Fileless Protection- Bitdefender TechZone
Fileless Protection defends against disk-less attacks by blocking PowerShell malicious commands and WMI exploits. Enhances security with the Command-Line Scanner and AMSI integration for robust Windows scanning.
Fileless malware attacks, unlike traditional file-based ones, do not write any content or part of their activity to disk and persist until the system is rebooted. Fileless attacks involve leveraging Living off the Land (LOL) techniques, using legitimate admin tools such as PowerShell and Windows Management Instrumentation (WMI), or attack tools like Mimikatz and Metasploit. These tools are employed to run scripts and load malicious code directly into memory. This strategy allows attackers to evade legacy antivirus software, which typically focuses on file-based, signature detection, and pattern analysis, while simultaneously leaving little evidence for forensic investigation. Evidence acquisition can only occur when a memory image has been obtained from a running affected system under investigation.
Fileless Attack Protection is crucial for thwarting these sophisticated attacks, as it actively detects and prevents malicious activities that occur solely in the system's memory.
Fileless Attack Protection
The Fileless Attack Protection mechanism is included as part of the Business Security Premium licensing and the Advanced Threat Security module for Monthly licenses. It is automatically configured to identify and prevent fileless malware during a pre-execution stage. This includes terminating PowerShell instances executing malicious command lines, blocking malicious network traffic based on URL queries and network resources, examining memory buffers before code injection, and preventing the code injection process. It's important to note that Exploit Protection technology focuses on preventing code injection, while Fileless Attack Protection only focuses on PowerShell scripts that use specific reflective code injection.
Fileless Attack Protection includes two types of configurations:
Antimalware Scan Interface Security Provider
Command-Line Scanner
Antimalware Scan Interface (AMSI) Security Provider
Our solution incorporates AMSI (Antimalware Scan Interface) to provide a powerful layer of fileless threat protection. AMSI acts as a bridge between your system and GravityZone, allowing it to scan various content types for malicious activity. This includes scripts (PowerShell, VBA, VBS, etc.), files, URLs, and more. Importantly, AMSI scans this content before it's executed, written to disk, or accessed, offering a proactive approach to stopping threats in their tracks. One of AMSI's strengths is its ability to de-obfuscate code before scanning. This means even if attackers attempt to disguise malicious scripts, AMSI can often see through the obfuscation and identify the true nature of the code.
However, AMSI does have limitations:
Limited Platform Support: AMSI is currently only available on Windows 10, Windows Server 2016, and newer versions, or updated Office 365 deployments with runtime Excel macro scanning.
Potential for Bypass: While robust, attackers may attempt to disable or bypass AMSI altogether.
Command-Line Scanner
This is where our proprietary Command-Line Scanner comes in. It complements AMSI by offering these key advantages:
Broader Platform Coverage: The Command-Line Scanner functions across various operating systems, including macOS, Linux, and older Windows versions where AMSI isn't available.
Layered Security Defense: By analyzing command-line activity and identifying patterns indicative of fileless attacks, the Command-Line Scanner can prevent malicious scripts or commands from executing, even if AMSI is bypassed.
Command-Line Scanner detects fileless attacks by analyzing command-line activities, finding patterns indicative of fileless techniques, and preventing the execution of malicious commands or scripts before they can compromise the system. It supports but is not limited to the following processes wscript, cscript, rundll32, regedit, and PowerShell. In Multi-Layered Security strategy, Command-Line Scanner cooperates with Advanced Threat Control which monitors process executions, and Exploit Protection which finds exploitation attempts to recognize and block potential threats. Through collaboration with Content Control technology, the scanning capability is enhanced to include files with command lines. This enables the scanning of all files to detect embedded commands, such as a .lnk file, determining their malicious status.
In essence, we believe in a defense-in-depth approach. While AMSI provides excellent protection within its supported environments, the Command-Line Scanner offers an additional layer of security for broader platform coverage and to mitigate potential AMSI bypass attempts.
Configuration
The setup for Fileless Attack Protection can be found in the Antimalware configuration, specifically under Policy configuration within the "On Execute" section. It is recommended to use this Protection layer to enhance the security posture and mitigate the risks.
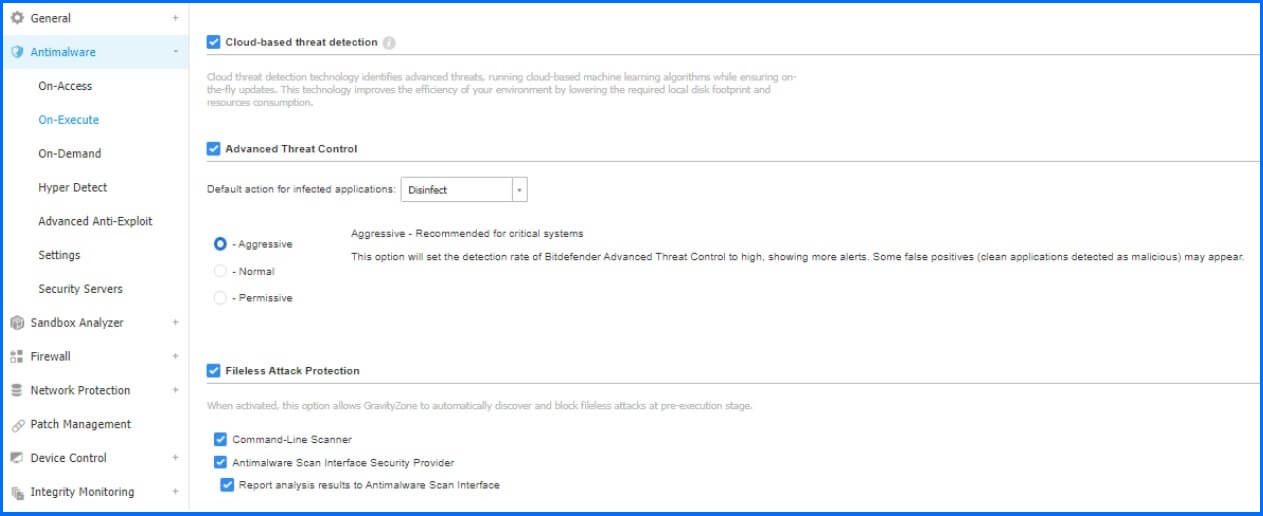
Detailed information about Fileless Protection configurations can be found at our Bitdefender Support Center here.
Recommended Content
To learn more about the technologies included in the protection layer we recommend reading the next article Sandbox Analyzer.
More Resources
Bitdefender Fileless Protection official website: Bitdefender Fileless Protection