Cloud (CSPM+) - Bitdefender TechZone
Bitdefender Cloud Security Posture Management Plus (CSPM+) helps organizations manage the secure and compliant configuration of cloud resources and services. Verifies user identities and access permissions within the cloud environment to find over-privileged identities.
Cloud service providers used a concept named the Shared Responsibility model. It means that cloud providers are responsible for ensuring the security of the cloud infrastructure and services, including the underlying hardware, network, and software components. At the same time, customers are responsible for securing their data, applications, identity access management, and configurations within the cloud environment. What used to be the sole responsibility of the customer in an on-prem environment is now split between customer and cloud service provider responsibility.
Cloud services provide great scalability and flexibility to significantly enhance operational efficiency but also introduce potential risks related to increased attack surfaces and a need for cloud security visibility. One of the fundamental cloud security challenges ensuring the configuration of public cloud resources avoids not only exposing data and systems to security threats but also complies with applicable regulatory and compliance frameworks, as well as industry best practices.
In this technical brief, we discuss how Bitdefender GravityZone Cloud Security Posture Management (CSPM+) helps organizations manage their security and compliance risks without requiring deep cloud security expertise. You will learn how to integrate with your cloud platform(s), remediate security findings, and meet security standards.
Bitdefender CSPM+
Bitdefender CSPM+ includes not only Cloud Security Posture Management (CSPM) functionality, ensuring the secure and compliant configuration of cloud resources and services to identify and mitigate potential security risks and misconfigurations, but also Cloud Identity and Access Management (IAM). The IAM – also referred to as CIEM (Cloud Infrastructure Entitlement Management) - functionality manages user identities - both human users and machine identities such as service accounts - and access permissions within the cloud environment. These integrated functionalities provide security and precise control over cloud resources, creating a comprehensive and secure cloud computing environment.
Interface
The CSPM+ management platform is a consolidated component of Bitdefender GravityZone. Access is provided through an integrated console within Bitdefender GravityZone.
Bitdefender GravityZone console
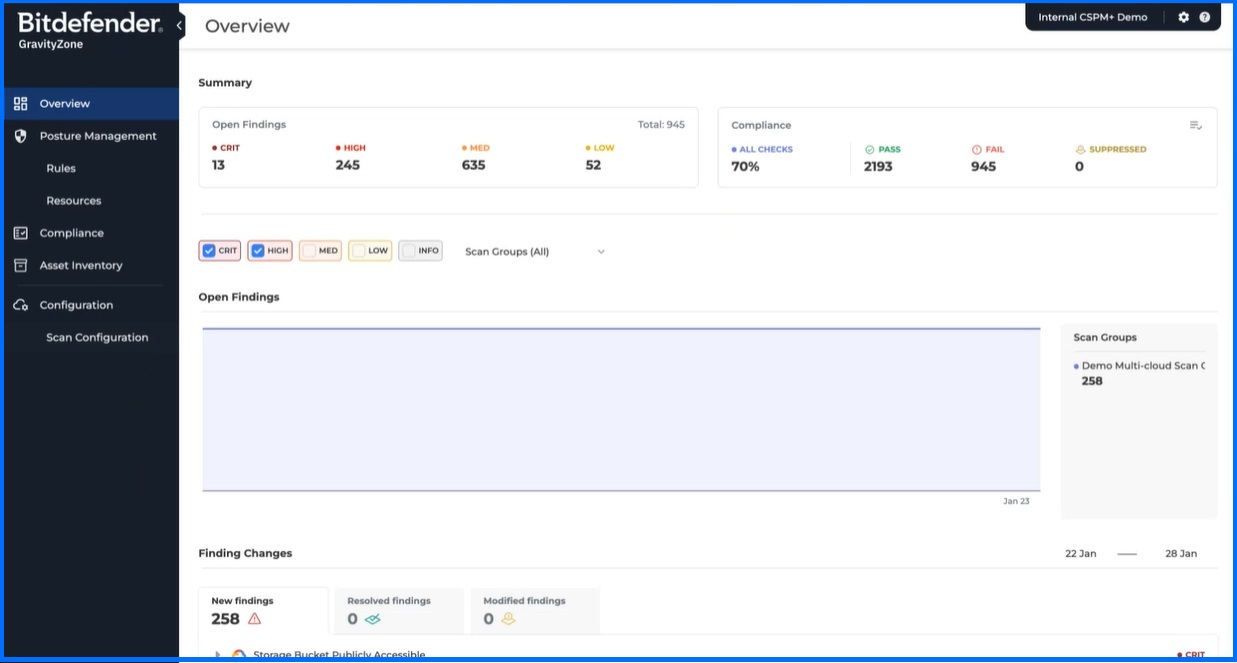
Bitdefender GravityZone CSPM+ management console.
Integration
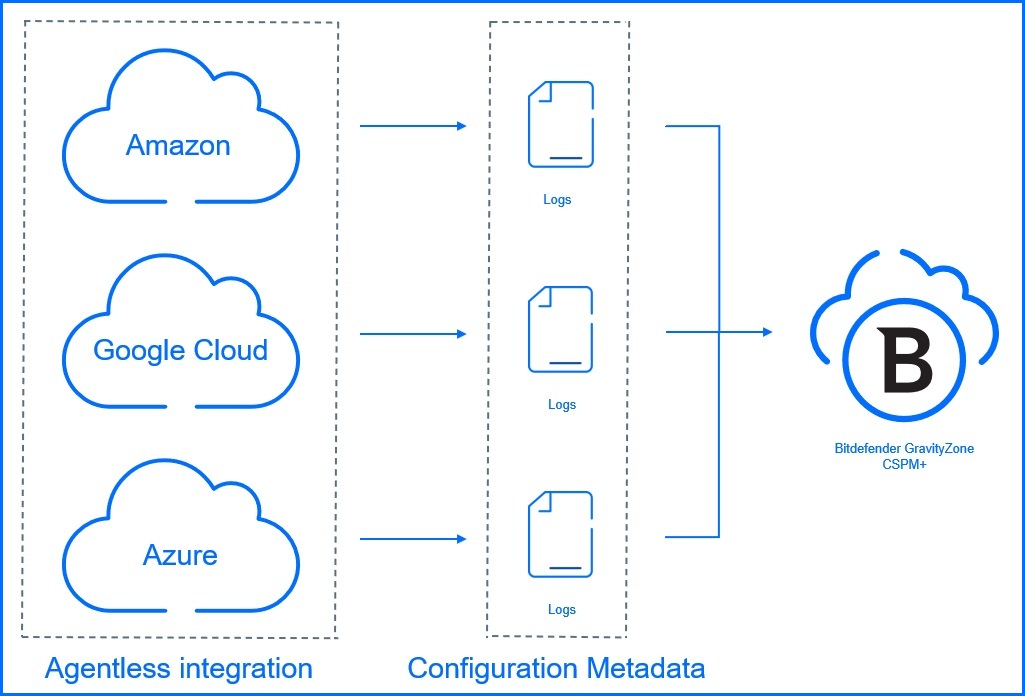
Integration enables full visibility into public cloud assets and identities on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure and Alibaba Cloud. It is an agentless integration where we only gather cloud configuration metadata for customer cloud accounts. Note that CSPM+ works with environment metadata and does not access or modify data within workloads, compute instances, or any location where data may reside. This agentless integration collects and analyzes cloud configuration metadata from customer cloud footprints. Since CSPM+ integrates directly with the cloud provider on the management plane rather than using traditional, in-workload agents, it has zero impact on workload performance.
Administrators can specify the scanning frequency for the cloud environment at the integration level, choosing between daily, weekly, or on-demand scans based on the dynamic nature of the cloud setup. The on-demand scan can be very useful when the administrator wants to verify if all the changes that were made resolve findings, otherwise, he will have to wait for another planned configuration scan. The on-demand scan is a differential scan for a particular rule and does not scan all environments.
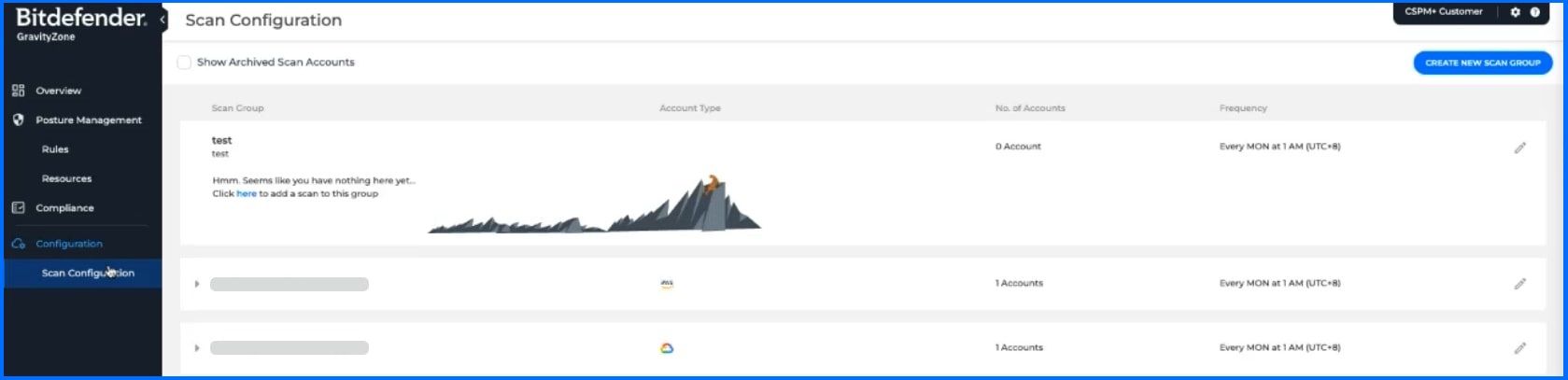
To onboard a cloud account, an administrator must configure the Scan Configuration section by following the provided steps.
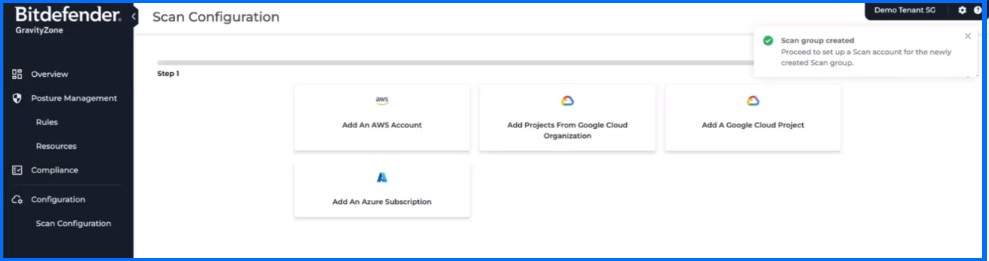
Bitdefender GravityZone CSPM+ Scan Configuration integration console
AWS integration
For AWS, administrators can automate this process using the Cloud Formation option, which is recommended, or do it manually. The Cloud Formation will create an IAM role with the necessary Security Audit permissions, and the integration takes a few minutes. The interaction between GravityZone and Cloud Provider is based on APIs. Detail configuration instructions are available in the GravityZone Support Center here.
Additionally, administrators can configure a Remediation Role ARN for One-Click Remediation which requires additional permissions described in GravityZone Support Center here. This will allow, the deletion of the access key, login profile, user, and user policy.
GCP integration
For GCP integration, administrators have at their disposal two types of integration: Organization and Project level. Both configurations must be done manually. When adding GCP Cloud Organization, the administrator gains control over the entire organization and all selected projects. With Project integration, administrators have control only over a configured project and need to remember that a new project requires a new integration. Detail configuration instructions are available in GravityZone Support Center here for Project integration can be found here, and for Organization here.
Azure integration
For Azure, administrators can initiate automated integration using the ARM Deployment option, which is recommended, or do it manually. The ARM Deployment option will create an access role (IAM) with previously assigned permissions for ‘Active Directory App Permissions’ like User.Read.All, Group.Read.All, and Application.Read.All. Detail configuration instructions are available in GravityZone Support Center here.
Bitdefender GravityZone CSPM+ with all cloud services configured
After successful integration, GravityZone CSPM+ consolidates data from all scans, providing the administrator with a high-level understanding of their cloud security posture.
Alibaba Cloud
For Alibaba Cloud, administrators can automate the deployment using RAM Policies by pasting the JSON code generated by CSPM+. The communication between Alibaba Cloud and CSPM+ is based on OpenAPI. This integration allows for streamlined policy management and secure data exchange, ensuring that your cloud security posture is continuously monitored and updated. Detailed configuration instructions and additional permissions required can be found in the GravityZone Support Center here.
Compliance
Cloud Compliance is ensured through continuous security checks of the configuration of customer public cloud resources based on security standards and regulatory compliance frameworks, such as CIS and GDPR. Currently, Bitdefender GravityZone CSPM+ supports more than 20 frameworks and regulations. It includes frameworks like CIS, PCI DSS, NIST CSF, CCM, ISO 27001, SOC2, and GDPR. Compliance can be checked by reviewing the Rules or directly from the main menu. Also, it includes a collection of best practices for cloud resources, ensuring secure configurations for elements such as identities, databases, and compute instances.
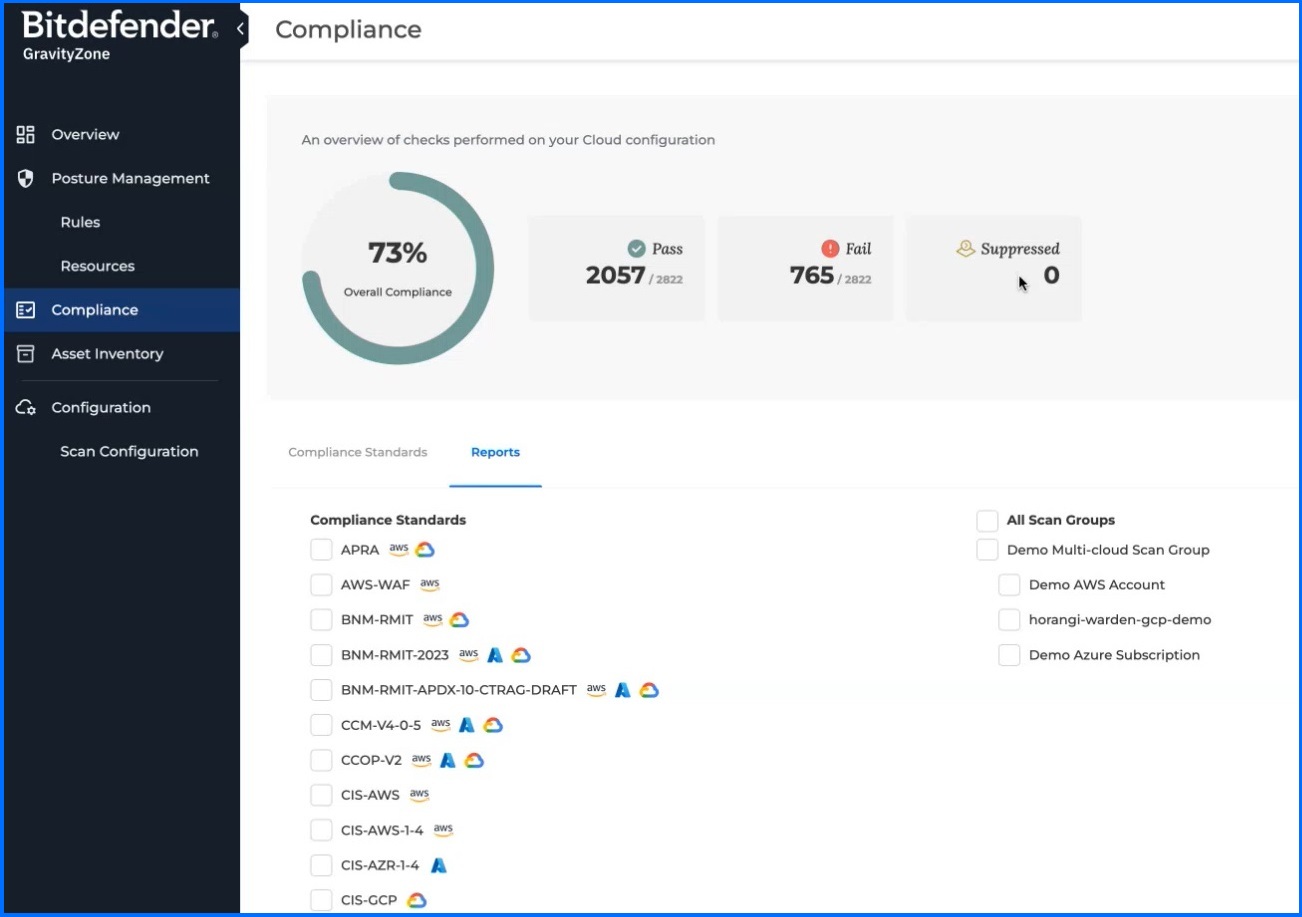
Bitdefender GravityZone CSPM+ Compliance section.
On the Compliance section administrator can check between Compliance Standards and Reports. Compliance Standards can be useful for Security Analysts, and DevOps teams to perform a quick assessment of a specific Framework or template and check what requires Remediation.
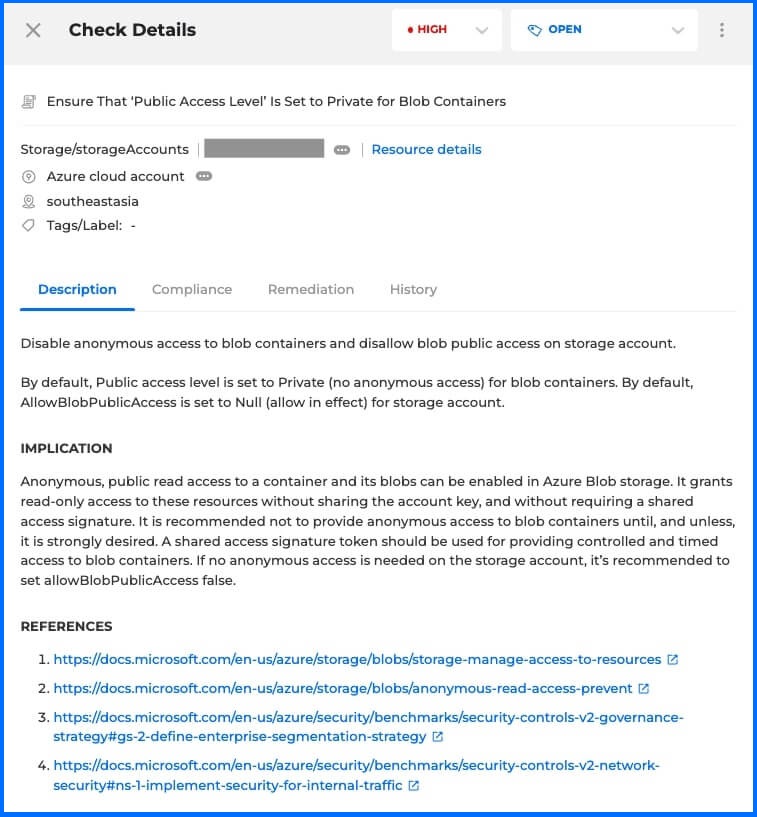
Bitdefender GravityZone CSPM+ details Description
The Reports section can generate a dedicated report that can be exported and sent to, for example, non-compliant departments or teams. Administrators can choose which compliance standards to assign to which Scan Groups. Generated reports are available as an Excel. The Reports section can generate a dedicated report that can be exported and sent to, for example, non-compliant departments or teams. Administrators can choose which compliance standards to assign to which Scan Groups. Generated reports are available as an Excel file.
Security Rules
Bitdefender GravityZone CSPM+ includes nearly 400 rules available for all cloud providers. The rules are checks conducted in a cloud environment against international/local compliance standards. It includes not only rules such as “RDS instance encryption not enabled”, “IAM Password policy” or “Compute Instance Configured with External IP” but also incorporates Security Best Practices.
The administrator can review and modify all the assigned Rules to particular Scan Groups from the Scan Configuration Menu. This allows the administrator to customize the Security Policy for each individual Account by disabling rules that may not be relevant for less critical environments or staging ones, such as backup data, and changing the Severity.
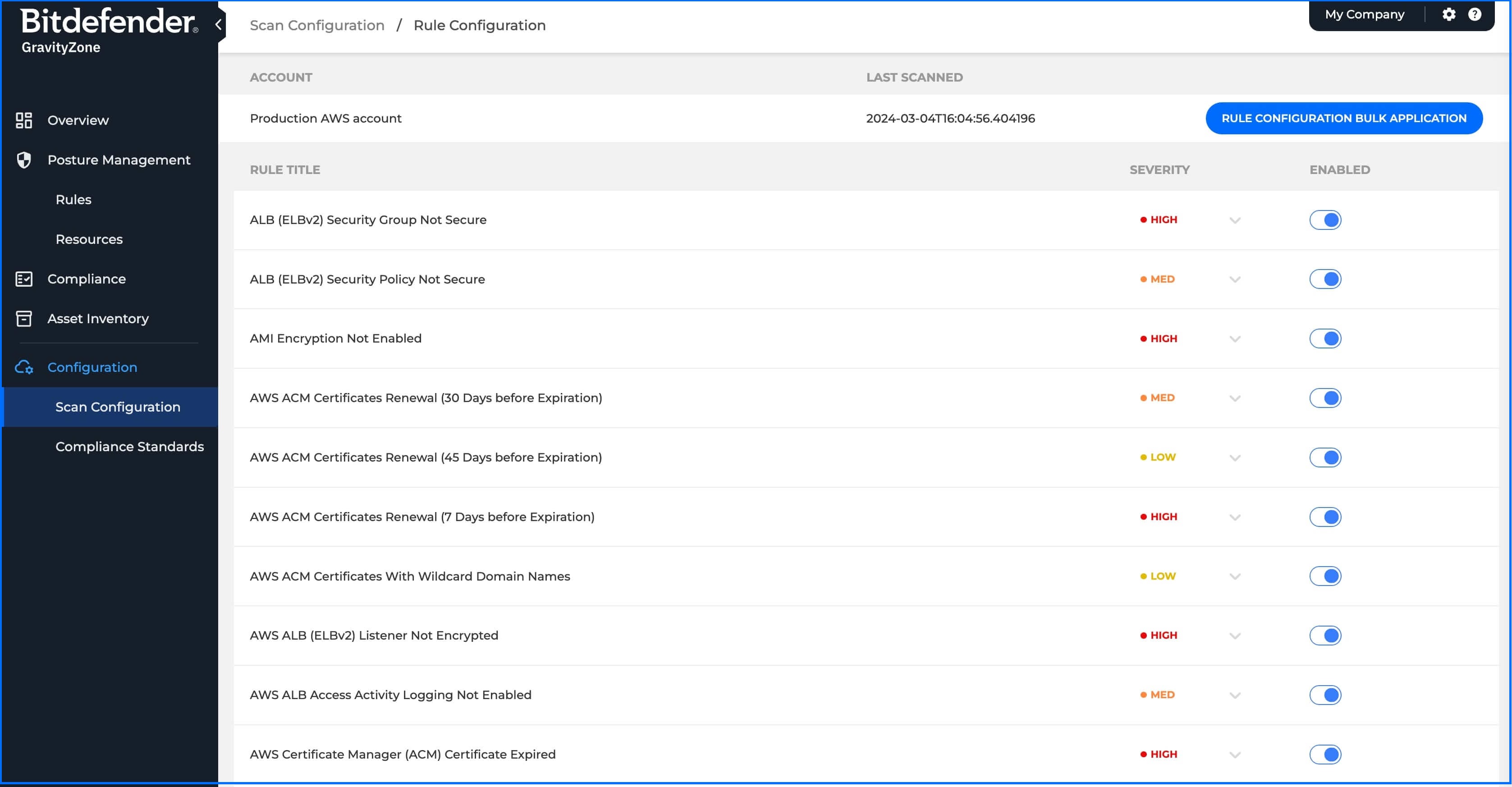
Bitdefender GravityZone CSPM+ Rule Configuration.
Rules monitor across all integrated multi-, hybrid-cloud environments and consolidate results into a single dashboard available for Security teams in the Rules section.
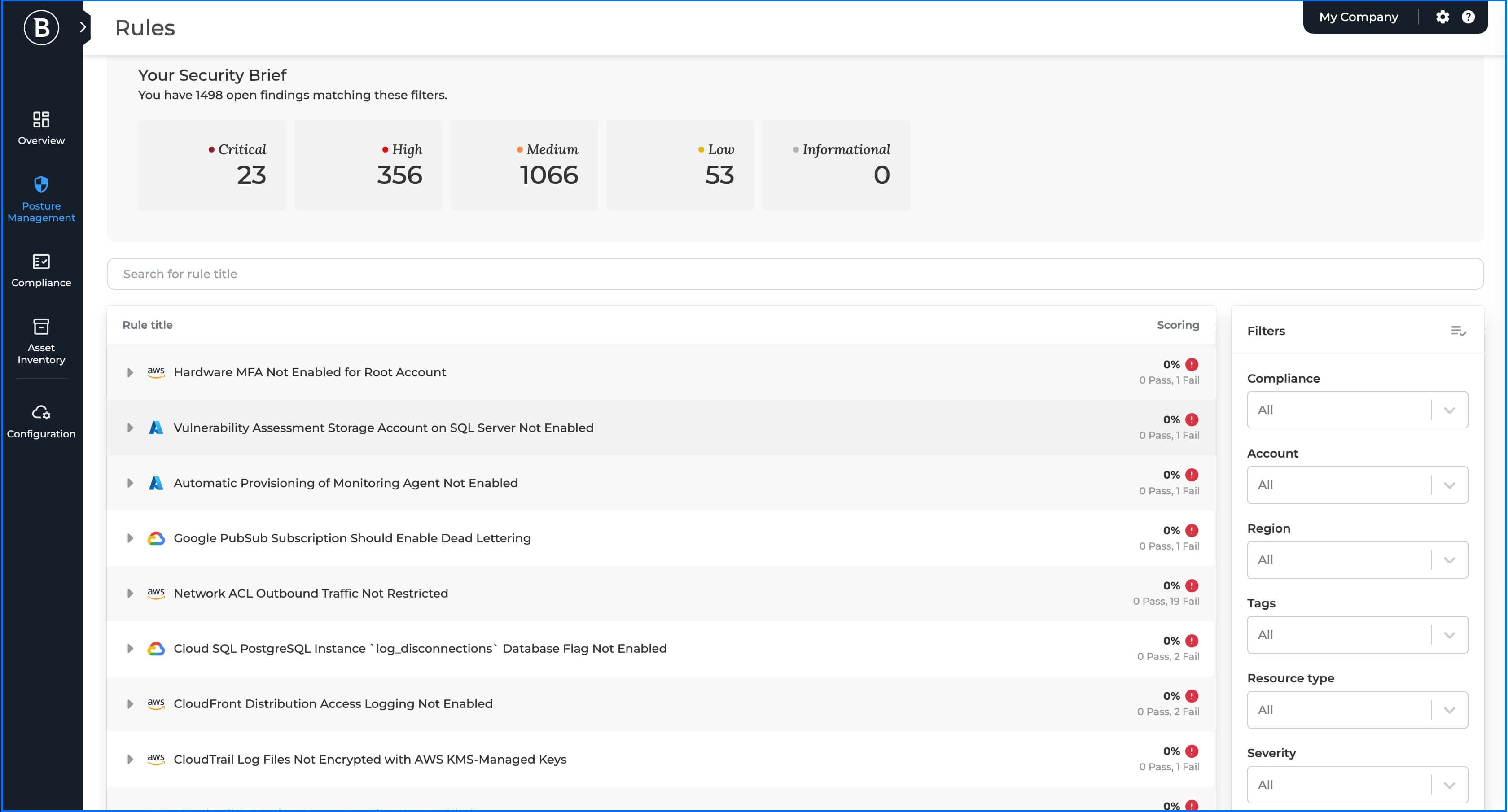
Bitdefender GravityZone CSPM+ Rules security findings.jpg
Administrators can search for critical and high-severity findings, compliance, scoring, IAM, and resource types using embedded filters to prioritize their tasks.
After selecting a rule, the Check Details section provides the administrator with information about the rule checked (Pass or Fail), affected resources, and recommendations. It includes severity which indicates the importance level (critical, high, medium, or low), and a detailed description explaining the finding's significance regardless of cloud or security expertise. This allows the administrator to decide whether remediation or fixing is necessary. Administrators can accept the risk and suppress findings for 3 or 6 months if remediation isn’t necessary or urgent, and include a justification to support future compliance audits.
The list of all supported resources depending on cloud providers is available on GravityZone Support Center here.
Security Findings and Logs
To address issues, security teams collaborate with developers, the DevOps team, and the infrastructure team. The integration we support allows administrators to export findings from Rules into ticketing tools like JIRA. The export includes the details such as rule title, account, severity, and resource type together with Manual Remediation (described in the next section of this article) and can be additionally commented on by the administrator, meaning security engineers do not have to log in to the Bitdefender GravityZone CSPM+ platform to view these findings and initiate actions. Relevant context on security issues is brought into existing user workflows rather than forcing all involved parties to come to the platform.
Remediation
GravityZone CSPM+ not only alerts you to the problem but also provides instructions on how to resolve it. This is crucial because we aim to ensure that the administrator can take immediate action based on the information from the console.
For every finding, the administrator has a Manual remediation. Additionally, depending on the cloud provider and the type of problem, they have at their disposal Terraform and Playbook Code.
Manual remediation
Manual remediation provides the administrator with step-by-step instructions on how to resolve issues with their cloud assets manually. To verify if all the changes were made correctly the administrator can run an on-demand scan.
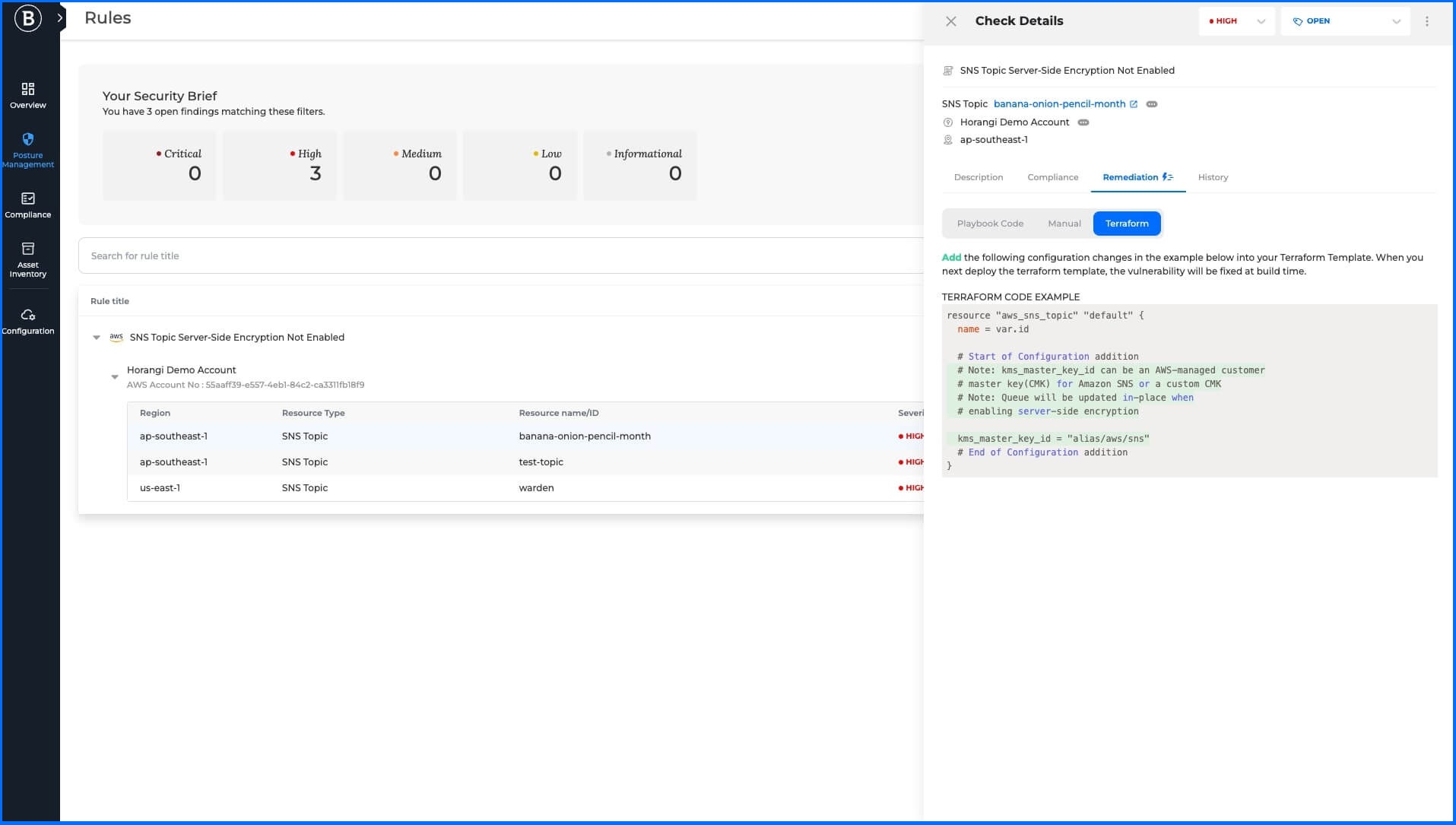
Terraform remediation
The administrator has a Terraform Code Example at their disposal, utilizing a configuration language for managing infrastructure. By tailoring the configuration in the provided example and deploying the template again, the administrator can fix the identified findings.

Playbook Code
In Playbook Code, the administrator is provided nodejs javascript code written by us and automatically generated by the platform. The code can be reviewed by the administrator, and after logging in to his cloud security provider with sufficient permissions, he can simply copy the code from Bitdefender GravityZone CSPM+ and paste it into his cloud CLI interface to fix the findings.
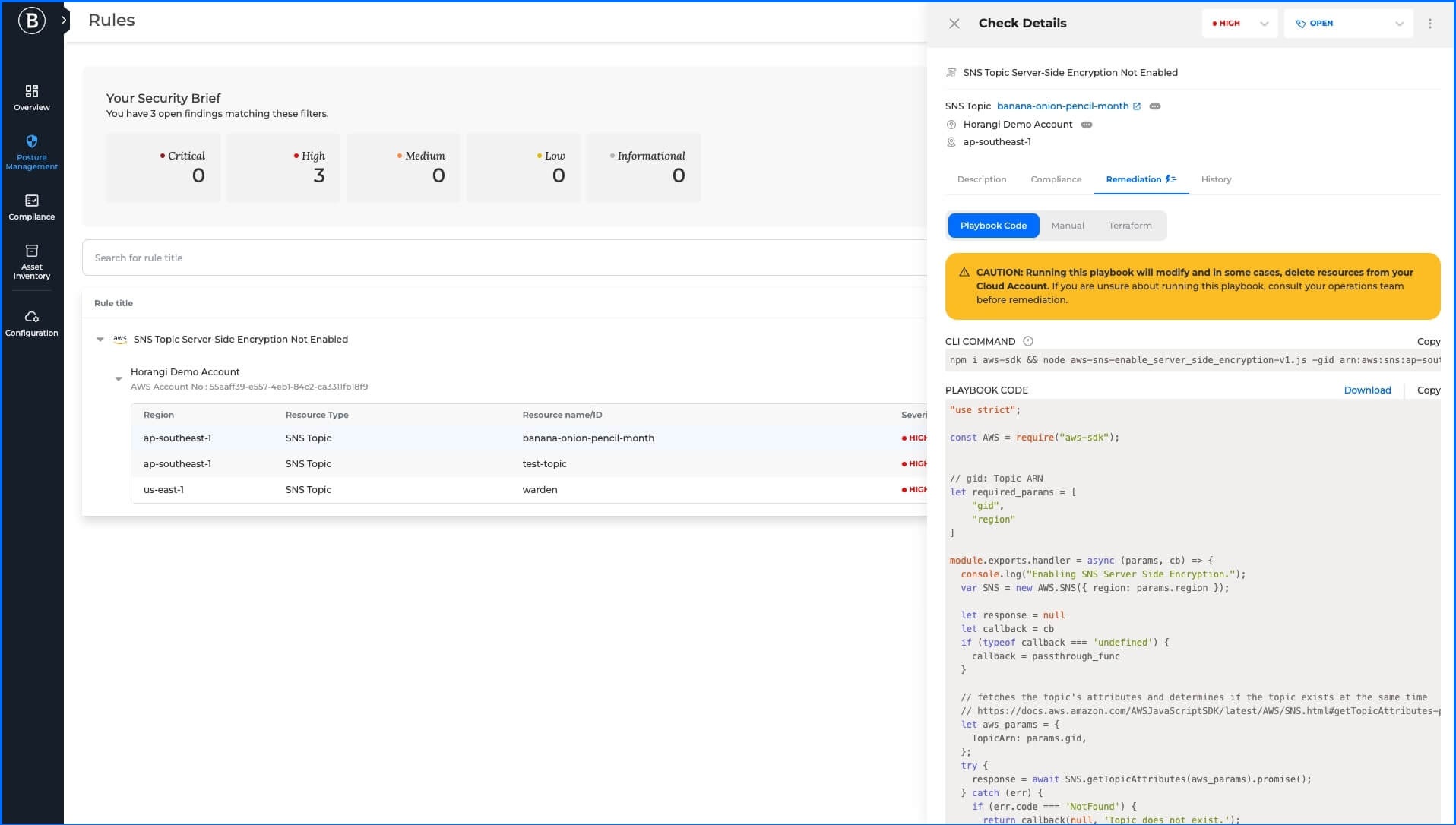
It’s worth highlighting that running Playbook Code will modify and, in some cases, delete resources from the Cloud Account.
Asset Inventory
The Asset Inventory provides an overview of the inventory list across cloud resources, various cloud providers, and accounts that have been onboarded. It is comprised of two main elements. Resources offers an overview of all existing resources detected across all your integrated cloud accounts, and Identities provides an overview of different identity types, including users, roles, groups, and service accounts. By tracking Resources and Identities administrators can verify who has access to what resources and identify potential security risks associated with specific identities.
Resources
Resources View provides visibility into compliance posture at the cloud resource level. Examples of resources include CloudFront Distribution, EC2 Instance for AWS, and Cloud SQL Instance and Compute Instance for GCP. Selecting resources, the view would expand to a list of all rules that apply to these Resources with information if the checks passed or failed.
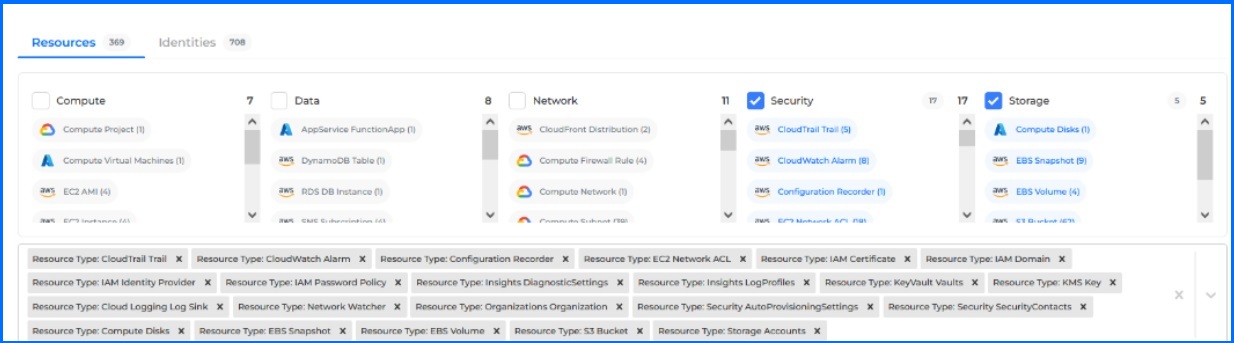
Bitdefender GravityZone CSPM+ Resources section.
Identities
The Identities tab provides an overview of different identity types: users, roles, groups, and service accounts. Administrators can filter among IAM User, IAM Role, IAM Group, and IAM Service Account.
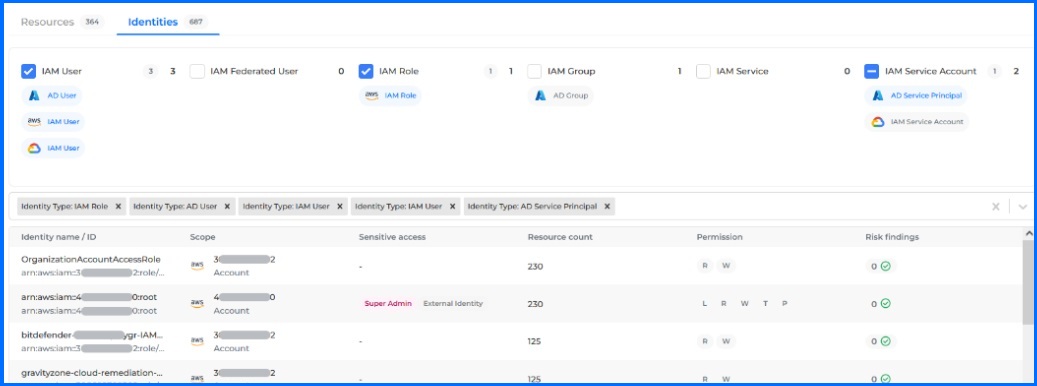
Bitdefender GravityZone CSPM+ Identities section.
By clicking on any Identity, the Details panel will be shown with information about resources, assigned policies, sensitive access, scope, and permissions.
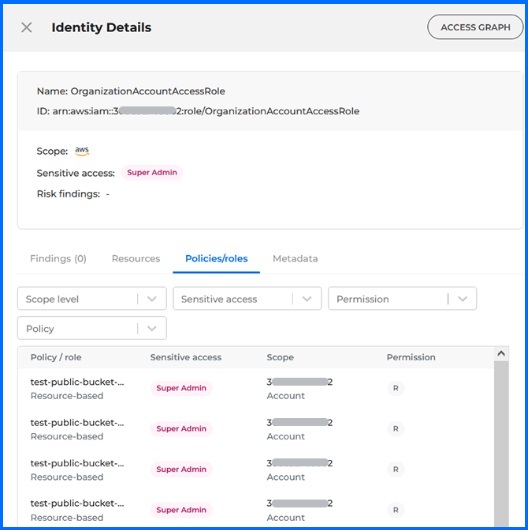
Bitdefender GravityZone CSPM+ Identities Details
Access Graph
The Access Graph offers a granular view of the access path from identities to resources within the cloud infrastructure. It represents relationships and connections between identities (such as users, roles, groups, and service accounts) and the associated resources to understand how permissions are structured and who or what has access to specific resources.
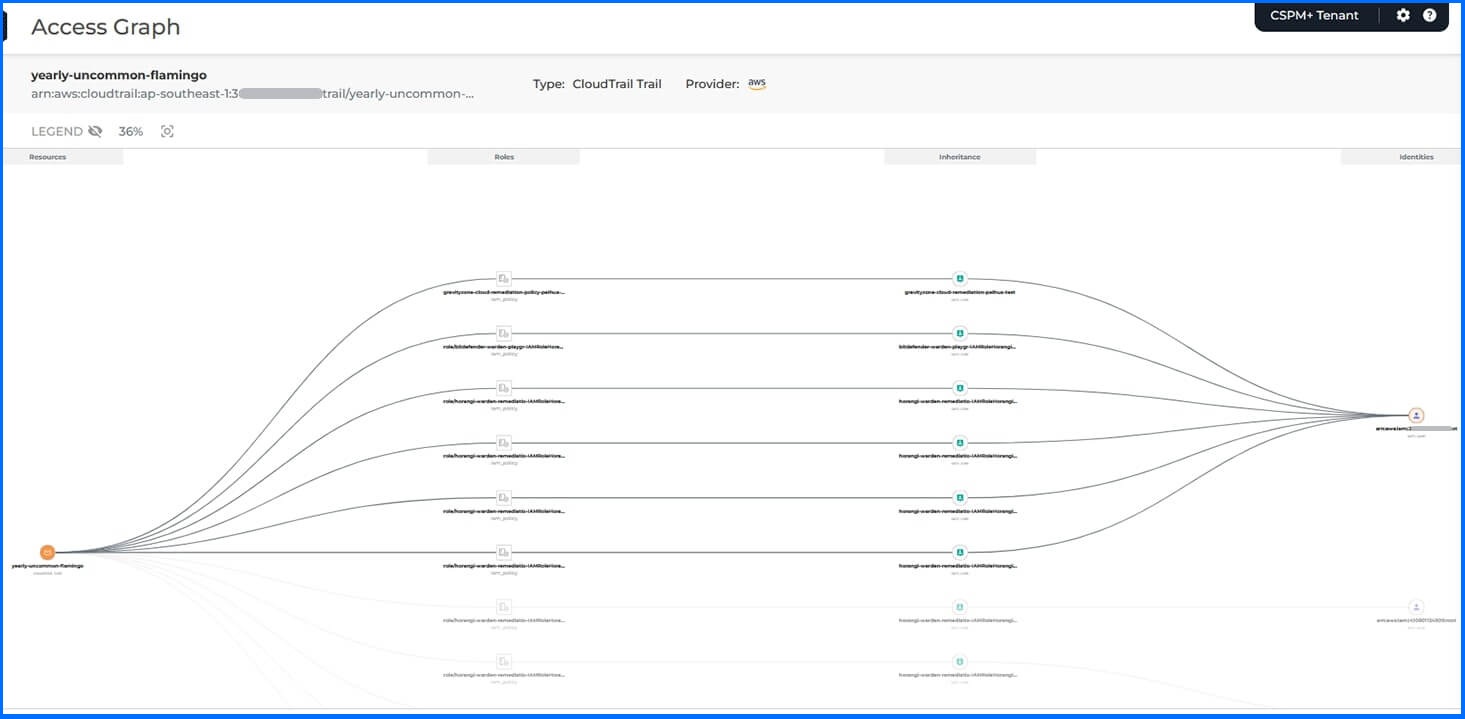
Bitdefender GravityZone CSPM+ Access Graph
The graph is automatically updated with every scan, and there are no additional setup steps required.
Summary
Bitdefender GravityZone CSPM+ is a comprehensive Cloud Security Posture Management solution designed to help organizations manage security and compliance risks in various cloud environments. The integration with AWS, GCP, and Azure allows administrators to have full visibility into cloud assets and identities. Continuous security checks, compliance monitoring, and remediation options are provided to ensure secure configurations for cloud resources to overcome complexity and focus on enhancing security team productivity.
More Resources
Bitdefender CSPM+ official website: Bitdefender GravityZone CSPM+
Bitdefender CSPM+ Guided Tour: CSPM+ Guided Tour
Discover the full potential with our dedicated video masterclasses: Elevate Cloud Security with Bitdefender's CSPM+
Recommended Content
To learn more about the technologies included in Risk Management we recommend reading the next article Proactive Hardening and Attack Surface Reduction (PHASR).