allowing or blocking specific apps, and setting strict rules for data sent via web pages and emails. With more people working from different places, either from the office or home and using various devices, having these protective measures directly on the device becomes crucial. This ensures that no matter where you're working from or what network you're on, your data remains secure and under control. As we explore GravityZone Content Control in this brief, you'll see how it has become an essential part of modern cybersecurity.
The Importance of Host-Based Content Control
The rise of hybrid and remote work models has further compounded the complexity of the digital landscape. With data frequently traversing between cloud-based infrastructures, on-premises servers, and remote devices, the traditional perimeter-based security model has proven insufficient. Host-based content control transcends these perimeter limitations, offering granular security right at the source, regardless of the device's geographical location or the network it's connected to. This not only boosts an organization's cybersecurity posture but also provides the flexibility essential for today's dynamic work models.
Given the nature of current cyberthreats, organizations must have the capacity to limit the users’ ability to access certain websites. When users access websites on their devices without filtering for malicious content, they expose themselves and their organizations to a myriad of risks. Malicious websites often host malware, exploit kits, phishing schemes, and ransomware, which can be designed to surreptitiously install on a user's device. Once compromised, the device can be used to harvest sensitive information, launch attacks on other systems, or be held hostage for ransom. Furthermore, the infection can propagate across connected networks, magnifying the damage exponentially. Such exposure not only threatens the confidentiality, integrity, and availability of data but can also result in significant financial costs for mitigation and recovery, reputational damage, and potential legal consequences.
Accessing certain websites, particularly those that feature content such as pornography, warez (pirated software), narcotics, and other undesirable material, presents multifaceted risks to businesses.
Productivity Concerns: First and foremost, employees who frequent such sites during work hours divert their attention away from their primary job responsibilities, leading to decreased productivity. The distraction can also have a ripple effect, disrupting the workflow of teams or projects.
Malware and Cybersecurity Threats: Many of these questionable sites often host malware or are laden with malicious ads. When accessed from a work device, there's a heightened risk of introducing malware into the corporate network, potentially compromising business data and critical systems.
Phishing: Employees accessing suspicious websites also put your company at increased risk of phishing. Clicking on suspicious links or interacting with malicious content on such sites increases the likelihood of falling victim to phishing attacks, compromising confidential data, and potentially allowing unauthorized access to corporate systems.
Reputational Risk: If employees are found accessing or downloading illegal or unethical content on company time or using company resources, it can tarnish the organization's reputation. Such actions may be viewed as a reflection of the company's culture or oversight, even if they are the acts of individual employees.
Legal and Compliance Risks: Accessing or distributing copyrighted material (like warez) illegally can result in severe penalties for the company. Similarly, involvement, even inadvertently, in sites promoting narcotics or other illegal activities, can draw unwarranted legal attention, leading to investigations, fines, or lawsuits.
Deep and Dark Web Threats: While the deep web and dark web are vast and not entirely malicious, they contain segments that are notorious hubs for illegal activities, from trading stolen data to orchestrating cybercrimes. Allowing users unrestricted access to these areas can put the company's data at risk, especially if employees unintentionally stumble upon or engage with malicious actors. Furthermore, merely accessing some parts of the dark web can raise red flags with law enforcement or security agencies, which could lead to unwanted scrutiny.
In essence, beyond the immediate dangers of malware and cyber threats, unauthorized access to certain websites and parts of the web poses significant risks to an organization's productivity, reputation, and legal standing. It underscores the importance of effective web content filtering and cybersecurity awareness training for all users.
Controlling Application Access
Application Blacklisting and Whitelisting are two proactive approaches to application and software management, both playing pivotal roles in bolstering cybersecurity posture. They serve as gatekeepers, dictating which applications can execute on a system and which ones cannot.
Application Blacklisting:
In the blacklisting approach, an organization maintains a list of applications and software that are prohibited from being executed or installed. All applications not on this list are permitted to run by default.
Pros: Blacklisting is beneficial in environments where a variety of software needs to be run and it's hard to account for all of them. Only known malicious or unsuitable applications are restricted.
Cons: It can be reactive rather than proactive. As new malicious applications emerge daily, the list needs constant updates to remain effective. An application that is not yet recognized as malicious could potentially be executed.
Application Whitelisting:
Conversely, in the whitelisting approach, only a predefined set of approved applications are allowed to run. Any software not on the whitelist is prohibited by default.
Pros: Whitelisting offers a tighter security grip. Since only pre-vetted applications can run, it dramatically reduces the risk of malicious software execution, even if it's a zero-day threat.
Cons: It demands rigorous management, especially in diverse environments. Any software update or new tool required by an employee would need vetting and addition to the whitelist.
Importance to Organizations:
Both security controls have distinct benefits in helping to improve an organization’s security posture:
Enhanced Security: Both methods provide an additional layer of security, preventing the execution of malicious applications. This is crucial in defending against malware, ransomware, and other software-based threats.
Regulatory Compliance: Some industries or regulatory frameworks demand stringent application controls, making whitelisting or blacklisting a compliance necessity.
Controlled IT Environments: They allow IT departments to have better control over the software landscape in the organization. This can lead to more stable system configurations, easier troubleshooting, and reduced software conflicts.
Reduced Attack Surface: By controlling which applications can and cannot run, organizations limit potential entry points or vulnerabilities that attackers might exploit.
Cost Efficiency: Preventing malware infections or unauthorized software installations can result in long-term cost savings by avoiding data breaches, system downtimes, or IT resource drains in troubleshooting and system cleanups.
Employing application control across an organization can significantly enhance an organization's defense against proliferating cyber threats.
Taking Control with GravityZone
Included as part of the core features of Bitdefender GravityZone for Windows and Mac systems are various tools that allow organizations to gain control of what websites their users are allowed and not allowed to visit, what applications can and cannot run on the endpoints, and protections for data transfers over HTML and SMTP protocols.
GravityZone Web Content Filtering
Bitdefender GravityZone includes formidable tools that enable organizations to take control of what sections of the world-wide web their users are exposed to, and when. We’ve already discussed the dangers of users exposing their systems to websites containing subjects such as software piracy, pornography, narcotics, and other unscrupulous content, however, time wasters such as online dating and social media sites can also have a significant detrimental impact on the productivity of employees. With GravityZone content control, businesses can eliminate the dangers posed by this type of behavior by scanning both HTTP and HTTPS (after enabling Intercept Encrypted Traffic) traffic in the service of adhering to the organization’s content control rules.
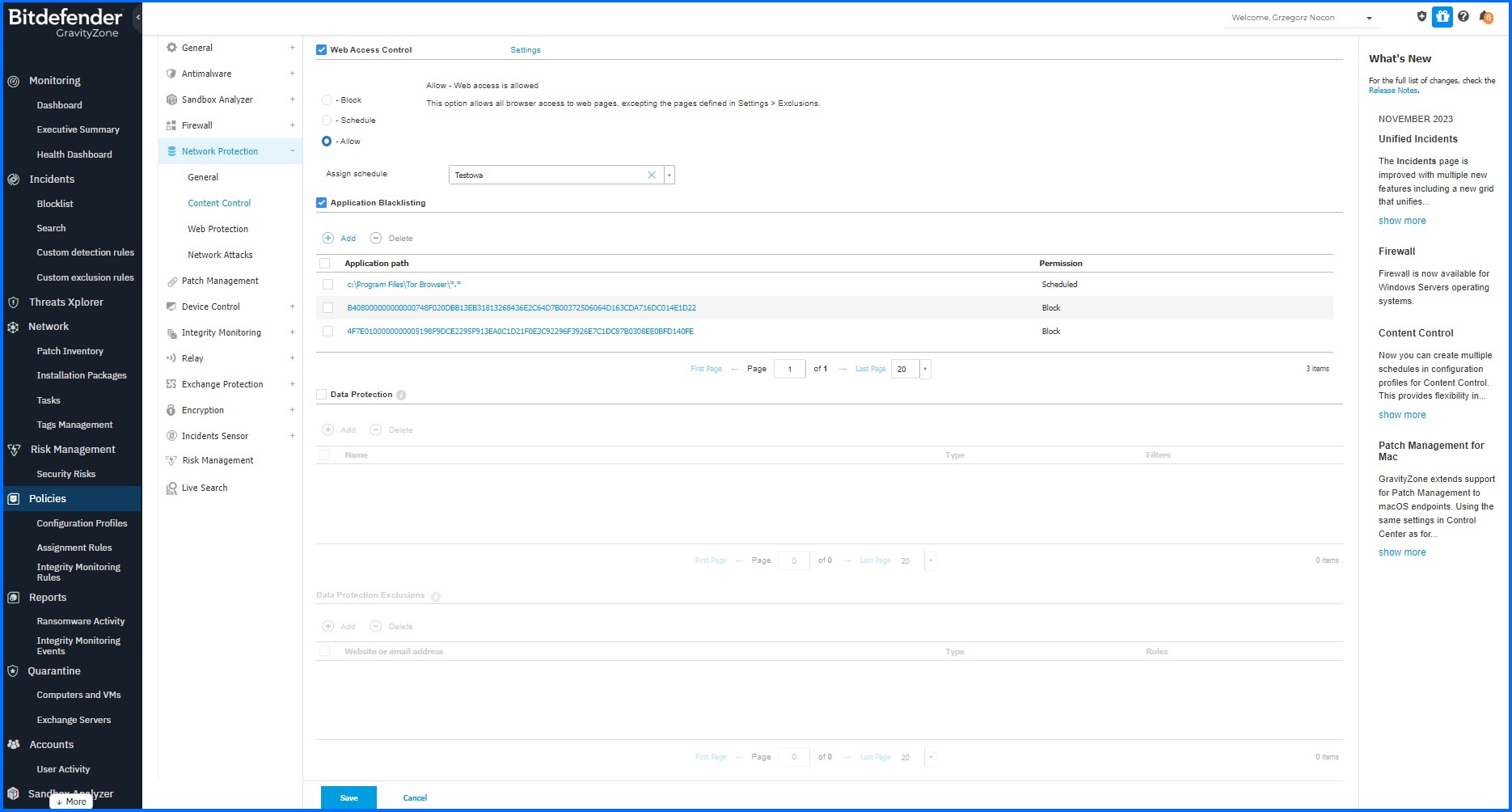
Figure 1: GravityZone Web Content Filtering allows organizations to limit users from visiting websites that can compromise the security and reputation of the business
Configuration
Web control filtering can be configured in two simple steps. Firstly, configuration requires defining a profile, which can be configured through the Web Access Control Scheduler. Each profile can be linked to a single scheduler, which can include up to 10 sub-schedules, allowing administrators to configure more granular policies.
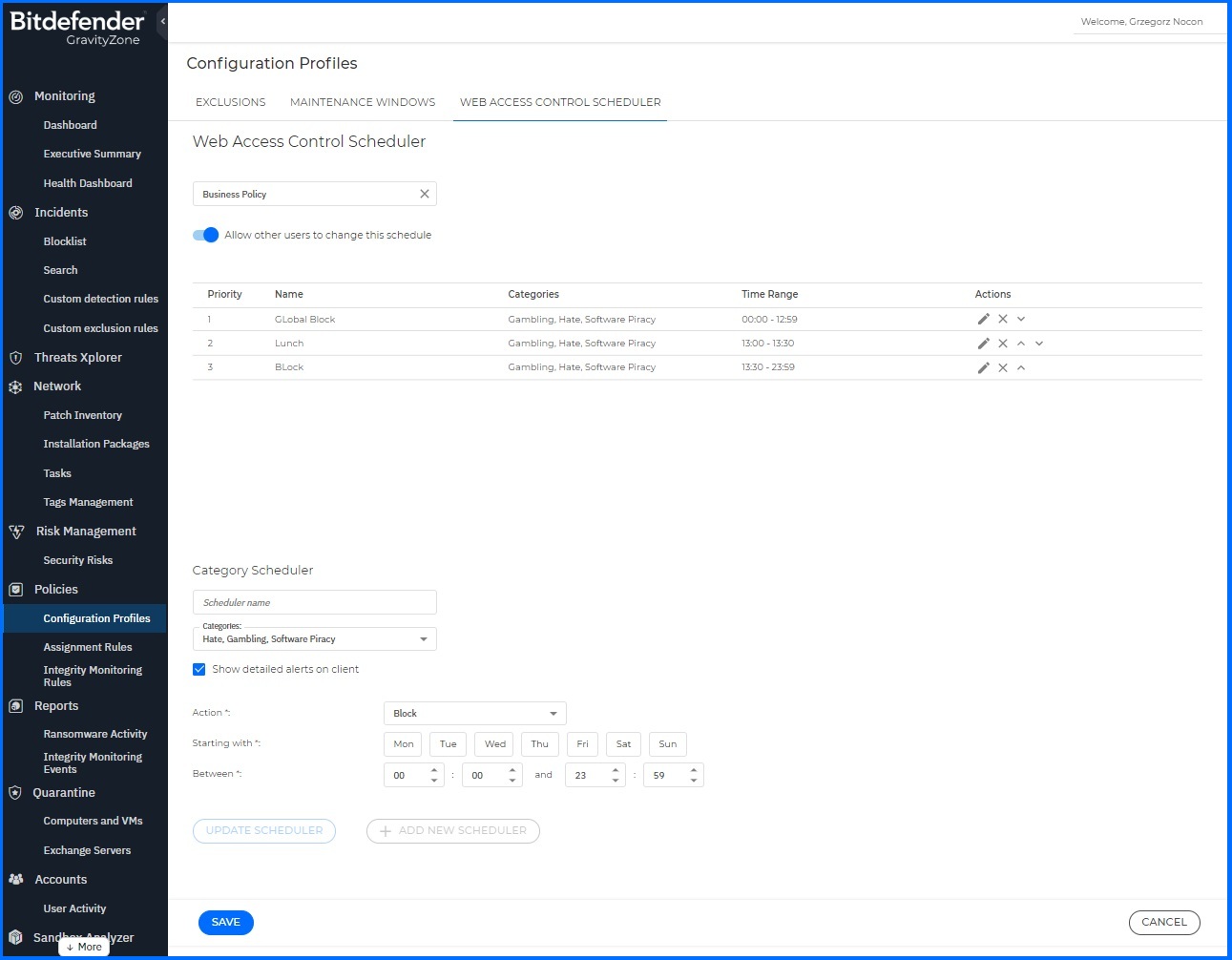
Figure 2: GravityZone web access control scheduler allows organisation to create more granular profiles
Under scheduler configuration, administrators can define:
Categories: Allow security teams to choose website categories.
Action: Allow security teams to decide whether to Allow, Warn the user, or Block traffic.
Time Range: Allow security teams to determine specific days and times.
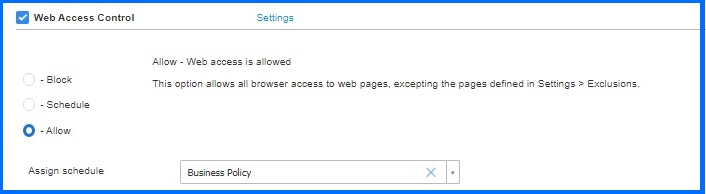
The second step is to simply assign the created profile in the policy under Content Control configuration settings.
Users who visit a blocked site will be greeted with a warning that the site violates the company’s security policy or a message in their browser that the site was blocked by Bitdefender. The message they receive is in accordance with their company’s security policy configured in the GravityZone console. GravityZone’s host-based solution makes it ideal for the modern era of remote/hybrid work, as it keeps laptops protected even when they are not connected to corpnet, allowing the security to extend beyond traditional perimeter defenses.
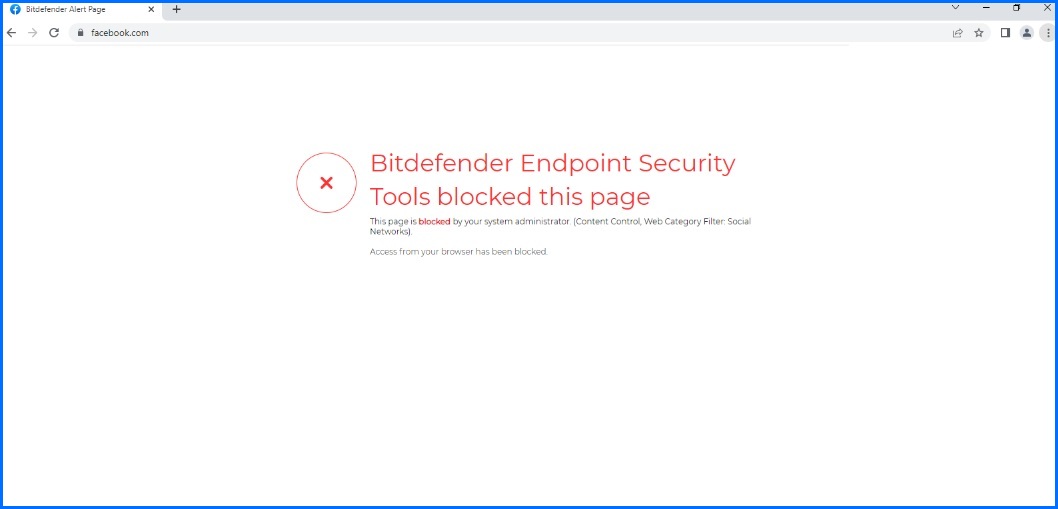
Figure 3: GravityZone web content filter at work, preventing the user from accessing a blocked Social Network site.
Detailed information about Web Access Control configurations can be found at our Bitdefender Support Center here.
GravityZone Application Control
There are two version of application control available with GravityZone for Windows systems: Application Blacklisting is available with both the on-premises and cloud versions of the console, while Application Whitelisting is only available with the on-premises version of GravityZone.
GravityZone Application Blacklisting
Application Blacklisting allows security teams to prevent specific applications from launching on endpoints. Once again, these settings are controlled through the flexible GravityZone policies. Security teams can easily define what applications are allowed to run on their endpoints by specifying the full path or simply the name of the application executable.
Using the Access Scheduler, organizations can further refine their Application Control by specifying specific days during the week and times when the application will be prohibited from running. For example, if an organization does not want their users accessing Spotify on their endpoints during business hours only, but have no issues with the users accessing the application after working hours, they can easily configure these settings in the GravityZone policies.
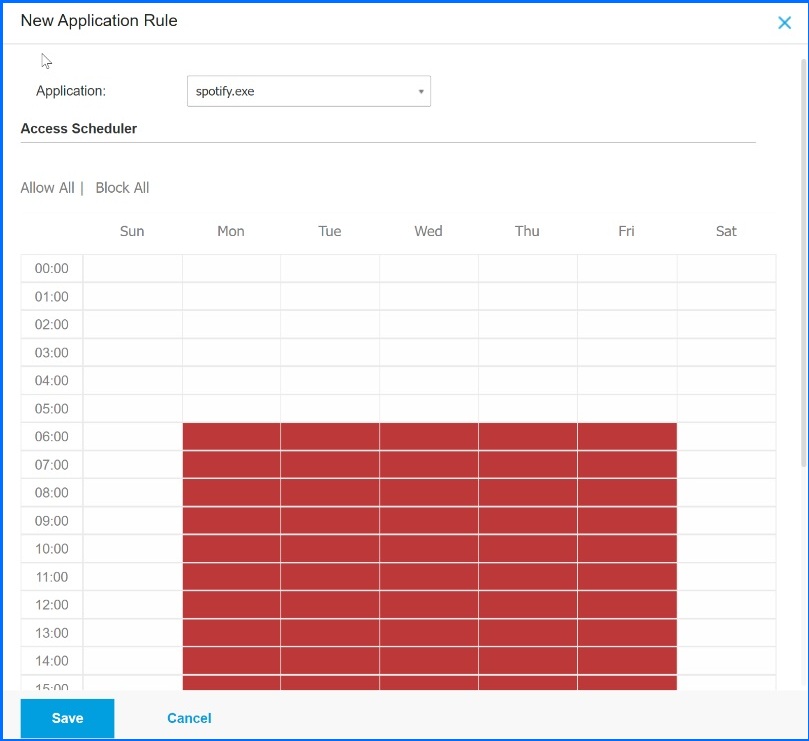
Figure 4: With GravityZone Application Blacklisting, organizations can block unwanted programs from running on their endpoints, and set a schedule to reduce the possible negative impact on productivity.
GravityZone Application Control
Included with the on-premises version of GravityZone are controls that permit an organization to prevent the installation and execution of any unwanted, untrusted or malicious applications. GravityZone Application Control can serve as a powerful augment to any zero-trust configuration.
Application Control in GravityZone’s on-premises version exists as its own separate section in the policies, instead of existing within the Network Protection section of the policies like it does in the Cloud version of GravityZone. Application Control on-premises begins with a discovery task which scans the running applications and processes on the organization’s systems that have Bitdefender GravityZone Endpoint Protection installed. There are two different modes Application Control whitelisting capabilities can run on:
Test Mode: Application Control only detects and reports the applications in Control Center, leaving them to run as usual. You can configure and test your whitelisting rules and policies, but applications will not be blocked.
Production Mode: Application Control blocks all unknown applications. Microsoft operating system processes and Bitdefender processes are whitelisted by default. Defined whitelisted applications will be allowed to run. To update whitelisted applications, you must define updaters. These are specific processes that are allowed to change existing applications. Detailed information can be found at our Bitdefender Support Center here.
Through the GravityZone policies, security teams can specify the application rules based on hash of the executable, signing certificate thumbprint, and path of the application. Wildcards can also be used to define entire directories where applications can be prohibited, or exclusively allowed to run from. Security teams can also include subprocesses and define exclusions. For example, if an organization wanted only one executable to be allowed to run from a specific directory but block any other that doesn’t match a specific hash, they can easily accomplish this with GravityZone Application control. As with all GravityZone policies, these rules can be applied to individual machines, groups, or users, allowing for robust flexibility.
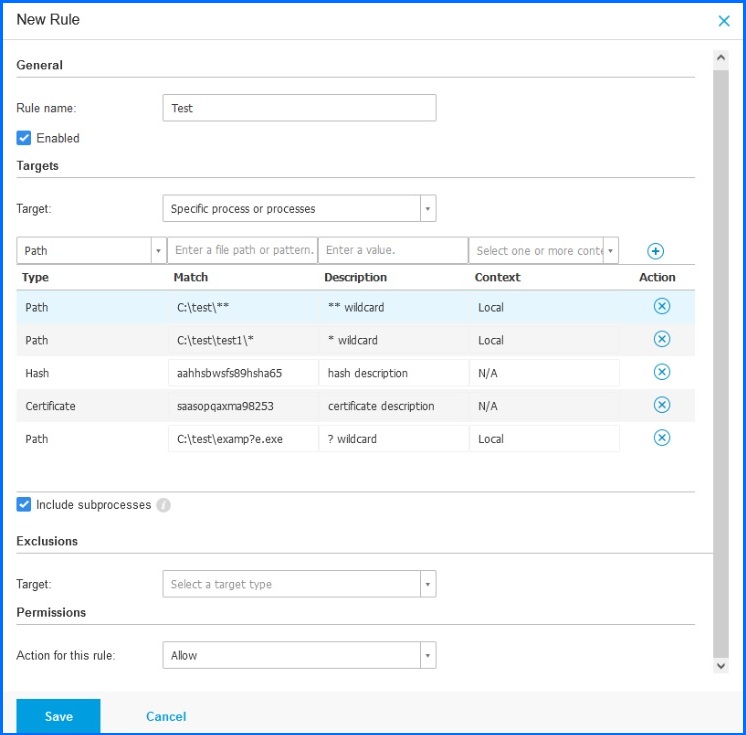
Figure 5: With Application Whitelisting, organizations can easily define the specific applications that are allowed to run on their endpoints.
Detailed information about Application Control can be found at our Bitdefender Support Center here.
GravityZone Data Protection
GravityZone Data Protection employs rule-based mechanisms, defined by system administrators, to safeguard sensitive data against unauthorized access and disclosure. This module provides a straightforward configuration that allows the scanning of sensitive content that is being transmitted via HTTP and SMTP traffic.
Using a simple set of rules, security teams can protect several different categories of information including addresses, bank account numbers, credit card numbers, email addresses, names, passwords, PINs, Social Security Numbers, and telephone numbers. In the event that a user attempts to transmit the information defined in the rule through an unsecured HTTP connection (such as an unsafe web form), or tries to send it via an unguarded SMTP email, GravityZone will block the information from being successfully transferred. Additional details on GravityZone Data Protection module can be found in the GravityZone Support Center.
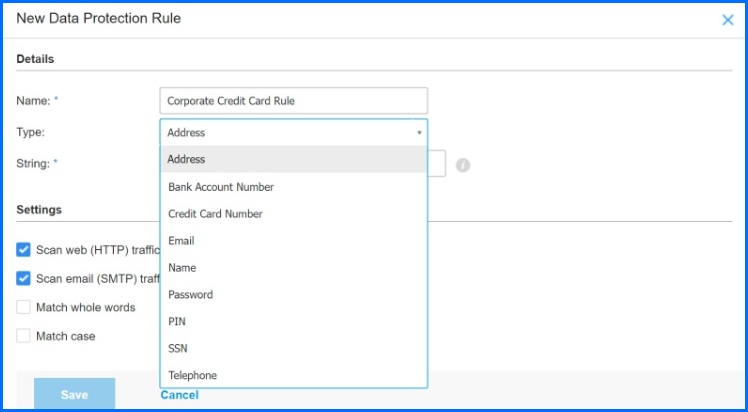
Figure 6: GravityZone’s Data Protection rules allows organizations to prevent sensitive data from being transmitted through unsecured HTTP and SMTP traffic.
A Powerful Consolidation of Security
In the modern cybersecurity landscape, GravityZone Content Control stands out not just as a defensive mechanism but also as a means to consolidate security tools, streamline operations, and eliminate redundancies. Conveniently governable from the same console that controls the organization’s antimalware, network protection, risk management, patch management, integrity monitoring, and more, GravityZone helps eliminate the burden of having to juggle multiple security solutions.
Firewall
Firewall functionality for Windows servers and workstations gives the administrators the capacity to control network traffic. Granular control over the services and applications that can communicate enhances security by restricting access to only necessary and trusted sources. Bitdefender is using its technology instead of managing the existing Windows Firewall. This approach provides us with the additional capability to add scanning functions, such as port scanning, which are unavailable when using the embedded Windows Firewall. Port scans are frequently used by hackers to identify open ports that can be exploited for vulnerabilities in the application responsible for the open connection.
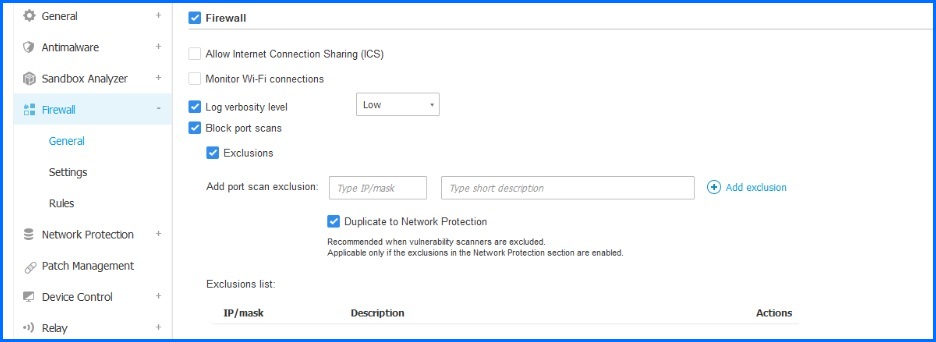
Bitdefender GravityZone Firewall general configuration.
Firewall configuration
The functionality of the Firewall relies on network profiles, which are based on trust levels. An administrator should start his configuration by defining the trust using predefined network profiles:
Trusted - Disables the firewall for the respective adapters. The traffic is allowed and not filtered.
Home/Office - Allows all traffic to and from computers in the local network while the other traffic is being filtered.
Untrusted - Completely blocks network and Internet traffic through the respective adapters.
Administrators may want to change the default profiles assignment if they want to have more granular control and for example filter mac addresses. By default, L2 filtering is disabled in the Trusted and Home/Office profiles and available in the Public one. Profiles need to be assigned to each network and can be defined in the Settings tab in the Network section. When the Firewall detects a new connection, compares the adapter information for that connection with the information from the existing profiles, and applies the correct profile.
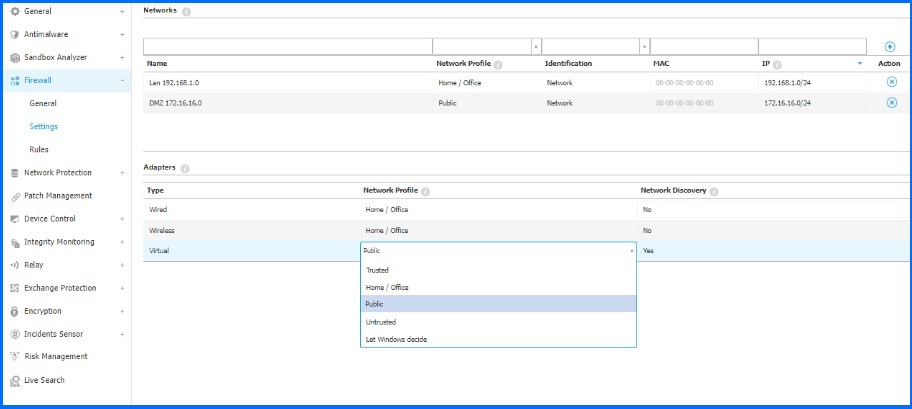
Bitdefender GravityZone Firewall Networks and Adapters configuration.
If a network that is not defined in the Networks table is detected, the Bitdefender security agent identifies the network adapter type and applies a corresponding profile to the connection. The Bitdefender security agent can detect three predefined Adapters: Wired, Wireless, and Virtual (Virtual Private Network).
Administrators can define profiles for each adapter or choose “Let Windows decide”, which means the Bitdefender security agent applies a profile for the firewall based on the network classification in Windows. If the detection based on Windows Network Manager fails, basic detection is attempted, using a generic profile where the network profile is considered Public.
Detailed information about Firewall configurations can be found at our Bitdefender Support Center here.
Rules configuration
For more granular control, administrators can define application and connection rules that specifically apply to the Home/Office and Public profiles. They have the flexibility to edit, disable, and delete predefined default rules in the policy or create their own new rules. This allows them to tailor the firewall settings to meet specific requirements, providing enhanced protection for user computers and servers against unauthorized inbound and outbound connection attempts.
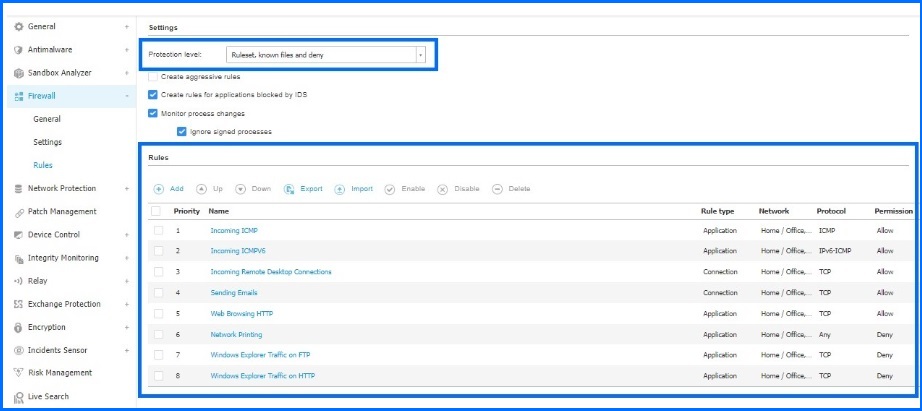
Bitdefender GravityZone Firewall Rules configuration.
Administrators benefit from a large collection of safe, trustworthy applications compiled and continuously maintained by Bitdefender. In the case of servers, it is recommended to create additional rules allowing traffic for services depending on the server's role. The rules have been described in our GravityZone Support Center here.
The Protection Level defines the firewall decision-making logic used when applications request access to network and internet services. Administrators can choose whether to use only predefined rules or to also recognize applications and determine the action to be applied, between allow, ask, or deny. For example, by choosing the ‘Ruleset, known files, and deny’ option, the firewall applies existing rules, automatically allowing connection attempts made by known applications, and automatically denying all other unknown connection attempts. Detailed information about configurations can be found at our Bitdefender Support Center here.
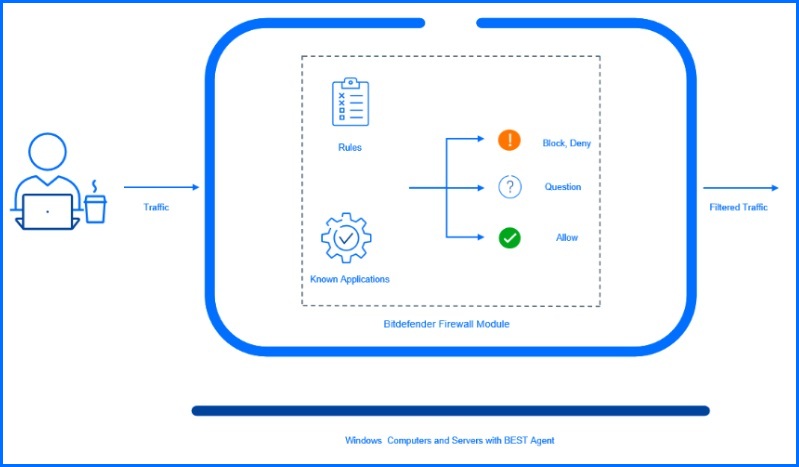
It is worth noting that the Firewall module includes one embedded, unmodifiable, and hidden rule responsible for allowing management traffic between GravityZone and the BEST agent. This rule enables endpoint management regardless of any new rules an administrator creates. For example, if they accidentally create a rule to block any incoming or outgoing traffic to the GravityZone management server.
Endpoint Isolation during an incident
When an endpoint is involved in an incident detected by Endpoint Detection and Response (EDR), the administrator might want to prevent that endpoint from spreading the threat to the rest of the network. Isolation is designed to restrict an endpoint's connectivity by using internal firewall module, and only Endpoint services are allowed to communicate with GravityZone. The endpoint can still receive updates and send events to the console but is restricted from potentially infecting the rest of the network. After being added to isolation, the endpoint can be removed if it is determined not to pose a threat anymore.
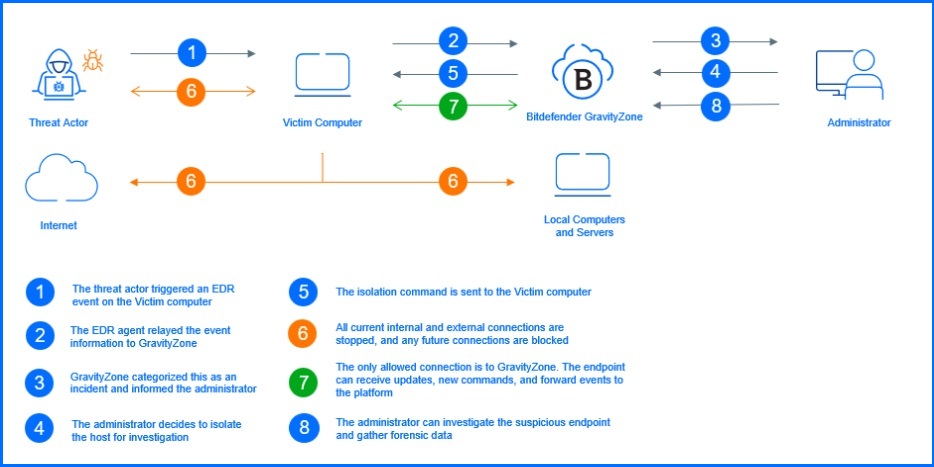
On different operating systems, we use different isolation mechanisms. On Windows computers, we are using embedded firewall; for Linux machines, we use embedded iptables, and on macOS computers, we utilize an internal traffic interception extension that functions like a regular firewall.
Implementation best practices
During firewall configuration, careful planning is necessary, and it is important to remember that no two networks or organizations are the same, and there is no one-size-fits-all set of rules. Before implementing the firewall, the administrator should at least take the following into consideration:
While multiple firewalls can run on one machine, it is recommended to keep only one firewall active at a time. On all machines where Windows Security Center is enabled, the internal Windows firewall will be disabled by default after Bitdefender Firewall installation and registration in the system. If the Group Policy configuration enables it again, Bitdefender Firewall can't disable it again. The local firewall has to be disabled manually, and the GPO policy modified. On systems where Windows Security Center is turned off, the local firewall can't be disabled by Bitdefender and should be disabled by the administrator first. Having more than one firewall on a machine can cause conflicts and problems, such as issues with prioritization and the order of processing.
It is recommended to create at least a separate configuration profile for workstations and for servers. For the server profile, we recommend adding the firewall rules available here.
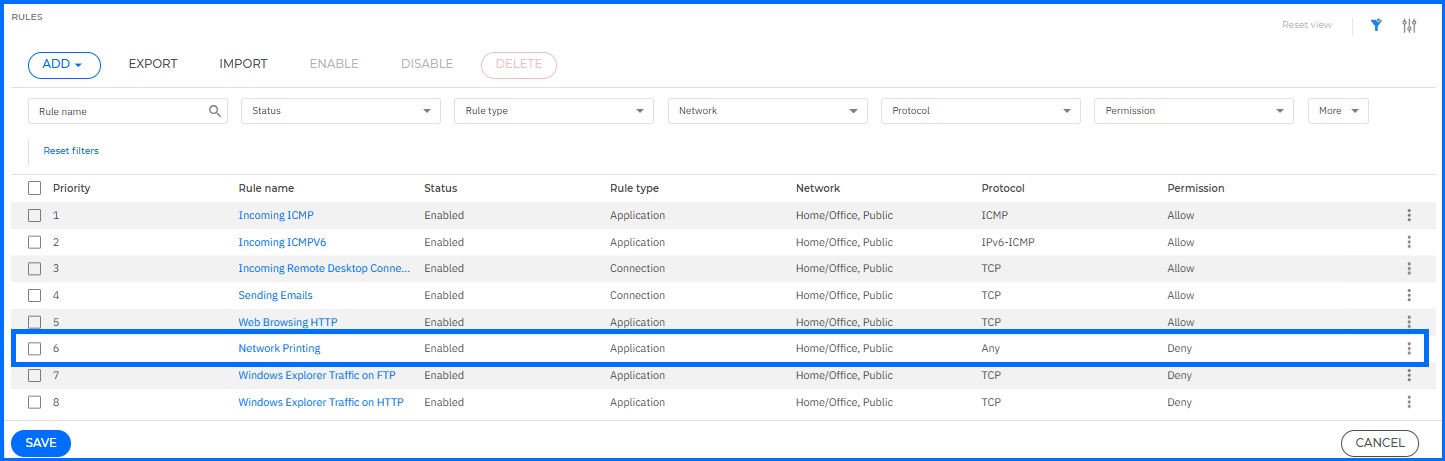
By default, Bitdefender Firewall includes a Network Printing rule. This rule is designed to deny access to printers located in a different local area networks. If your network environment has printers that users need to access, it is critical to manually edit this rule to allow for network printing in the required networks. The configuration video is available our GravityZone Support Center here.
Depending on the server's role, it is necessary to create a dedicated set of rules allowing traffic for specific services. The recommended set of rules is available in our GravityZone Support Center here
When the administrator wants to migrate their rules from the existing firewall, this is a good opportunity to conduct an audit to check for redundancies and errors, and consistently omit unnecessary rules before implementation. Migration can be done by using a CSV file. The administrator can simply export rules from their existing configuration, parse it, and import it into the Bitdefender Firewall configuration. Information on how to use a CSV file is available in our GravityZone Support Center here. For example, to export Windows Defender Firewall rules from a server to CSV format, administrators can use the 'Get-NetFirewallRule' PowerShell command (more information is available here), or he can do it directly from Inbound/Outbound Rules configuration using Export List option.
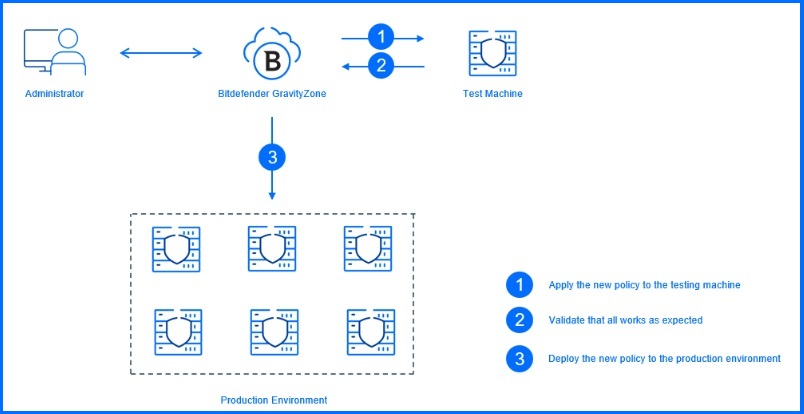
For example, after creating the server firewall policy, test servers should be assigned to that policy. After enabling the firewall configuration on these test servers, the administrator must test the new policy. It is crucial to remember that the rules are checked from top to bottom. When all the tests are done with acceptable results, the server firewall policy can be assigned to production servers.
It is worth noting that port scans or creating a high number of rules may create additional load on the CPU. Therefore, we recommend avoiding any 'deny/allow default actions' because for each new connection attempt, a new rule is created and added to the ruleset. To prevent the creation of new rules, we recommend manually creating rules based on specific configurations to deny or allow all traffic at the bottom.
Recommended Content
To learn more about the technologies behind the Protection layer, we recommend reading the next article Protection.