Risk Management – Bitdefender TechZone
Enhance your cybersecurity defences. Identify and mitigate security risks, prioritize vulnerabilities, and protect your business from devastating cyberattacks.
Remote, cloud, and on-premise environments introduce new security challenges due to misconfigured settings, software vulnerabilities, and complex IT environments. Human error remains a significant risk factor.
To effectively mitigate these risks, organizations must prioritize ongoing, proactive risk management across all processes. By consistently identifying, assessing, and addressing security threats, you can significantly strengthen your cyber resilience. This continuous approach protects sensitive data, ensures business continuity, and builds trust with customers and stakeholders.
Bitdefender Risk Management
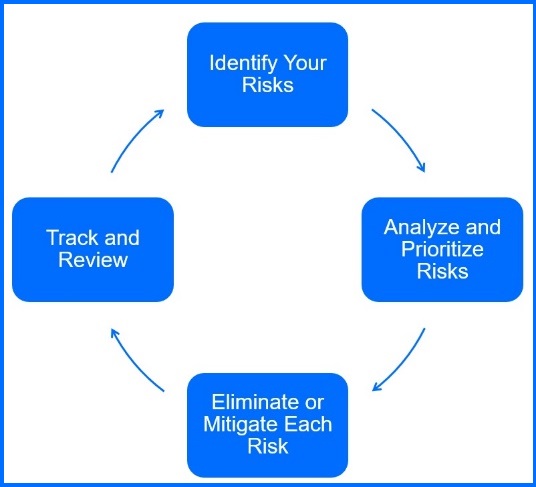
With Bitdefender Risk Management, you can proactively secure your organization by gaining a clear and easy-to-understand view of your risks, along with relevant remediation actions. This powerful tool helps you manage risks through a clear, four-step process that forms a continuous cycle:
Identify Risks: Detect and catalog all potential security threats across your organization's digital landscape.
Analyze and Prioritize: Conduct a detailed assessment of each identified risk to measure its potential impact and likelihood, enabling you to prioritize the most critical threats effectively.
Address Risks: Create targeted strategies to mitigate, reduce, or accept each risk, depending on its severity and likelihood. This could involve patching vulnerable applications, endpoint isolation, creating watchlist to monitoring specific devices or users, or selectively ignoring certain low-priority risks.
Track and Review: Continuously monitor the effectiveness of your risk mitigation strategies, making necessary adjustments to ensure ongoing protection.
Risk Management with GravityZone
With GravityZone Risk Management, you can gain a comprehensive overview of your organization's attack surface, enabling you to identify and mitigate risks across endpoints, applications, user behavior, and cloud environments.
Endpoint Misconfigurations & Vulnerabilities – helps you on Windows and Linux operating systems, identify misconfigurations, including issues with local and group policies, computer configuration settings, and application vulnerabilities. These vulnerabilities provide visibility into applications installed on managed endpoints that have been identified as containing security risks associated with the Common Vulnerabilities and Exposures (CVE) system. More information you can find in the Endpoint Risk Management article.
User Behavior Risk helps you track end users' activity in Windows computers that could potentially compromise your organization’s security. This functionality is covered in detail in the User Risk Management article.
Cloud Security Posture Management helps you verify risks associated with cloud assets on Amazon Web Services (AWS), Google Cloud Platform (GCP), Microsoft Azure. More information you can find in the Cloud (CSPM+) article.
Proactive Hardening and Attack Surface Reduction (PHASR) proactively hardens your systems by analyzing user behavior to prevent "Living off the Land" attacks and targeted threats. It uses anomaly detection to enable tailored, application action-level blocking, reducing your attack surface without disrupting operations. More information you can find in the Proactive Hardening and Attack Surface Reduction (PHASR) article.
External Attack Surface Management (EASM) helps you continuously discover and analyze internet-facing assets and their vulnerabilities, providing an attacker-centric view to proactively reduce your attack surface. More information you can find in the External Attack Surface Management (EASM) article.
Compliance Manager streamlines regulatory adherence by mapping IT controls to standards like GDPR, ISO 27001, and NIS2, offering real-time endpoint evaluations, actionable remediation steps and recommendations, and audit-ready reports. More information you can find in the Compliance Manager article.
Kubernetes Security Posture Management (KSPM) helps you identify and remediate misconfigurations within your Kubernetes (K8s) environment, such as over-permissive Role-Based Access Control (RBAC) settings that can lead to privilege escalation and persistent access. More information you can find in the Kubernetes Security Posture Management (KSPM) article.
Risk Management Configuration
To activate Risk Management, navigate to the Policies configuration within your settings. Here, you can schedule automated risk scans, ensuring your endpoints are regularly assessed without manual intervention.
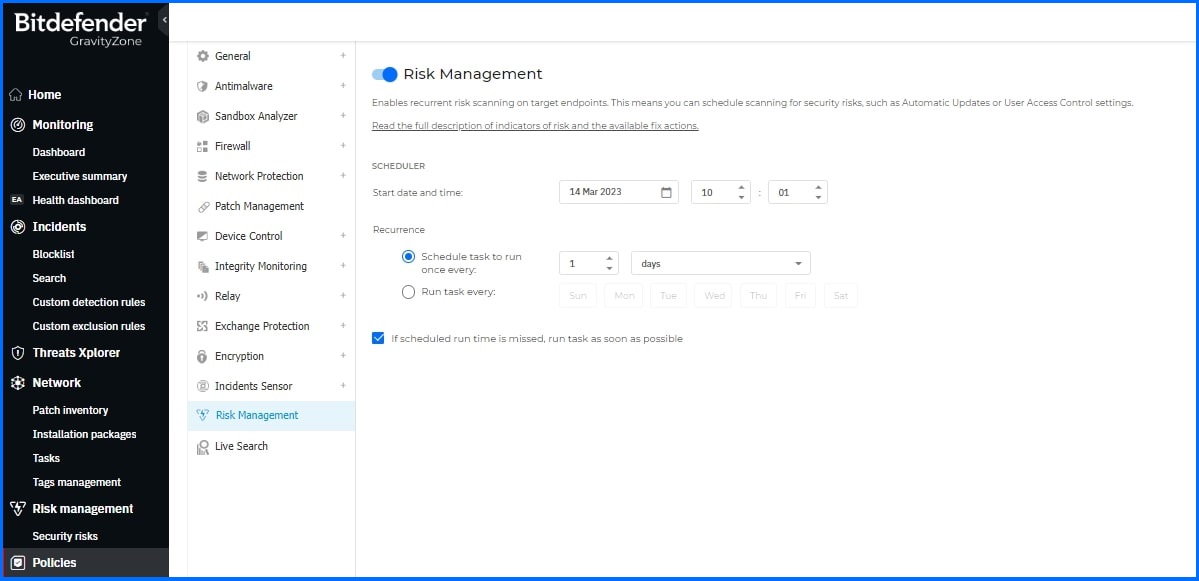
Whenever you need, you can run on-demand scans by selecting specific endpoints from the Network page. Once selected, you can initiate a Risk Scan task from the Tasks menu. On-demand scans can also be initiated using the Scan button from the Risk Management grids.
The Risk Management Dashboard
Available under the Monitoring section in the ASM Dashboard tab, the Risk Management Dashboard provides a comprehensive overview of your network security and risk assessment. The dashboard offers a customizable layout with resizable and rearrangeable widgets, allowing you to tailor the view to your needs. Within these widgets, you can pivot to view detailed information on:
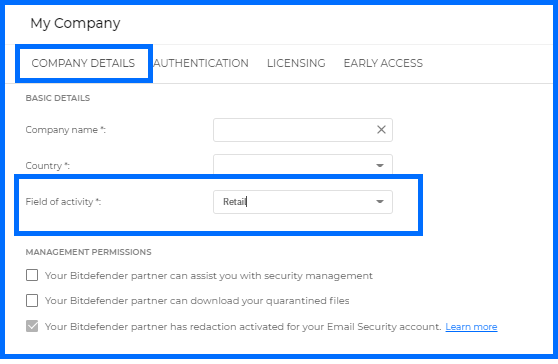
The Company state widget represents the overall risk level your organization faces. It is calculated based on factors such as misconfigured system settings, known application vulnerabilities, and user behavior, with each contributing to the final score. You can track these changes daily with the Score Over Time graph. Ignoring a risk action executed by the administrator removes the risk from the overall company risk score calculation. The Industry Modifier parameter provides crucial information about vulnerabilities and exposures (CVEs) discovered in your environment that have already been exploited by other organizations within the same industry. Your industry can be defined in the Industry field within the My Company details section:
To find the top risks related to vulnerabilities, you can use widgets that are categorized by severity and impact. This will help you identify the most critical issues at a glance and understand their potential effect on your network. Key widgets for this include Top vulnerabilities by severity and Top vulnerabilities by impact.
If you want to focus on the security of specific users and resources, the dashboard provides a clear overview of identity-related risks and a breakdown of your scanned environment. Useful widgets for this are Top identities at risk and Top resources involved in incidents.
For a general overview of all security findings, you can leverage widgets that provide high-level summaries. These widgets help you quickly grasp the most prevalent issues across your environment. Relevant widgets include Top findings by severity and Top findings by impact.
Detailed information about vidgets can be found at our Bitdefender Support Center here.
Incident Advisor with the Risk Management Component
During a security incident, it's essential to stop the attack and identify its source. GravityZone Incident Advisor was designed to minimize the time required to investigate and contain threats. Its Associated Risks widget not only pinpoints the root causes that led to the incident but also reveals all related security risks, enabling you to address it and prevent future breaches. This widget summarizes risks linked to incident-related entities and includes:
A graphical representation of the distribution of risks among the various resource types associated with the specific incident.
A list of all root cause risks detected for this incident.
The top five risks identified from Endpoint Risk Management and User Risk Management feature and top five risks identified by Cloud Security (if Cloud Security is licensed and engaged in the incident).
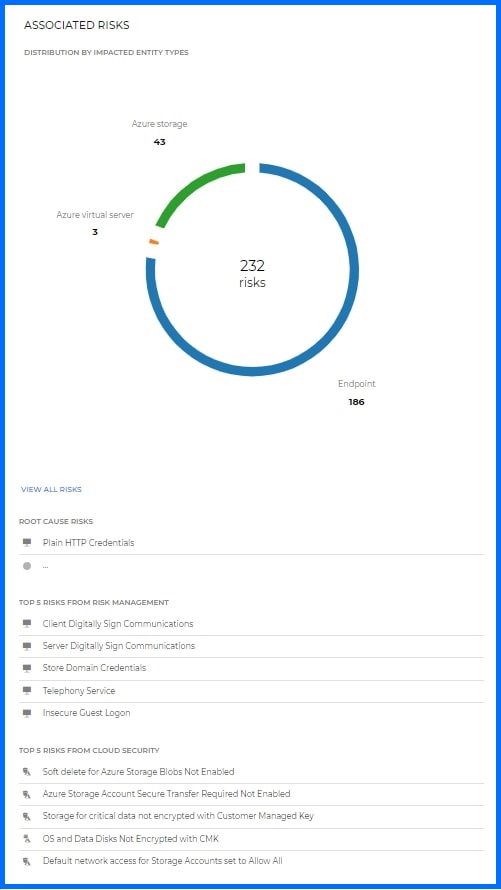
For example, if the incident occurred because a user used his credentials in unencrypted communication, which was a root cause of the incident, Risk Analytics will report it along with a list of all detected root cause risks for this incident and the top five most severe risks affecting node and resource types, as identified by User and Endpoint Risk Management and Cloud Security.
Recommended Content
To learn more about the technologies included in the Risk Management we recommend reading the next article Endpoint Risk Management.
More Resources
Bitdefender Risk Assessment official website: Endpoint and Human Risk Assessment
Bitdefender Risk Management whitepaper: A Guide to Effective Cybersecurity Risk Management
Bitdefender Risk Management Guided Tour: Risk Management Guided Tour
Discover the Risk Management full potential with our dedicated video masterclasses: Masterclass