Live Search - Bitdefender TechZone
Enhance threat hunting and incident response with Bitdefender Live Search. Proactively combat threats on Windows, Linux and macOS.
Hackers use different techniques to gain unauthorized access to the corporate network. One of the most common relies on locating vulnerable systems accessible from the Internet. Depending on the application, a vulnerability can be exploited and lead, for example, to remote code execution, which occurred with a zero-day critical vulnerability like Log4j2 or React2Shell. This kind of software vulnerability enables a remote attacker to take control of a system and all its data and applications.
Once attackers gain entry points to your organization, they can initiate additional actions seeking out valuable targets and sensitive data. This progression is often referred to as the Path of Post-Compromise Attack. The next step is often moving laterally within the network. Attackers can use legitimate, pre-existing system binaries, scripts, and libraries, employing Living Off The Land (LOTL) techniques.
In the scenario described above, actions made by the attackers cannot be detected by standard protection functionality because they are using vulnerabilities, valid credentials, or trusted applications. On the other hand, each action generates events which are invaluable for your threat hunting and incident response capabilities.
Without specialized tools, you may suffer from a lack of direct visibility into live data and events. This leads to a lack of understanding of your organization’s current state—whether the company was breached, where it is vulnerable, and how many systems were affected.
Functionality Overview
Bitdefender’s Live Search is a significant addition to EDR and XDR tools, enhancing threat hunting and active incident response capabilities. By integrating Osquery, Live Search empowers you to proactively combat threats and swiftly respond to incidents across all major endpoint platforms, including Windows, Linux, and macOS.
You can access a comprehensive management layer for Osquery, encompassing and visual management through the intuitive Control Center. This approach ensures that you or your security analysts can seamlessly engage with Osquery and perform essential tasks without leaving the GravityZone console as an all-in-one security management platform.
Integration simplifies the deployment process through a centralized approach. You can effortlessly and consistently deploy Osquery across your entire endpoint infrastructure by leveraging the power of BEST (Bitdefender Endpoint Security Tools) client policies. This centralized deployment strategy alleviates operational complexities, ensures uniformity in query execution, and equips all endpoints with the necessary capabilities to conduct comprehensive security queries. Moreover, Live Search facilitates the execution of queries on multiple endpoints concurrently.
Live Search works by querying the operating system using SQL-like commands, which allows you to retrieve information easily and quickly about processes, loaded kernel modules, open network connections, browser plugins, hardware events, file hashes, system configuration, and other aspects of the operating system in real-time.
You have at your disposal more than 340 predefined queries ready to be employed out of the box, thereby ensuring effortless management.
Additionally, you have the flexibility to create new queries tailored to your specific needs, which can be saved in a private collection for repeated use. With access to over 390 tables, including more than 130 custom tables exposing EDR cache data from Bitdefender's technology, you can easily build new queries. These custom tables significantly enhance your threat hunting capabilities by providing granular visibility into behavioral artifacts that standard OS tables might overlook.
Bitdefender custom tables are easily recognizable as they always start with the edr_ prefix. While native Osquery tables gather real-time data at the exact moment a query is executed, Bitdefender's custom tables include historical data stored for a certain period (depending on the internal database size). For example, using a query like:
SELECT path, date_time, pid FROM edr_file_delete WHERE date_time > (strftime('%s', 'now') - 300);
Live Search will retrieve file deletion events that occurred within the last 5 minutes, even if the file is already gone.
The GravityZone console provides a user-friendly table side panel helper with a full description of each table, including details about columns, data types, and the specific operating systems from which the information is gathered. This embedded guidance facilitates the query creation process by providing a comprehensive dictionary of all available tables and platform compatibility (Windows, Linux, or macOS) without needing to refer to external documentation.
 |  |
You can edit your previously saved queries, giving the flexibility to modify and refine queries as needed. This essential feature promotes adaptability and ensures that you can keep your queries up to date, aligning with evolving security requirements.
In addition, Live Search offers functionality allowing submit queries to multiple systems based on specific inclusion criteria. Whether selecting specific inventory objects or defining generic inclusion criteria based on system characteristics or metadata tags, you can tailor your queries precisely. This versatility enables organizations to efficiently target specific endpoints or groups of endpoints, streamlining threat hunting and incident-response efforts.
The GravityZone console display of query results further enhance the usability of Live Search. You can view the query results, facilitating quick analysis and providing immediate visibility into potential security issues. Additionally, Live Search offers the functionality of exporting query results. This feature enables you to generate comprehensive reports that capture query findings, facilitating further analysis, sharing with stakeholders, or inclusion in incident response documentation.
Example of Usage
The security team (like Bitdefender MDR) could use Live Search for threat hunting to discover this attack in its initial stages and proactively search for any potential threats. By querying for indicators of compromise (IOCs), such as suspicious registry keys, network connections, or system events, your team can identify potential threats before they become full-blown incidents. In our case, security engineers can search for remote connections, scripts, DNS tunnelling, or PowerShell execution inside the organization.
After discovering the ongoing attack, the security team could use it for forensic and root cause analysis. Live Search can be used to gather forensic evidence after a security incident. By querying for information about file modifications, process information, and other indicators, security teams can piece together a timeline of events and identify the scope of an incident, trace the path of an attack, and identify the point of entry.
Live Search can be used for system administration tasks such as inventory management, software deployment, and compliance auditing. With Osquery, system administrators can easily gather information about the configuration of their systems, identify software that needs to be updated or patched, and ensure that their systems are in compliance with relevant regulations and policies. For example, the vulnerable Log4j library could be located and patched, which could prevent the attack completely.
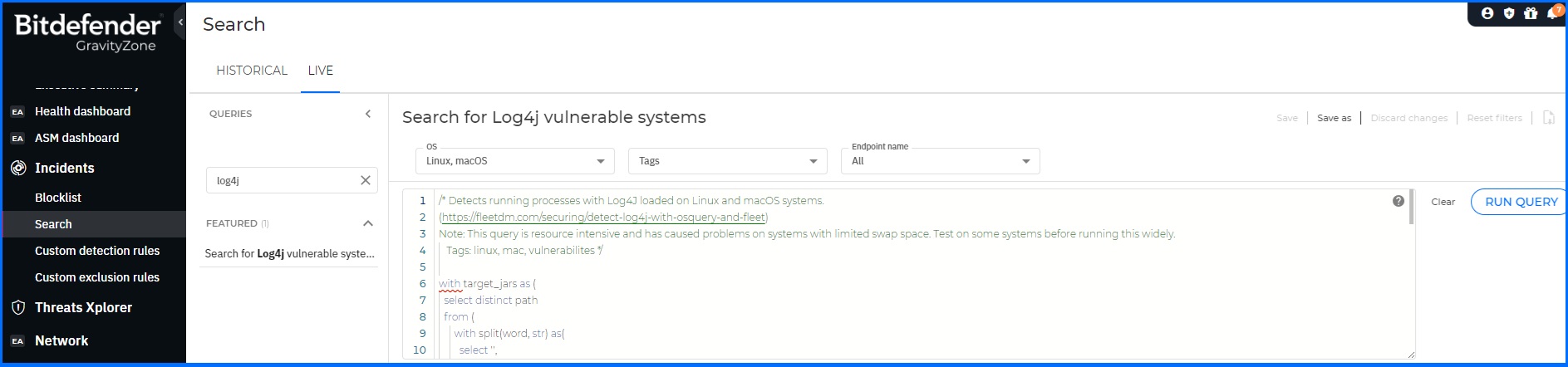
Detailed information about Live Search configurations and usage can be found at our Bitdefender Support Center here.
Recommended Content
To learn more about the technologies included in the Detection layer we recommend reading the next article YARA Rules.