Cybersecurity Advisory Services – Bitdefender TechZone
Safeguard your business with Bitdefender's Cybersecurity Advisory Services. Explore expert-led strategies in risk, compliance, and incident preparedness to build a resilient security posture.
New technologies offer many exciting opportunities, but striking a balance between innovation and ensuring sensitive information remains protected and IT infrastructure stays secure remains a significant challenge. Many organizations lack the expertise to navigate the full spectrum of risks across cybersecurity.
Cybersecurity Advisory Services offer a consultative approach, providing businesses with the expertise and guidance needed to navigate the complexities of cybersecurity. Think of them as trusted advisors, working alongside your team to assess risks, develop a strategic roadmap, and implement effective security controls.
In this article, we will deep-dive into all security advisory services provided by Bitdefender.
Bitdefender Cybersecurity Advisory Services
We offer a range of customizable cybersecurity services across three main pillars: Strategy and Leadership, Risk and Compliance, and Event Preparedness.
 |
Our team of experts offers a comprehensive approach that combines high-level strategic planning with practical steps to strengthen your organization's cybersecurity posture. This includes:
Identifying your cybersecurity weaknesses.
Obtaining an independent assessment of your current security.
Developing a security plan that accommodates future growth.
Benefitting from expert guidance.
Strategy and Leadership
The services under Strategy and Leadership focus on the big picture of your cybersecurity program. They help you establish a solid foundation with clear direction and leadership, ensuring your cybersecurity efforts align with your business goals. This includes developing a comprehensive strategy, creating effective policies, and building a security-aware culture throughout your organization.
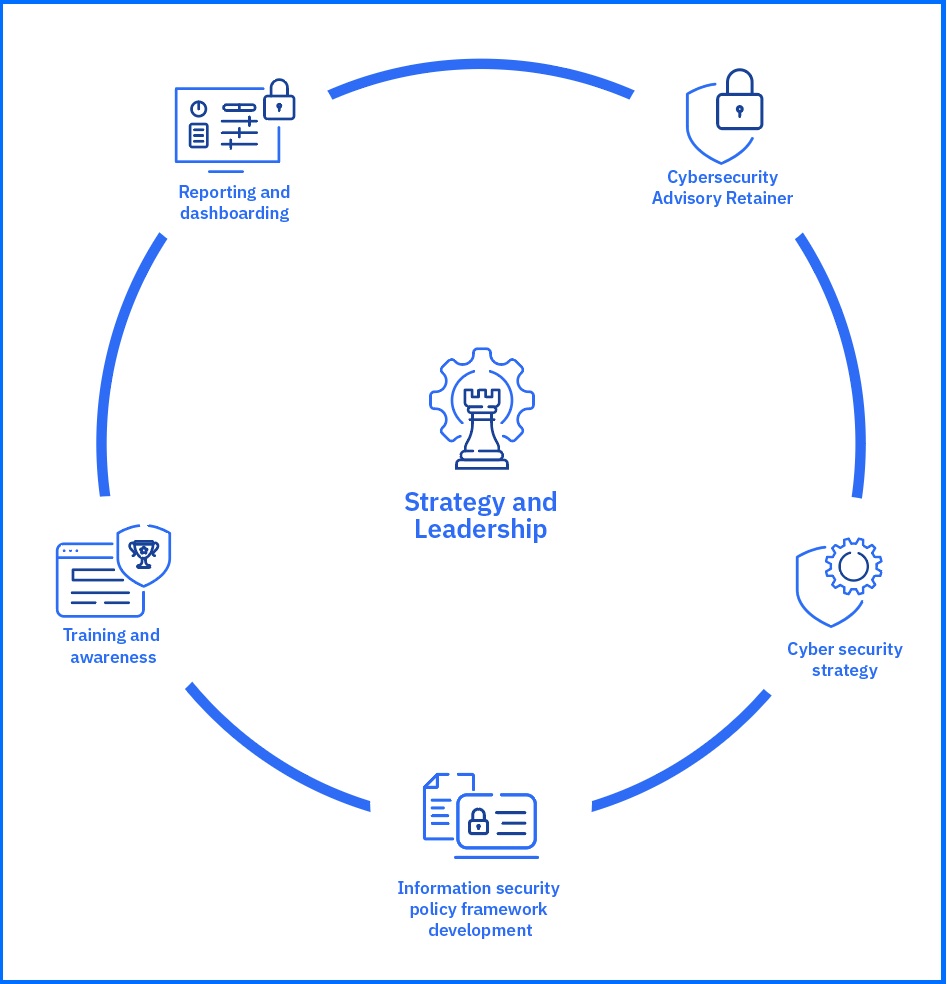 |
Cybersecurity Advisory Retainer
Cybersecurity Advisory Retainer is a cost-effective solution for businesses that need access to an ‘office’ or pool of expert cybersecurity guidance but lack the resources to hire a full-time team. Think of it as having top cybersecurity experts on-demand as an extension of your business. They can assist you with tasks like leading strategic security planning to support compliance with regulations (e.g., GDPR, HIPAA, PCI DSS, SOC) and mitigate risk. Additionally, the retainer can involve tasks such as enhancing existing security policies and procedures or the development and deployment of Incident Response and Business Continuity Plans.
Ideal for: Companies looking to optimize their cybersecurity posture without the cost of a full-timeteam.
Cyber Security Strategy
Our security specialists help you develop a comprehensive strategy that outlines your organization's security goals, objectives, and initiatives. If you already have one, we review it for clarity, ensuring it aligns with your business objectives and risk tolerance. We identify gaps or weaknesses and suggest improvements. We compare your strategy to industry best practices and recommend adjustments if needed. We also ensure it aligns with relevant industry regulations and internal policies, such as GDPR and HIPAA.
Ideal for: Organizations looking to align their cybersecurity strategy with industry best practices and compliance requirements.
Information Security Policy Framework Development
This service assists you in developing a tailored set of information security policies, processes, and playbooks. These elements work together to form a comprehensive approach to cybersecurity management, specifically designed to protect your organization's data and systems. Key aspects include ensuring alignment with relevant regulations and recognized best practices (e.g., NIST Cybersecurity Framework or EU Cybersecurity Act). This service helps you develop a clear, hierarchical framework with overarching information security policies, supporting procedures that outline specific actions, and detailed playbooks to guide responses to various security scenarios. Additionally, we focus policies and procedures on areas with the highest potential impact, maximizing the effectiveness of your security investments.
Ideal for: Organizations seeking to build a comprehensive information security program aligned with industry best practices (e.g., NIST) and regulations.
Training and Awareness
We offer comprehensive security training and awareness programs tailored to various roles within your organization. Our programs are designed to cultivate a culture of security awareness throughout your organization, ensuring everyone understands their role in protecting your data and systems. Training options are flexible, allowing you to choose programs specific to your needs. Whether you need training for the board and general employees on basic security principles or specialized training for security professionals (like secure coding), we can provide the right program to fit your requirements.
Ideal for: Organizations seeking to address the human element of cybersecurity with targeted training programs for all personnel, the board/senior management or the security team.
Reporting and Dashboarding
Reporting and dashboarding service involves developing or reviewing existing cybersecurity metrics, such as Key Performance Indicators (KPI) or Objectives and Key Results (OKR). For example, we can refine reports to demonstrate the progress and Return on Investment (ROI) of your security projects. This enhances reporting capabilities and empowers your organization to make informed decisions based on security insights.
Ideal for: Organizations seeking to leverage security metrics (KPIs, OKRs) to optimize their security posture.
Risk and Compliance
The Risk and Compliance services offer a deep dive into your cybersecurity risks, both internal and those from your suppliers. This assessment helps ensure your defenses meet security standards. We can also recommend improvements and assist with the accreditation process if that is your goal.
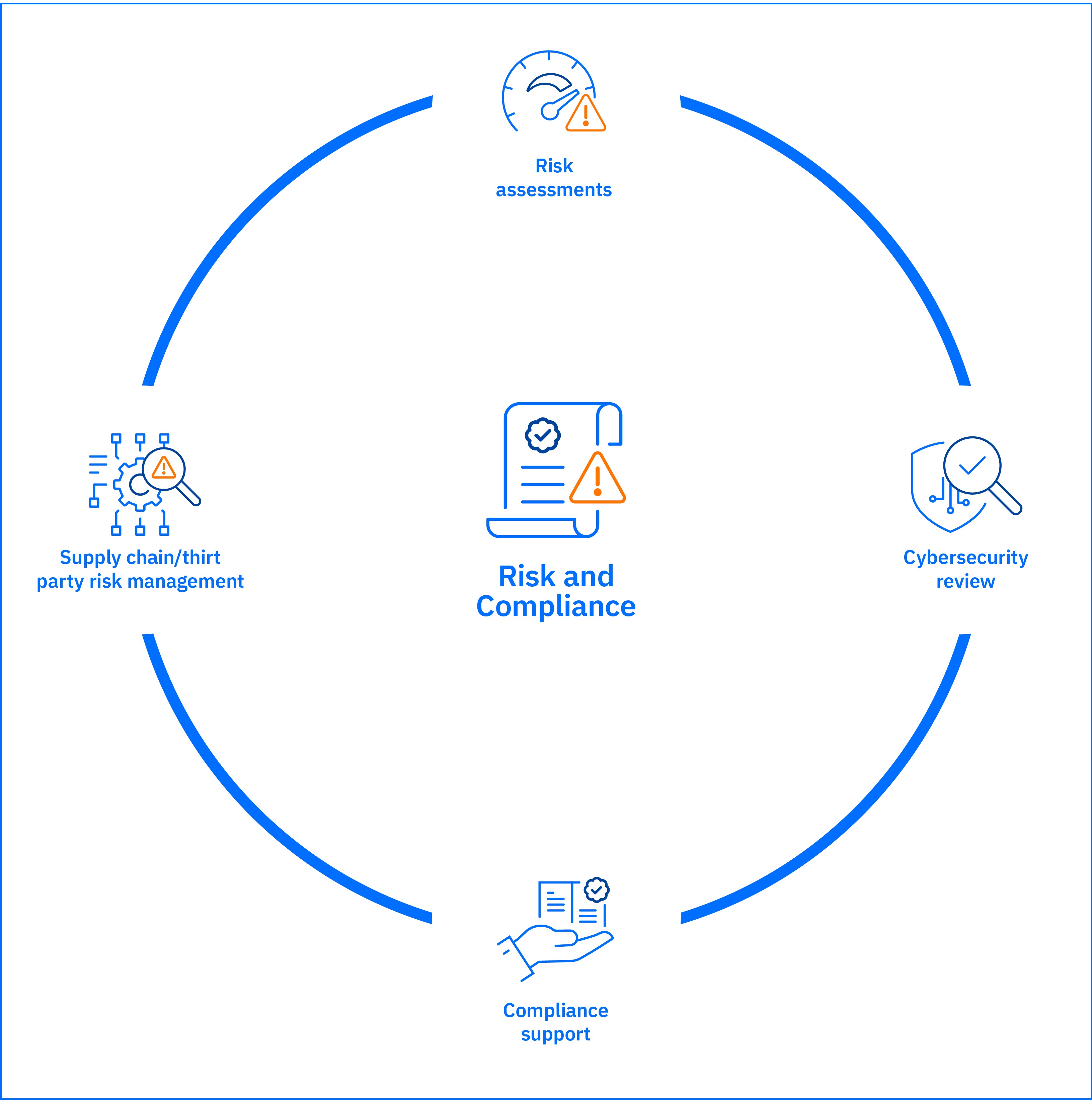 |
Risk Assessments
Risk assessments service provides a comprehensive evaluation of your organization's cybersecurity risk profile. It can assess the risks for your entire organization, or focus on specific projects, applications, or assets. Our assessments leverage industry-recognized methodologies, such as NIST RMF, IRAM2, and ISO 27005, to deliver an in-depth risk analysis.
Ideal for: Organizations requiring a comprehensive risk assessment based on industry standards to identify and prioritize security risks.
Cyber Security Review
Cyber security review service provides a comprehensive assessment of your organization's cybersecurity posture against industry standards like ISO 27001 or NIST CSF. This in-depth analysis helps you benchmark your practices, understand threats, identify strengths and weaknesses, and develop a strategic roadmap to prioritize all recommendations. We offer this service in three tiers to provide varying depths of analysis and reporting based on your specific needs.
Lite: Provides a high-level overview of your cybersecurity posture. Focuses on identifying control deficiencies within each domain of the industry framework with recommendations.
Normal: Includes all aspects of the Lite tier but in greater detail with the addition of a prioritized roadmap to address your most critical findings.
Plus: Includes all aspects of both the Lite and Normal tiers. You will get the addition of a high-level threat assessment and business impact assessment to understand your key assets, allowing you to prioritize improvements with more context of your cybersecurity landscape.
Ideal for: Organizations seeking a gap analysis against industry standards to identify control gaps and prioritize remediation efforts.
Compliance Support
This service helps you whether your organization is looking to align with well-known industry standards like ISO 27001 and SOC2 or actually achieving compliance by identifying gaps in your current practices, recommending improvements, and even assisting with the accreditation process itself.
Ideal for: Organizations seeking a comprehensive approach to compliance, from gap analysis and improvement recommendations to accreditation assistance.
Supply Chain/Third Party Risk Management
Supply chain risk management helps you secure your organization's ecosystem by defining and implementing a risk management framework and offers the option to outsource continuous monitoring and assessment to Bitdefender, ensuring your entire supply chain remains compliant with your information security policies.
Ideal for: Organizations needing a comprehensive framework to identify, assess, and mitigate risks from third-party vendors, or support with the assessment of third parties themselves.
Event Preparedness
Do not wait for a crisis to hit. Our team can help you develop a comprehensive incident response plan, proactively preparing your organization to handle security breaches efficiently.
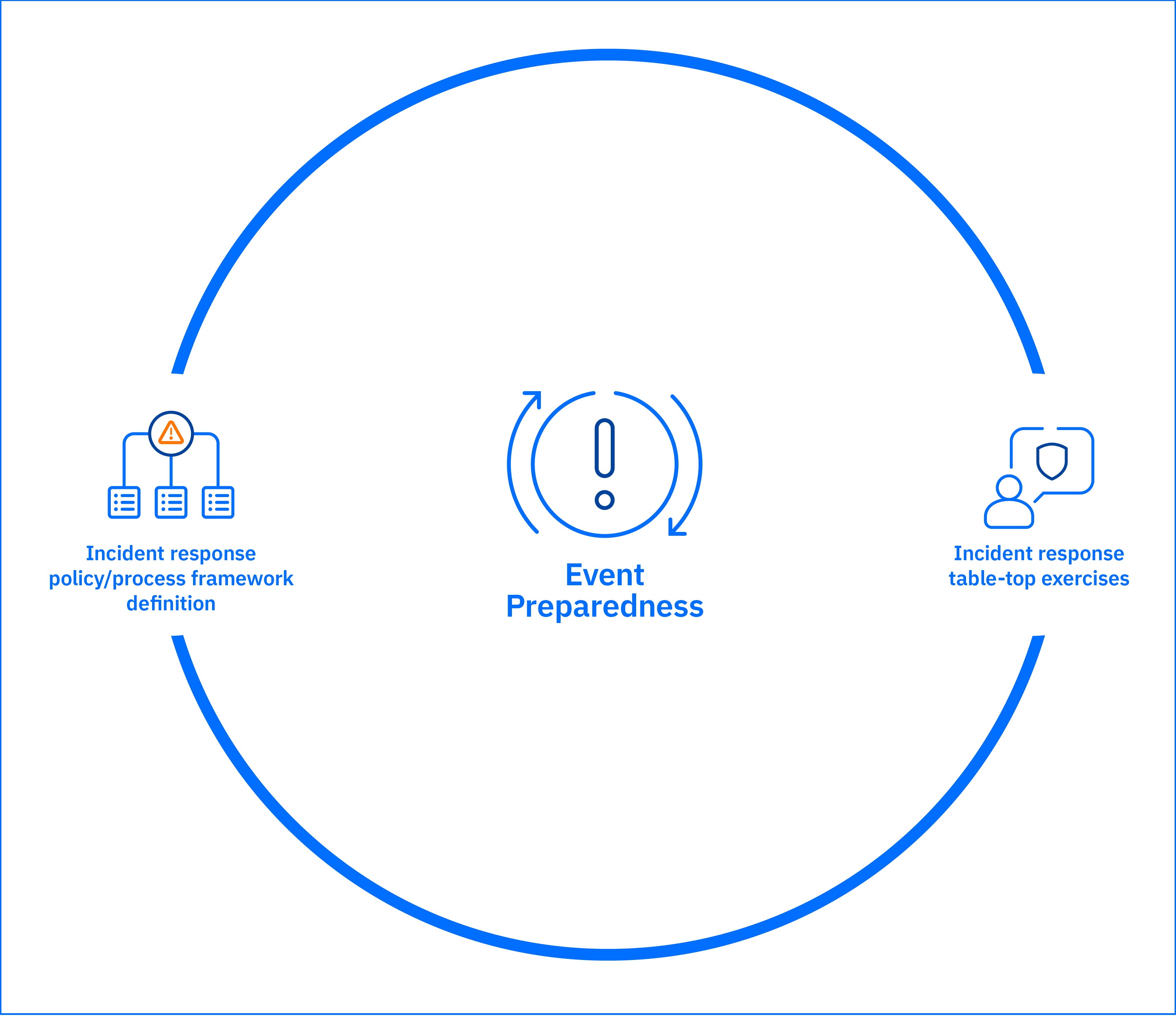 |
Incident Response Policy/Process Framework Definition
This service helps you develop a comprehensive set of policies, processes, and playbooks for incident response, including business continuity and disaster recovery plans. By establishing these frameworks, you ensure your organization has a structured and coordinated approach to managing security incidents, enhancing the effectiveness of your response and recovery efforts.
Ideal for: Organizations seeking to develop a comprehensive incident response framework, including business continuity and disaster recovery plans.
Incident Response Table-Top Exercises (TTX)
This service helps to define tailored scenarios which are then simulated, for example ransomware incidents, to test and refine your incident response plans. These interactive exercises identify gaps, improve team coordination, ensure your stakeholders understand their roles in an incident, and create a more security conscious organization.
Ideal for: Organizations needing to validate their incident response plans and identify areas for improvement through simulated scenarios.
Recommended Content
To learn more about the technologies within our Services, we recommend reading the next article Offensive Services.
More Resources
Cybersecurity Advisory Services official website: Cybersecurity Advisory Services
Why Every Organization Needs a Cybersecurity Review: Turning Risk Into Readiness