Device Control - Bitdefender Techzone
Bitdefender Device Control: Prevent data leaks & malware via external devices. Granular policy management & exceptions. Monitor user behaviour, manage device access, and prevent breaches.
External devices can serve as channels for data exfiltration. Unauthorized users may copy sensitive data onto USB drives or other storage media and remove it from the secure organizational environment. USB and Bluetooth devices can also be exploited for unauthorized access to systems. For instance, attackers might use a prepared flash drive to swiftly execute malicious code on a computer.
Bitdefender's defence-in-depth security architecture employs multiple layers to minimize the potential for cyber-attacks. At the core of this comprehensive security approach lies prevention, a critical first line of defense that aims to stop attackers from identifying or exploiting vulnerabilities within the secure infrastructure.
Within Bitdefender GravityZone, the Device Control functionality plays a vital role in preventing sensitive data leakage and malware infections through external devices connected to endpoints. By utilizing blocking rules and exceptions configured through policies, a wide range of device types can be effectively managed. This control extends beyond USB flash drives, encompassing Bluetooth devices, CD/DVD players, storage devices, and more. Consequently, organizations have the flexibility to design device control strategies tailored to the specific needs of their devices.
Device control offers valuable information, including visibility into which users are employing specific devices on endpoints and control over whether and how external devices can be utilized.
Device Control operation
The Device Control policy in the GravityZone console can be precisely managed with granular rules and exclusions available out of the box for the administrator.
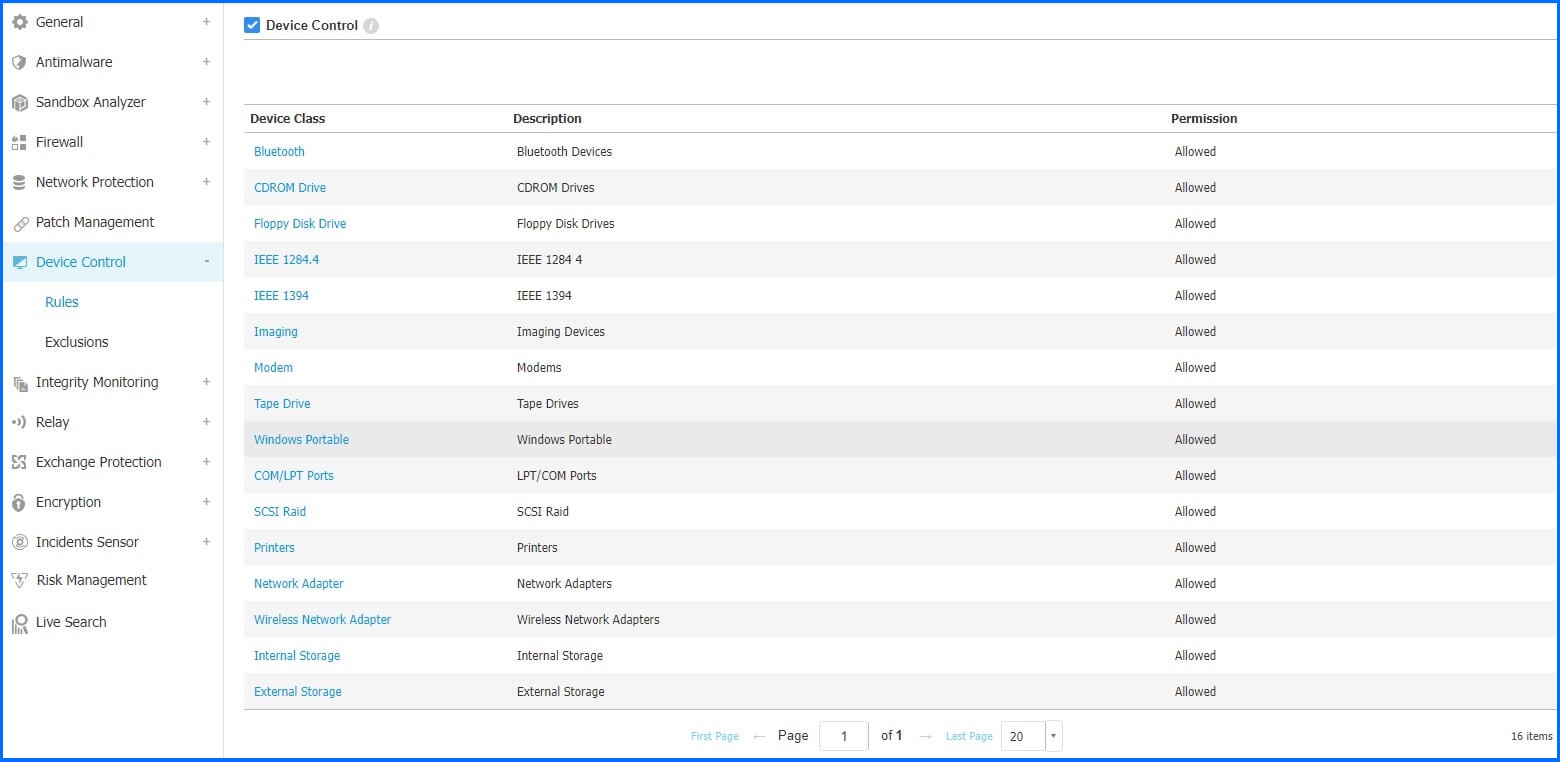
Device Rules can establish two types of permission policies: standard rules and exception rules:
Rules: Permissions based on device type and connection type.
Exception Rules: Permissions based on Device ID or Product ID.
For devices, the first match from the list of rules will be applied as the governing rule. It is essential to prioritize exception rules initially. The Mac implementation is designed to align with the Windows rules and exceptions, following a best-match approach.
Kindly be aware that we cannot instantly block devices that are mounted during boot time (e.g., CD-ROM). After installing the product, a system restart is necessary. Only then will we be able to control the access of those devices effectively.
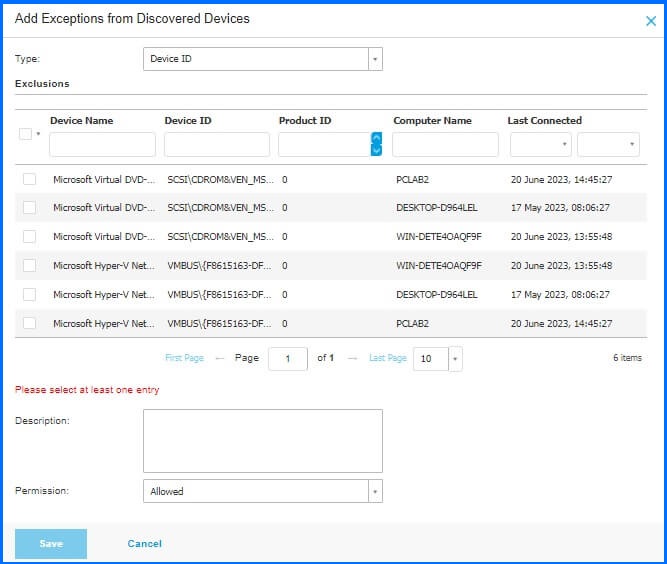
In the policy section, discovered devices serve as the basis for adding exclusion rules. When adding an exceptions policy, the administrator can select devices from the list or add the device manually based on Device ID or Product ID. Moreover, users have the option to filter devices based on various criteria, including Device ID, Product ID, last connected date, and endpoint name.
Administrators can set unique exceptions for a single device using Device ID. Alternatively, Product ID applies exceptions to all devices of the same type from one manufacturer. However, some customers may find Product ID missing, notably in budget devices.
Detailed information about device control configurations and a list of supported device types can be found at our Bitdefender Support Center here.
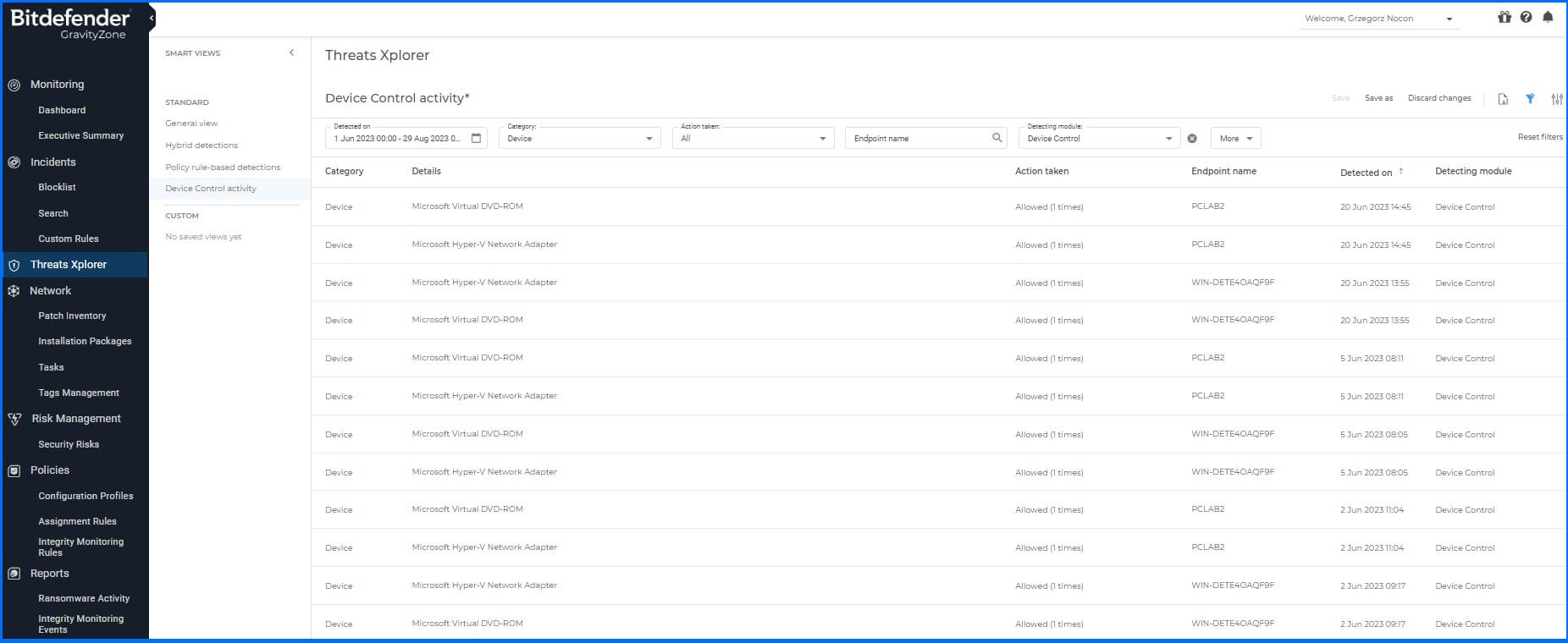
Not only rules play a crucial role but also the visibility of administrative actions and user behavior. For instance, reports can help detect unauthorized device usage by monitoring how users interact with the system. The primary report displays a comprehensive list of all endpoints accessible to the user, along with counters indicating the number of devices that have been allowed, blocked, or set as read-only. The second one can be opened by clicking on the counters and displays the list of events for the selected device and status.
Detailed information about managing permission rules and exclusions can be found at our Bitdefender Support Center here.
Recommended Content
To learn more about the technologies included in the Prevention layer we recommend reading the next article Application Control.
More resources
Bitdefender GravityZone Platform official website: Bitdefender GravityZone Platform official website