Patch Management – Bitdefender TechZone
Efficiently manage patches and secure your systems. Easily track, install, and schedule automatic patch scans, ensuring your software is up-to-date and protected from cyber threats.
Software and hardware vulnerabilities, such as bugs, misconfigurations, and outdated systems, can be exploited by cybercriminals to gain unauthorized access to systems and sensitive data.
Once a new vulnerability is discovered and a proof-of-concept (POC) is released, cybercriminals within 24 hours create automated tools to find vulnerable systems. They then launch targeted attacks, like remote code execution (RCE), when available to gain unauthorized access to these systems.
Patch Management Strategy
Patch management is a critical component of an effective risk mitigation strategy. It involves the systematic process of identifying, assessing, acquiring, testing, deploying, and verifying software patches to address vulnerabilities and mitigate risks.
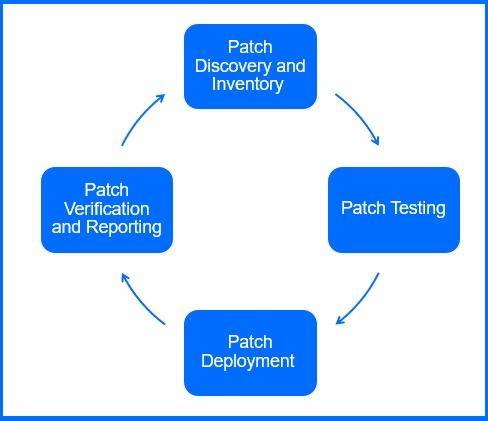
It is important to note that patch management is not a one-time task but rather an ongoing process. Regular reviews and updates are essential to maintain the effectiveness of patch management strategies.
Initial deployment
GravityZone Patch Management is an add-on component easily installed to systems through the GravityZone console by simple package creation.
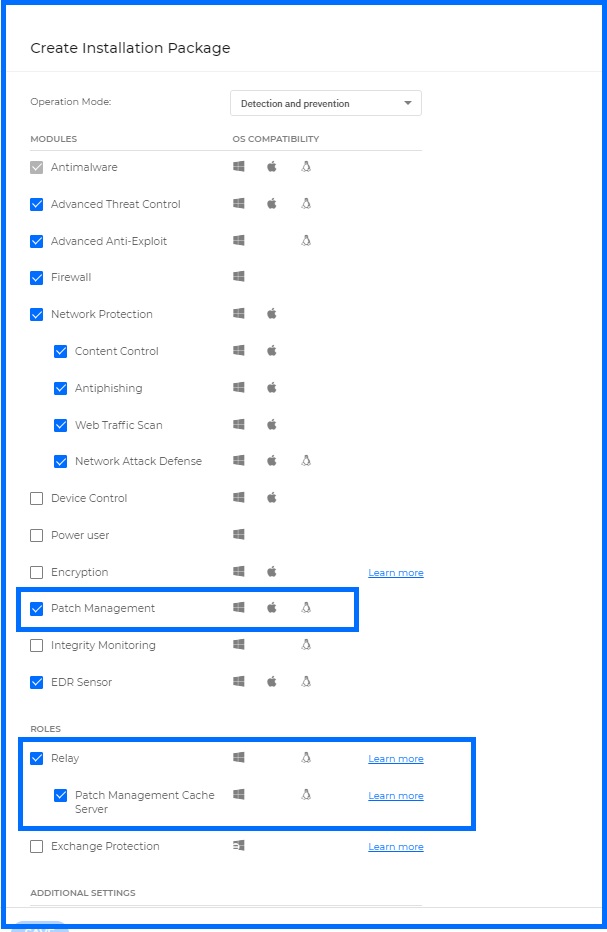
If you are using the Relay role on one of your endpoints to download its updates locally, you can add the Patch Management Cache Server role on it. It will install additional component that stores all relevant patches on the local network, accelerating patch deployment and reducing internet bandwidth usage for patch distribution and updates. If the patch caching server is unavailable, systems can automatically use vendor websites as fallback location to download patches.
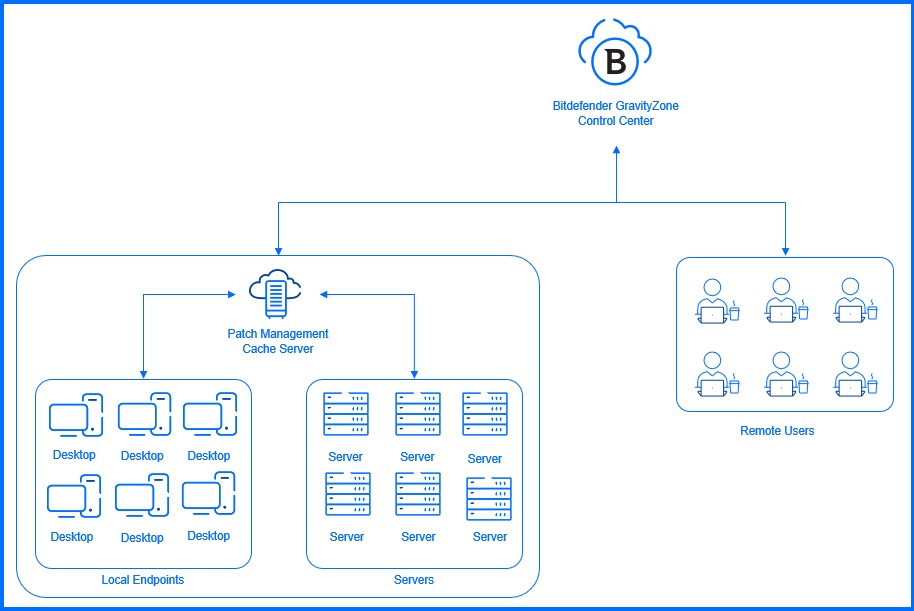
Detailed information about Patch Management system requirements can be found at our Bitdefender Support Center here and configuration description is available here.
Patch Discovery and Inventory
You can initiate a patch scan in two ways: manually or through the maintenance windows assigned to the policy.
The manual scan task can be executed at any time and is available from the Network section by selecting the desired machines and executing the Patch Scan action. For example, for a newly added server, manual scans can help identify any critical patches right away. The results of the scan will be available in a report form after the task execution in Task tab in the Network section.
Maintenance Windows streamlines the scan process through its automation. You can configure Maintenance Windows through Configuration Profiles. These maintenance windows can define a specific date and time range when patch scans are automatically triggered. The available Smart Scan feature can automatically scan newly installed software for any available patches or updates. Assign maintenance windows to policies to apply your Patch Management settings network-wide.
Detailed information on how to assign maintenance window to policy can be found at our Bitdefender Support Center here.
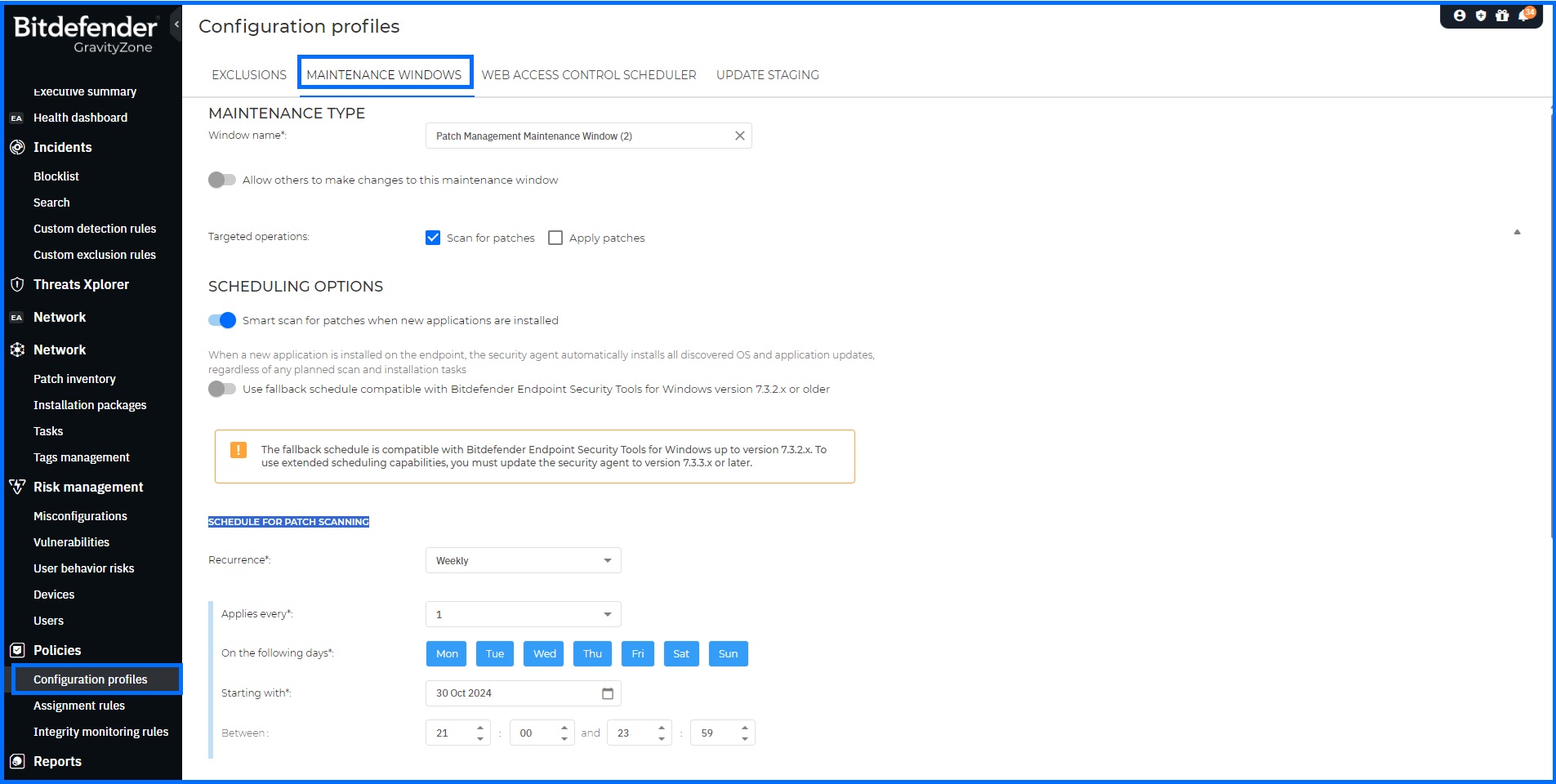
After the patch scan is completed, the Patch Inventory updates automatically.
Patch Inventory
The Patch Inventory page displays all patches discovered for the software installed on your Windows, Linux, and macOS endpoints. It provides information that helps you identify patches, evaluate their importance, and view their installation status and scope for example by sorting columns such as:
Patch severity: Informs you of the patch importance from none to critical one.
Category: Based on the type of issues they resolve, patches are groups in three categories: security, non-security, and manually approved.
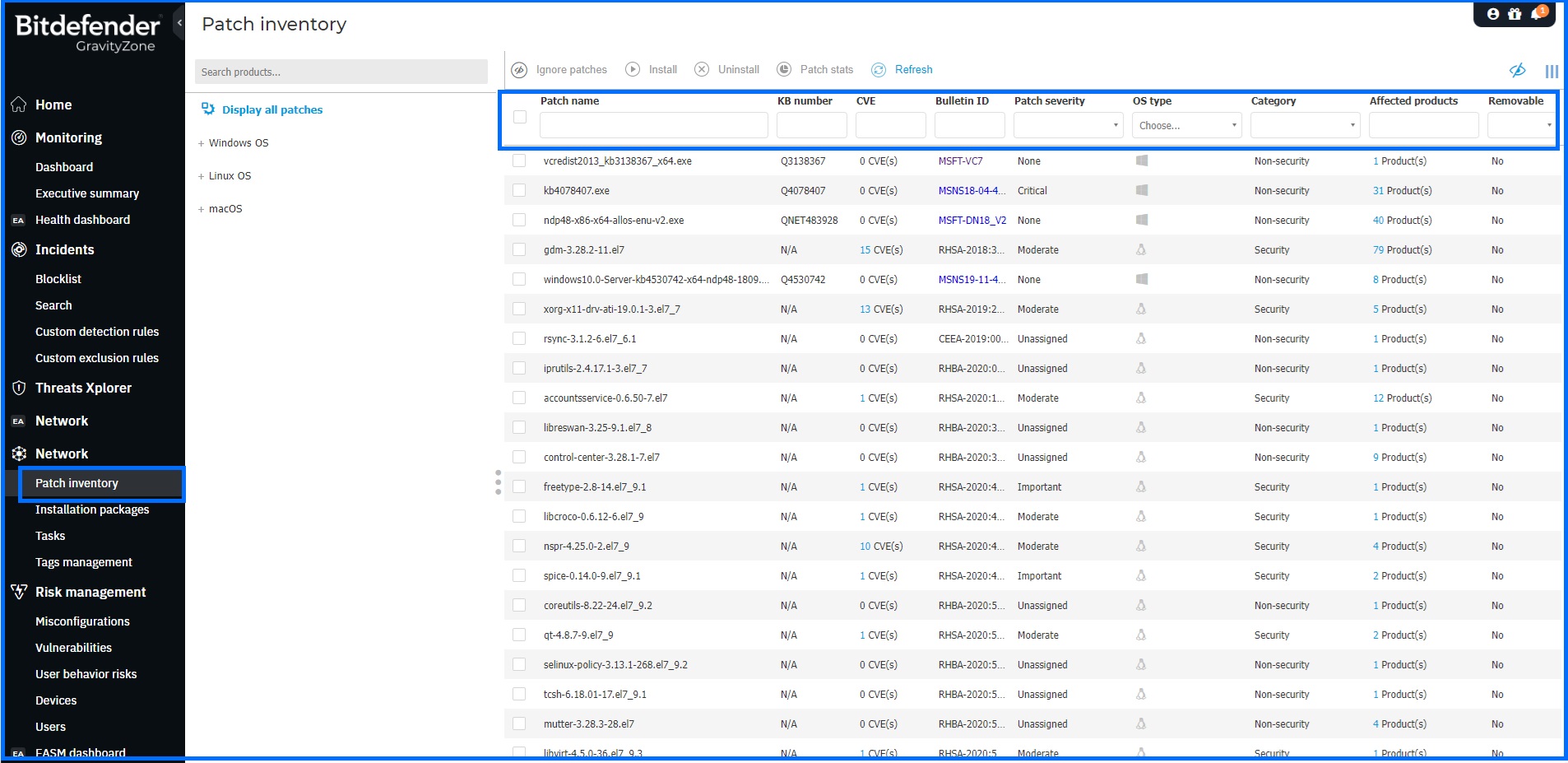
Additionally, you can see the number of Common Vulnerabilities and Exposures (CVEs) addressed by the patch in the CVE section. Clicking this number will display a list of CVE IDs.
Detailed information about Patch Inventory configurations can be found at our Bitdefender Support Center here.
Patch Testing and Deployment
With common challenges like patch compatibility issues, the best practice is to test patches before broad implementation to minimize risks and system damage.
You can manually install selected patches from the Patch Inventory section by selecting the patches and then clicking the Install button. You can select the target groups of endpoints, for example to run patch testing, and define if you want to choose to Reboot endpoints after installing the patch, if required. This option will restart the endpoints immediately after the patch installation if a system restart is required. Keep in mind that this action may disrupt the user activity.
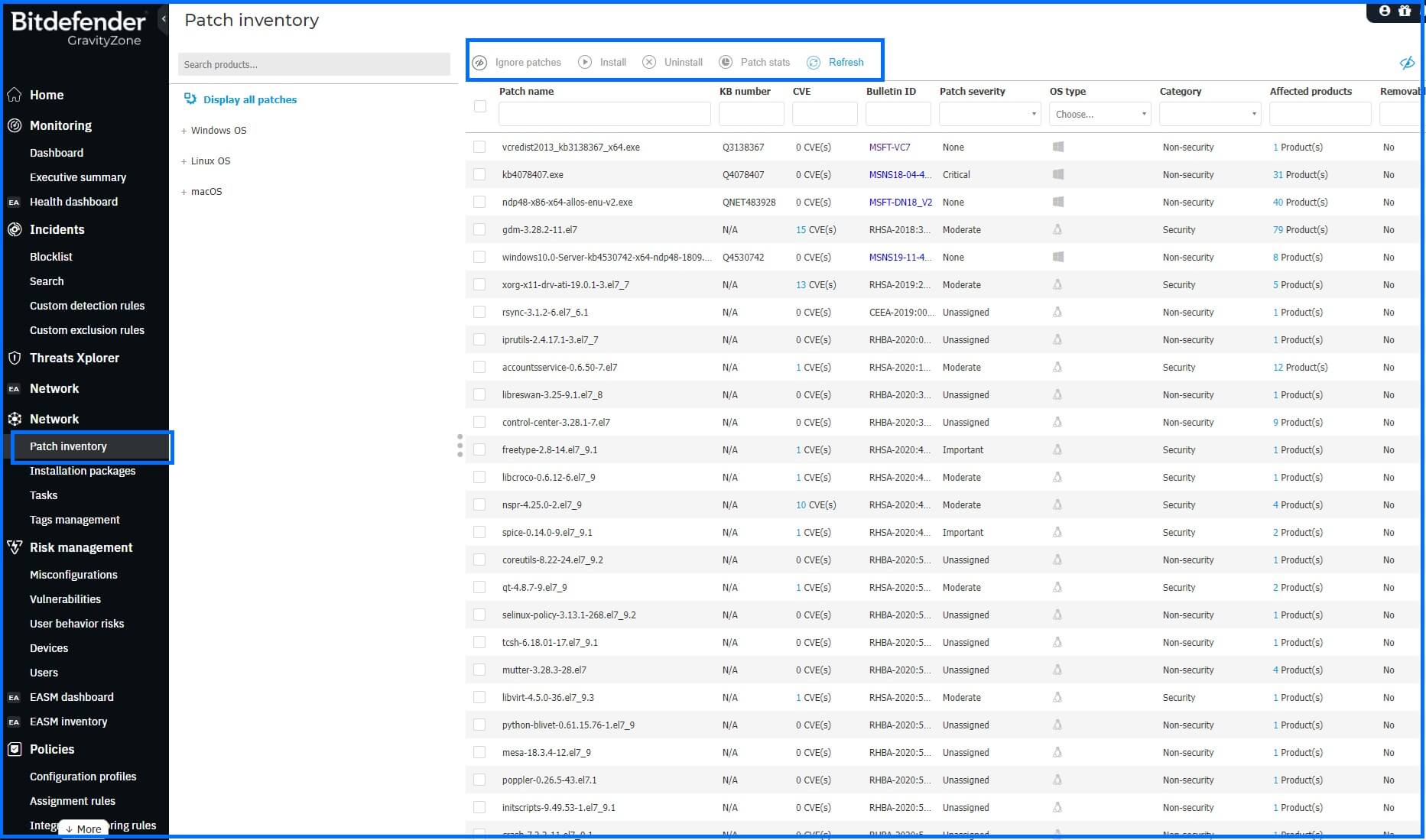
If patches that supports rollback causes malfunctions on your Windows endpoints, GravityZone provides a feature to restore the software to its previous state. Please note that only selected patches support rollback functionality. For other endpoints and patches without rollback support, you may need to manually uninstall or reinstall the software.
You may need to exclude certain patches from patch inventory, if you do not plan to install them on your endpoints, by using the Ignore patches button. An ignored patch will be excluded from automatic patch tasks, patch reports, and it will not be counted as a missing patch.
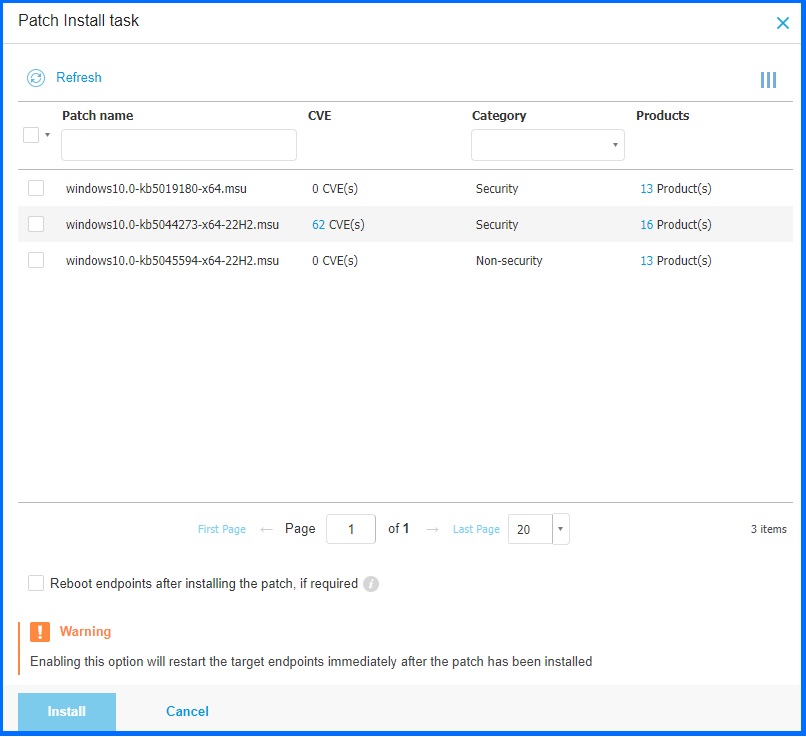
You can also manually install patches using the Patch install task in the Network Section. This allows you to select specific machines and patches for installation.
Automated Patch Deployment
To streamline the process of deploying patches after they have been validated, you can take advantage of Maintenance Windows. This feature allows you to not only scan for patches but also deploy them. You can define which types of patches to install:
Security patches: Include fixes for vulnerabilities/CVEs.
Non-security patches: These include bug fixes and new features for third-party applications.
Manually approved patches: These are patches that can impact the installed Windows version, such as Microsoft Windows Feature Updates. They often require manual intervention due to credential requirements or limited availability.
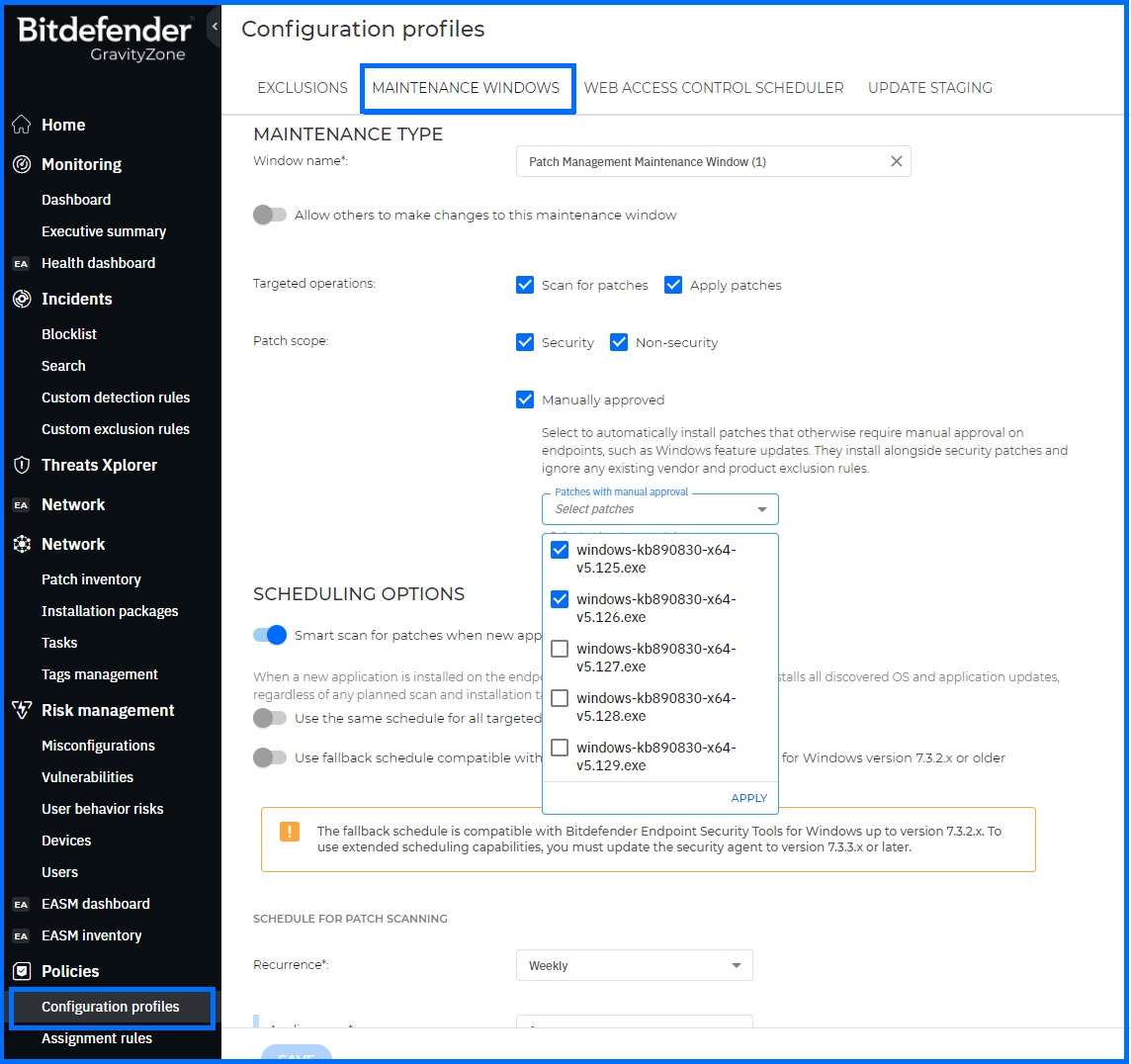
You can define two independent schedulers for patch installation:
Security: Configure when to install security and manually approved patches.
Non-security: Configure when to install non-security patches.
To fine-tune your patch management strategy and prioritize critical updates, or exclude certain applications due to licensing restrictions or other factors, you may want to specify which vendors and products should be included or excluded from the patching process in your Maintenance Window.
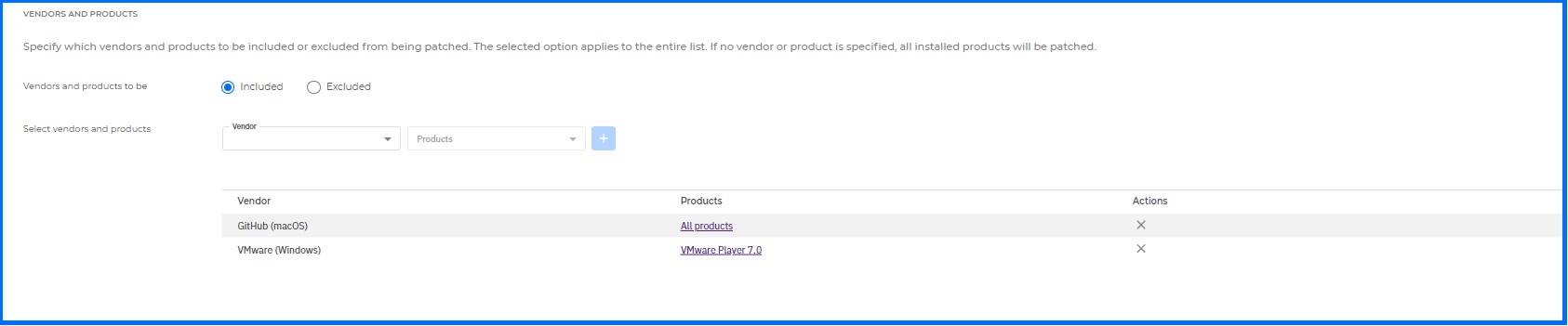
This way some of the patches will be installed automatically during the maintenance window while the rest will require manual installation.This way some of the patches will be installed automatically during the maintenance window while the rest will require manual installation.
Detailed information about the full list of supported vendors and products through Patch Management can be found at our Bitdefender Support Center here.
Patch Verification and Reporting
To view detailed information about the status of a specific patch for all endpoints, you can use the Patch Stats functionality in the Patch Inventory section. This generates an instant report for the selected patch.
For a global overview of your patch status, you can generate the Network Patch Status report from the Report section.
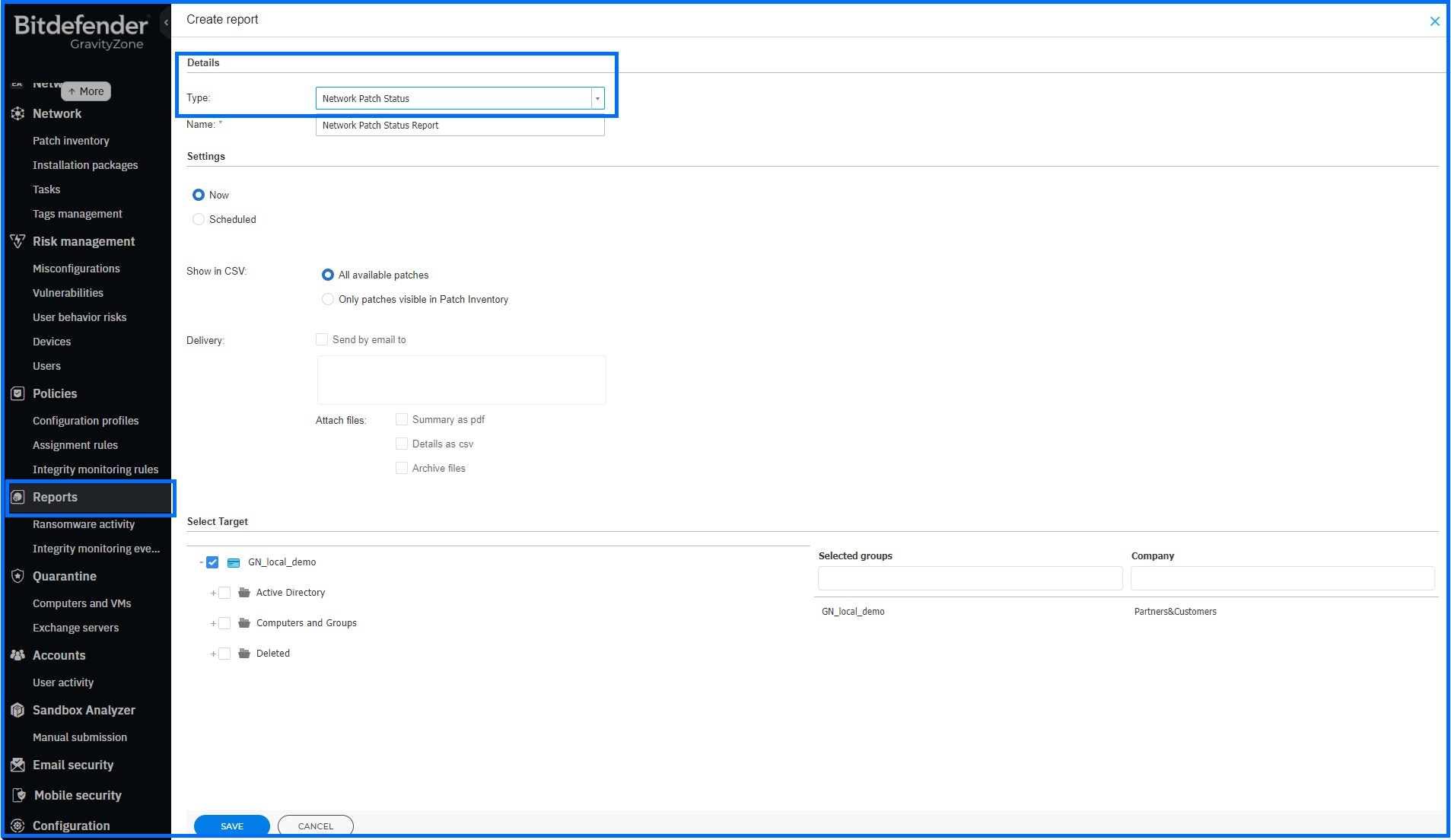
This report provides you details on the update status of software installed on target machines, including endpoint information, installed and failed security patches, missing security and non-security patches, information on manually approved patches, and the status and last modified time for checked-out endpoints.
Recommended Content
To learn more about the technologies included in the Prevention layer we recommend reading the next article Risk Management.
More Resources
Bitdefender Patch Management official website: GravityZone Patch Management
Bitdefender Patch Management Guided Tour: Patch Management Guided Tour
Discover the Patch Management full potential with our dedicated video masterclasses: Masterclass