Managed Detection & Response (MDR) - Bitdefender Techzone
Enhance cybersecurity with Managed Detection & Response (MDR). Proactive threat hunting, rapid response, and safeguarding digital environments.
In today's rapidly evolving cyber-threat landscape, organizations face increasingly complex and sophisticated security challenges. Traditional security measures alone are no longer sufficient to safeguard against the ever-changing tactics employed by cybercriminals. To effectively detect, respond to, and mitigate these threats, businesses require extensive expertise in the fields of security analysis and threat hunting but are faced with several challenges in staffing for these positions.
MDR services can be a game-changer by providing access to a team of experienced security analysts who continuously monitor systems for threats 24/7. MDR can identify and respond to suspicious activity, not only minimizing damage from cyberattacks but also freeing you up to focus on running your core business operations.
Organizations with existing in-house security teams can also benefit from MDR services. MDR can augment existing capabilities by providing additional expertise, 24/7 coverage, and access to advanced threat intelligence.
In this article, we will highlight Bitdefender MDR Service and explore its key capabilities, such as individual Threat Modeling and Rapid Incident Response, to show how it can address the challenges of building and maintaining a security posture for organizations of all sizes.
MDR Data Collection
Fast and accurate threat response relies on comprehensive data collection from a diverse range of data sources, which is the foundation of Bitdefender MDR.
Endpoint Detection and Response (EDR) agents are deployed on endpoints (workstations, servers) to collect data from BEST agent components such as Network Attack Defense or Fileless Protection and monitors endpoint activity, including running processes, network connections, registry changes, and user behavior. Additionally, LiveSearch allow for the detection of malicious patterns and signatures in files, memory, and network traffic, and enable the creation of custom rules to detect specific threats relevant to the organization.
To enhance visibility beyond endpoint data, Bitdefender Sensors can be leveraged. These sensors provide valuable information from various sources, including network activity, events from Productivity Applications, data collected from cloud platforms like Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform (GCP), and many more. Depending on your license, the MDR team will enhance visibility using selected sensors. For further information on Bitdefender Sensors, please refer to this article here.
Furthermore, the MDR team leverages Bitdefender Threat Intelligence (TI). This real-time intelligence provides crucial context for security events, such as information on emerging threats, zero-day exploits, and the latest attack techniques. It includes intelligence at the tactical, operational, and strategic levels. TI data is integrated into the MDR platform to enhance threat detection, prioritize alerts, and guide incident response activities.
MDR Deployment
MDR deployment begins with data collection and analysis, which significantly influences the efficiency and effectiveness of the MDR service. This process involves gathering information such as company name, corporate structure, key individuals, products, and services, as well as information on partners, business affiliates, and data assessment. This allows for an assessment of potential threats, including Tactics, Techniques, and Procedures (TTPs), and Indicators of Compromise (IOCs). This information is then used to set up proper monitoring through intel feeds, dashboards, and other analysis tools, as well as to create Threat Modeling and intelligence Threat Hunting packages.
Deployment of Bitdefender GravityZone technology can be easily performed by your internal IT team or a partner using the GravityZone console. Our Professional Services are included in both MDR service offerings and can help deploy GravityZone to ensure that all necessary configuration is correct.
When you decide to use the Professional Services, the deployment process typically includes the following steps:
A kickoff call to discuss your specific needs, expectations, and the scope of the project, outlining the services to be provided and the project timeline.
A comprehensive GravityZone configuration, including policy configuration, EDR and XDR Sensor deployment.
Post-installation verification to ensure successful deployment across all endpoints and to address any failed installations or issues encountered.
A final health check verification to ensure the optimal performance and effectiveness of the deployed solution.
MDR Service components
Effective threat prevention, detection, and response require a collaborative approach between Security Operations Center (SOC) analysts and Cyber Threat Intelligence (CTI) teams. Bitdefender MDR service reflects this principle, leveraging the expertise of a highly skilled team comprising:
Threat Research/Intel Analysts: This team focuses on gathering, analyzing, and disseminating threat intelligence, including information on emerging threats, vulnerabilities, and the tactics, techniques, and procedures (TTPs) employed by adversaries.
Detection Engineers: These specialists focus on developing and refining detection rules and signatures, continuously improving the ability of the MDR platform to identify emerging threats.
SOC Analysts: These analysts are responsible for 24/7 monitoring of security alerts, performing threat hunts, and conducting in-depth investigations of suspicious activity.
Threat Responders: These experts specialize in incident response and remediation, working to contain and mitigate the impact of cyberattacks.
To effectively address the diverse needs of organizations of all sizes and budgets, Bitdefender offers two distinct MDR services. Below we highlight their key features and benefits.
Bitdefender MDR | Bitdefender MDR PLUS | |
|---|---|---|
 |  | |
24x7 SOC |  |  |
Pre-approved Actions (PAAs) |  |  |
Threat Hunting |  |  |
Expert Recommendations |  |  |
Incident Root Cause & Impact Analysis |  |  |
MDR Portal & Reporting |  |  |
Professional Services On-boarding |  |  |
Cybersecurity Breach Warranty |  |  |
24x7 Security Account Manager |  | |
MDR team leverages Global Threat Intelligence |  | |
Tailored Threat Modeling |  | |
Brand and Intellectual Property Protection, |  | |
Add-ons | Add-ons |
Bitdefender MDR delivers comprehensive cybersecurity 24/7 from three global Security Operations Centers (SOCs) using a follow-the-sun model: one in Texas (USA), one in Romania (EU) and one in Singapore (Asia Pacific). All SOCs use the same level of knowledgeable staff, processes, and technology to ensure unparalleled 24/7/365 global coverage for our customers. Our highly skilled, and certified security analysts, with backgrounds in organizations like the U.S. Air Force, U.S. Navy, British Intelligence, and the NSA, operate from these centers, providing you and all customers with expert protection.
Threat Modeling and Risk Assessment
During the MDR deployment process, the MDR team will gather information about your environment, business, users, and known threats. This information, combined with threat modeling, is crucial for establishing a security baseline and ensuring an accurate understanding of the threat landscape for your monitored environment. Threat modeling is a proactive process that begins with building intelligence requirements that support the business's security needs. Continuous research provides detailed intelligence to customers, answering critical questions:
Who might target the business?
What are their motivations and capabilities?
Where are the potential attack vectors?
Why would they choose to target this specific organization?
This analysis, coupled with an in-depth assessment of your environment, helps identify potential threats, Tactics, Techniques, and Procedures (TTPs), and Indicators of Compromise (IOCs) that may be of concern. The threat modeling process includes a comprehensive evaluation of industry trends, recent and related incidents, and key attack vectors that require close monitoring. This approach enables the MDR team to create a unique Threat Model tailored to your specific needs and risk profile.
The MDR deployment process also includes the identification of high-value or high-risk assets within your environment. For these critical assets, we implement separate processes to provide higher priority and a more focused level of monitoring, known as Priority Target Monitoring. This approach can significantly minimize the risk associated with security incidents related to these critical assets.
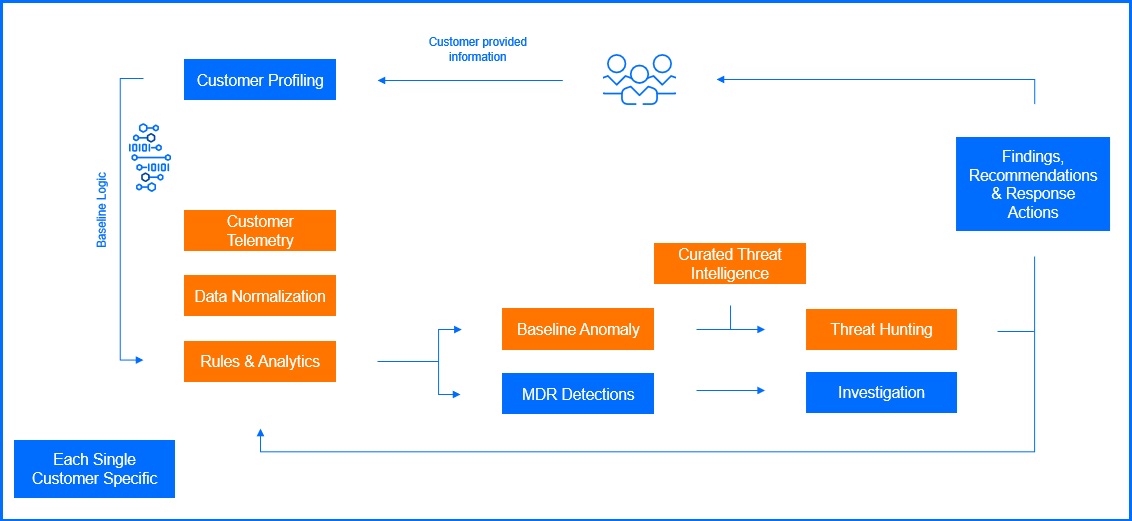
Threat Hunting
Risk-Based Threat Hunting utilizes a proactive approach to identify and mitigate potential threats. Our Threat Research/Intel Analysts team continuously analyzes the global threat landscape, identifying emerging threats and vulnerabilities. Based on this analysis, the Bitdefender MDR team develops targeted hunt packages. These packages focus on specific threats relevant to each customer's unique risk profile, considering factors such as industry vertical, geographical location, and the presence of certain applications within their environment.
Targeted Threat Hunting is performed for each customer on a 2-week interval. This involves anomaly detection based on a deep analysis of events collected from endpoints, for example file manipulation, network connections or registry key modifications. Our SOC analysts review your environment to identify deviations from baseline behavior across various dimensions, such as user behavior, application activity, and network data. This aims to identify and address advanced threats, zero-day exploits, and insider threats that pose significant risks to your organization. Through targeted hunting, the MDR team can minimize the dwell time of advanced threats, including Advanced Persistent Threat (APT).
Threat Management
Threat management leverages comprehensive data collection from EDR agents and XDR sensors, enriched with real-time Threat Intelligence, to effectively identify and prioritize security incidents and events that require immediate action. A set of documented actions can be executed in response to findings within your protected environment. These actions, described in detail in the MDR Incident Response section, include pre-approved actions that can be executed by the MDR team without prior consultation.
Brand and Intellectual Property Protection
Brand/IP reputation monitoring helps the company's reputation remain intact within the digital realm. By actively monitoring online platforms, social media, and other digital channels, we can identify instances of brand impersonation, phishing attempts, or unauthorized usage of intellectual property. The MDR team monitors also all your domain properties for newly created domains that could indicate "typo-squatting" or URL hijacking behavior by bad actors.
In a double extortion attack, your company's data may be published or sold on the dark web. Digital Asset Monitoring ensures that your data or code is not being leaked or distributed on public forums such as code repositories or paste sites. By Dark Web Monitoring, our MDR services can detect potential threats related to your company's sensitive data, credentials, or intellectual property that may have been compromised or are being sold illicitly.
MDR Incident Response
During the MDR deployment process, we will work with you to create a customized monitoring-response runbook. This runbook defines the team’s standard operating procedures for working with you on monitoring alerts and includes custom escalation procedures aligned with best practices and your specific business needs. In case of security incidents, the MDR team maintains constant communication with designated contacts within your organization throughout the incident response process, providing guidance and informing you of any pre-approved actions taken. Pre-approved actions may include:
Stop process. Terminate a process that has been determined to be malicious.
Block file. Block a malicious executable from running on the host.
Delete file. Delete a file that has been determined to be malicious.
Quarantine file. Move a suspicious file to a quarantine folder so that it cannot be used accidentally. The file will not be deleted.
Block port. Block the host from exchanging network traffic on one or more network ports that have been determined to present a risk. For example: port 80 or 443.
Block IP. Block the host from exchanging network traffic with one or more IP addresses that have been determined to be malicious. This action does not apply to servers.
Isolate host. Isolate the host from the network so that it may no longer make or receive connections with other systems.
Response shell. Access may be granted to run commands on the endpoint in order to investigate or mitigate malicious activity.
Delete email. Delete an email message from the inbox after it has been determined the message is malicious.
Disable user. Disable the user's ability to log in after determining their is malicious activity associated with the account.
Mark user as compromised. Mark the user as compromised in Active Directory. This action is only available for customers with the Microsoft E5 level license.
Force user credentials reset. After determining an account may be misused, the account will be set so the user must reset their password on the next login.
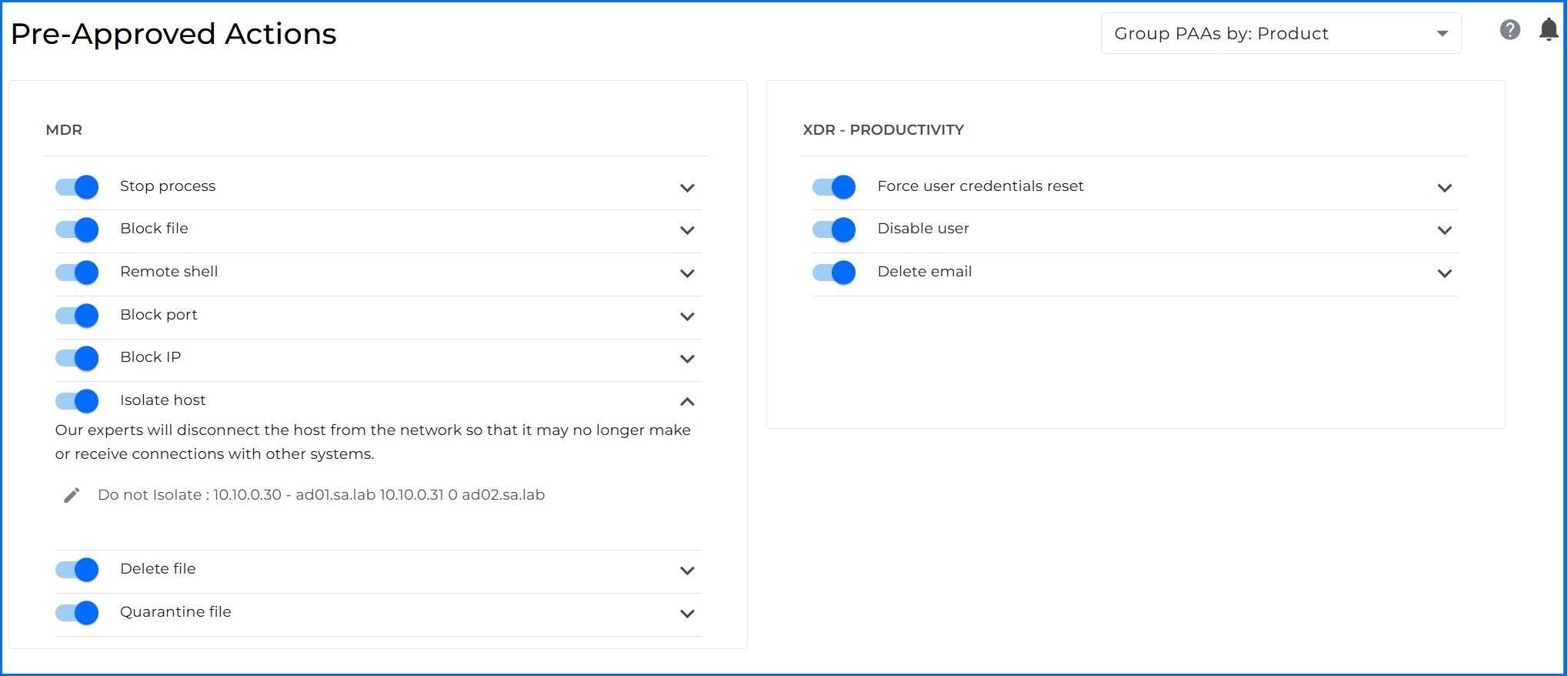
In MDR Customer Portal under each action, you can provide additional information for our MDR team. For example, if you do not want or cannot isolate a key service for the business in the Isolate host pre-approved action, you can add a note about not blocking specific hostnames.
For critical and high incidents, you will receive an email from our MDR team within 30 minutes of the incident to schedule a phone call to provide more information. Additionally, you will receive a phone call when the MDR team begins the incident investigation. All notifications and updates are described in detail within the EULA here.
After Action Reports are generated for completed incident investigations. They contain the details of the attack, a summary of the actions taken by the SOC and any recommendations on changes in the environment to help prevent similar incidents in the future.
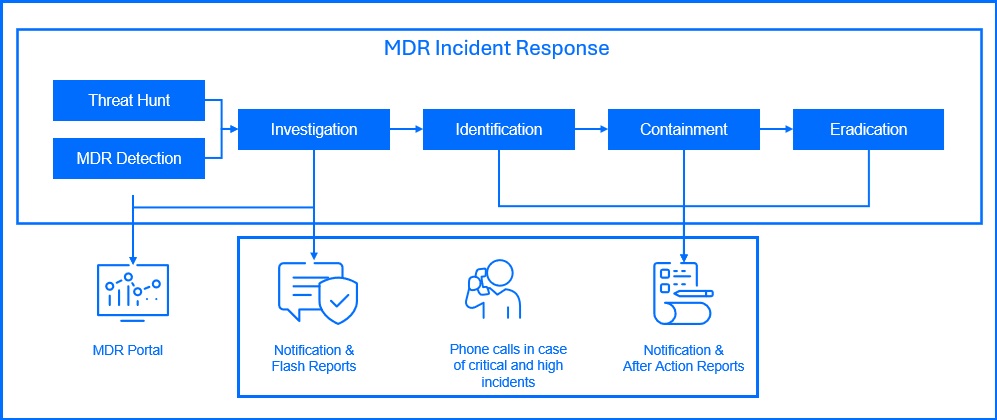
MDR Visibility and Reporting
Understanding your security posture requires access to comprehensive and actionable insights. You have direct access to all data related to the reports generated at the endpoint or sensor level within the GravityZone console.
The Bitdefender MDR Customer Portal provides access to a Real-Time Dashboard summarizing telemetry from your environment and statistics regarding alerts, incidents, and MDR hunting activities. You have access to after-action and monthly reports that provide insights into security incidents, remediation efforts, and offer transparency into the MDR processes.
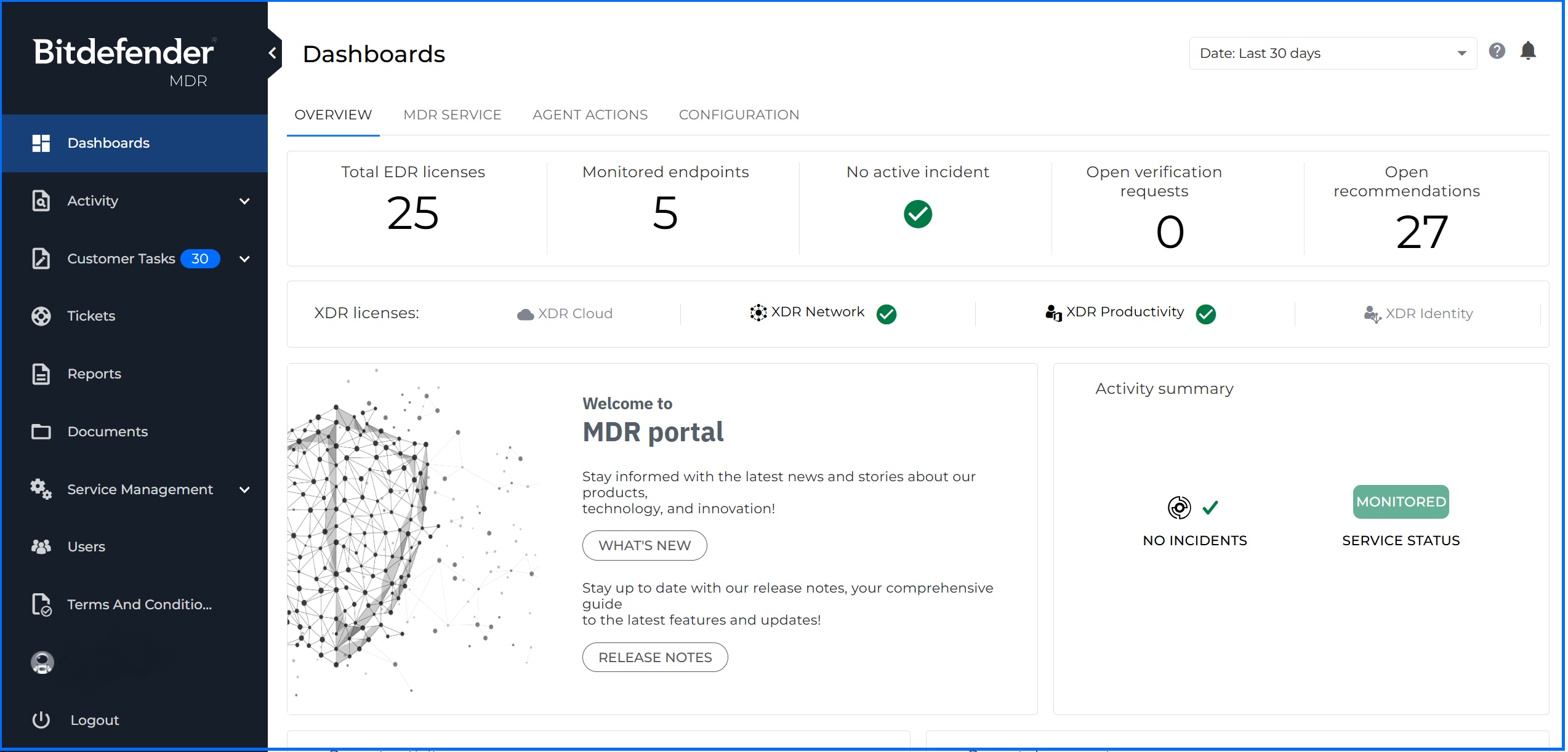
MDR Customer Portal
The MDR Customer Portal provides features that allow you to better keep track of the MDR investigations, threat hunts, reports, and cases, while also providing a tool for cross-communication with the GravityZone MDR SOC specialists. From the Bitdefender MDR Portal, you can review the following:
Dashboard: Quickly review graphs and statistics on activity, deployment progress, investigations, top impacted users and systems, active licensing, threat hunt data, and more.
Activity Section: Track investigations and threat hunt activity, including analysis results and recommendations.
Recommendations: Review recommendations on threat activity, hunts, and investigations delivered by the Bitdefender MDR.
Tickets: Open and monitor cases submitted to the MDR Security analysts.
Reports: Access the flash, after action and monthly reports delivered by the Bitdefender MDR team.
Documents: Exchange valuable information such as screenshots and logs with the MDR team.
Service Management: Complete or update service details.
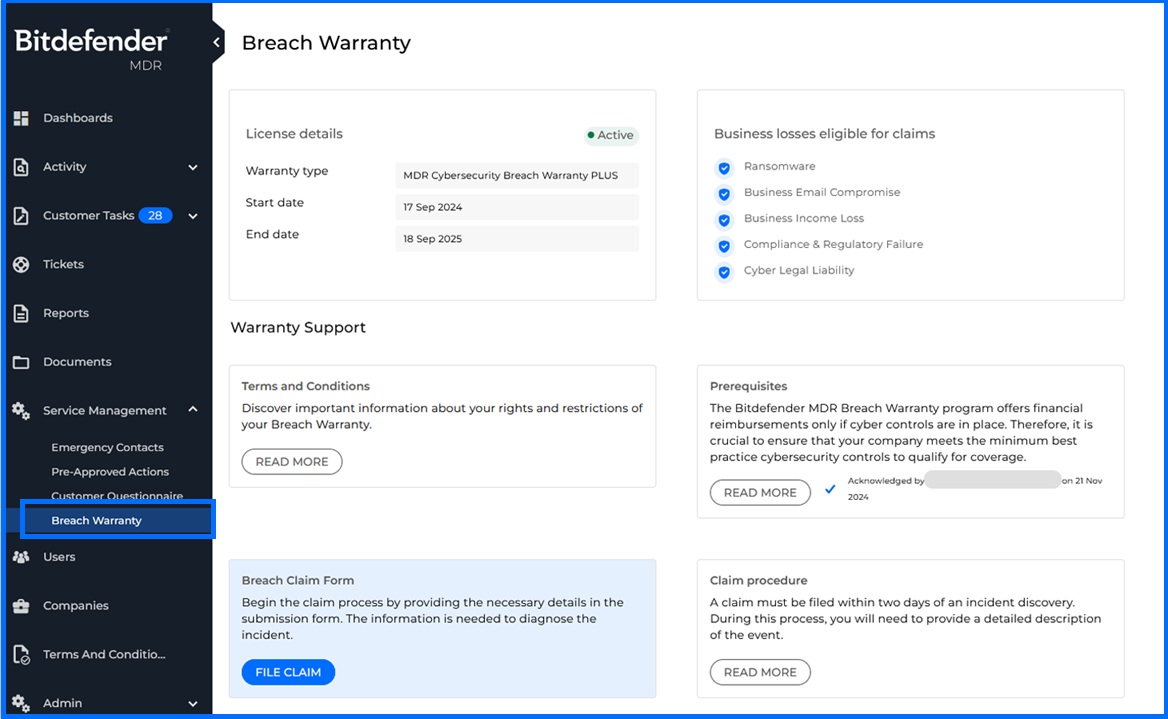
Emergency contacts: Provide a list of people that the SOC team can reach out to in case of an emergency.
Pre-approved Actions: You can enable the SOC team to take certain actions without explicit approval, whenever needed.
Customer Questionnaire: Providing detailed answers to questions you will help build Threat Modeling.
Cybersecurity Breach Warranty: You can access the Breach Warranty page to file a claim in case of any incident eligible for compensation. For detailed information about Cybersecurity Breach Warranty, please refer to our Bitdefender Support Center here.
Users: Create and manage user accounts with defined access levels:
Admin: Full access to the MDR Portal.
User: Can upload documents, submit tickets, and acknowledge investigations.
Read-Only: Can only read the data displayed in the portal.
Notifications
You do not need to consistently monitor the MDR Portal, you can configure email notifications to be sent to designated individuals within your company whenever a new incident, investigation, or report is generated. This ensures timely awareness of critical security events.
Reports
Upon initial detection of a security incident, Flash Reports are generated to provide an early assessment of the situation. These reports serve as one of communication methods about suspicious activity detected in your environment. They include key points such as initially affected systems, the timeframe of the incident, a summary of what was detected, and actions taken by the Threat Response team.
Once the full investigation is concluded, you will receive After Action Report. This report details the precise sequence of events that unfolded during the breach attempt, including initial detection, subsequent actions taken, the response and recovery process, and the involvement of specific files, networks, and systems. The reports elaborate on the specific actions that were undertaken to identify, contain, and eradicate the threat, including steps such as the isolation of infected systems, patching of vulnerabilities, removal of malware, and any other measures taken to neutralize the threat and minimize its impact.

Our Monthly MDR Report provides a detailed snapshot of your security landscape. The report begins with an overview of general activities, such as agent and network activity, EDR alerts, and discovered threats. The case management section provides a detailed overview of all ongoing and closed security cases, outlining the nature of the threats, and steps taken for mitigation. The report closes with a thorough analysis of monthly security activity, highlighting vital statistics on threat detections, hunting endeavors, intelligence alerts, and case activities.
MDR Cooperation Models
The optimal cooperation model depends on various factors, including the expertise and resources of your internal security team, your organization's budget and risk tolerance, and your specific security requirements and objectives.
In the Co-Managed Security model, Bitdefender collaborates closely with your internal security team, fostering a shared responsibility for security operations. This collaborative approach facilitates seamless knowledge transfer, ensuring a deeper understanding of threats and best practices. Furthermore, it offers cost-effectiveness by optimizing resource allocation and leveraging the strengths of both internal and external teams. This model provides flexibility, allowing you to tailor the level of involvement and support based on your specific requirements.
For organizations seeking a more comprehensive solution, the Fully Managed Security model offers complete responsibility for security operations to Bitdefender. This model significantly reduces the operational burden on your internal IT teams, freeing them to focus on core business priorities. With 24/7 expert coverage, you can ensure continuous monitoring and rapid response to threats, even during off-hours.
Recommended Content
To understand the services available in Bitdefender offering, we recommend reading the next section, Services.
More Resources
Managed Detection and Response (MDR) official website: Managed Detection and Response (MDR)
To learn more about Bitdefender MDR services, please contact us through the MDR Inquiry Form
MDR ROI Calculator: MDR ROI Calculator Webpage
Bitdefender MDR Guided Tour: MDR Guided Tour with Click & Discover
Defeating Cyber Attacks with MDR: RAAS Scenario