Sandbox Analyzer - Bitdefender TechZone
Discover advanced threat detection with Bitdefender Sandbox Analyzer. Analyze suspicious content in a secure virtual environment, gain actionable insights, and protect against sophisticated malware.
Threat actors continually advance their tactics to evade detection. Attackers target vulnerabilities in software or systems that have not yet been identified or patched by the vendor. Polymorphic malware can change its code structure to bypass traditional signature-based detection. Additionally, some malware operates solely in memory, leaving little to no trace on disk, making it difficult to detect using conventional methods. Administrators require an isolated environment for safely detonating payloads to collect information. This informs decisions and effectively identifies and characterizes advanced threats.
Sandbox service analyzes suspicious files in depth by detonating payloads in a contained virtual environment hosted by Bitdefender, observing their behavior, reporting subtle system changes that indicate malicious intent, and providing actionable insight. For example, when a new unknown file is accessed by an end-user Machine Learning with HyperDetect is applied first. If a file requires further analysis, it is automatically sent to the cloud sandbox.
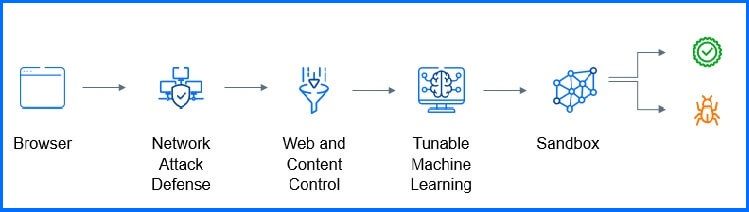
Based on the configured policy, the results of the analysis determine if the file will be allowed or blocked. If the verdict is that the file is malicious, the Bitdefender threat intelligence service will automatically be updated to ensure that all Bitdefender customers receive protection from this newly identified threat without having to detonate the same file again. Administrators can be confident that there is no performance impact on the endpoint, and that the risk associated with allowing a potentially malicious file to run on the endpoint is eliminated.
Detailed information about Sandbox configurations can be found at our Bitdefender Support Center here.
Sandbox Analyzer components
Bitdefender Sandbox Service offers a controlled environment for dynamic inspection by meticulously recording and analyzing all system changes during execution. When running the submitted sample, the environment closely resembles a real endpoint, complete with common applications and files.
It is crucial to remain undetected when dealing with advanced threats. Some of these sophisticated threats attempt to identify if they are running in an emulated environment such as a sandbox service. They do this to evade detection by altering their default behavior, making detecting and mitigating of their malicious activities even more challenging.
Throughout the process, our monitoring technology remains hidden while files are executed in a meticulously instrumented environment. PDF files are opened by Adobe Reader, documents by MS Office, and various anti-evasion techniques are applied.
Bitdefender Sandbox Service includes two main components:
The Prefilter service - runs a quick series of scans and analyzes files using various algorithms. If a verdict is determined, it will be returned, and the file will not be sent to Sandbox.
Sandbox service - detonates files in a sandbox environment.
Prefilter service
Prefiltering employs highly aggressive malware detection techniques rooted in Machine Learning and heuristics to precisely filter files for detonation. By leveraging machine learning capabilities, this system constantly learns from vast datasets, empowering it to detect potential threats or clean files precisely and rapidly with exceptional accuracy. This technology not only boosts efficiency but also delivers substantial cost-reduction advantages. Bitdefender prefilter service focuses on executables, documents, and archives as their primary targets for analysis.
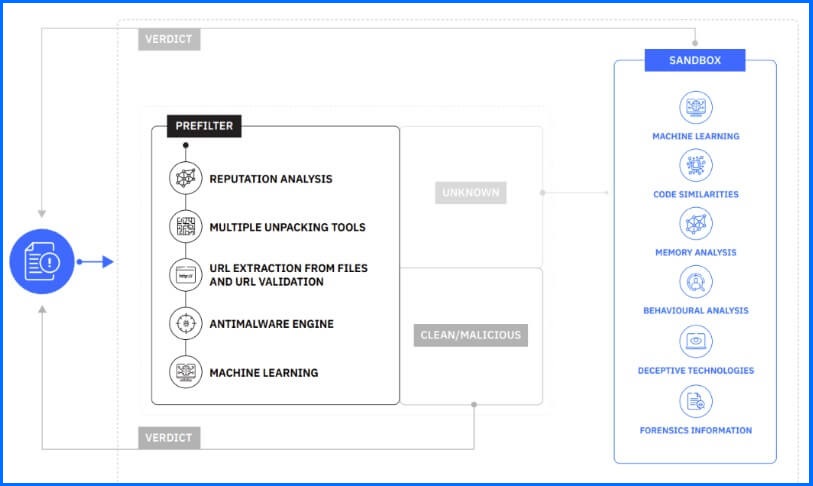
At Bitdefender, we have been using machine-learning algorithms since 2008, and we hold more than 480 patents for core technologies including machine-learning algorithms to detect malware and other threats, and anomaly-based detection techniques vital to detect and prevent new and unknown threats.
Sandbox Service
Bitdefender offers a range of files supported by the sandbox service to make the solution effective against a wide range of attack vectors, including malicious applications, documents, archives, emails, and scripts. A detailed list of supported file types and extensions was described on the GravityZone Support Center.
The sandbox service, apart from its integration with Bitdefender GravityZone where the samples can be sent automatically or manually by the administrator, can also function as a stand-alone analysis tool. It can be integrated with any solution that verifies all network traffic scanning the files. The Bitdefender Sandbox Service utilizes an asynchronous API. Upon submitting a file or URL for analysis, the service generates a unique Job ID which allows security specialists to retrieve the analysis result and report.
For efficient and effective monitoring, the sandbox records and observes the following behaviors:
Every file that was modified, deleted, created, or changed
Every registry key that was modified, created, or deleted
Every process created, terminated or injected
Every API instruction executed
Every network connection
In the controlled virtual environment, we thoroughly monitor and analyze all activities that occur, along with system-level changes, following the execution of any potential threat.
The sandbox includes several detection mechanisms based on behavior monitoring, including ransomware identification to prevent data encryption and potential extortion and data exfiltration to safeguard sensitive information from unauthorized access and data breaches. It can detect zero-day exploits to protect against newly discovered vulnerabilities and botnet identification which helps in countering coordinated and large-scale cyberattacks. Additionally, it identifies several malicious actions like malicious downloads and persistence, and the presence of bootkits, which is crucial for preventing attacks that manipulate the boot process and gain persistent control over the system.
Sandbox reporting
Bitdefender Sandbox Analyzer boasts a uniquely comprehensive and elegant visualization chart that delivers a complete view of each detection and its underlying context. Within the report, users can access information about known threat actors and the family of the detected infection. It provides details on the detection process, including the security mechanism responsible for identifying the infection and submission information such as the command line, MD5 hash, and extracted data.
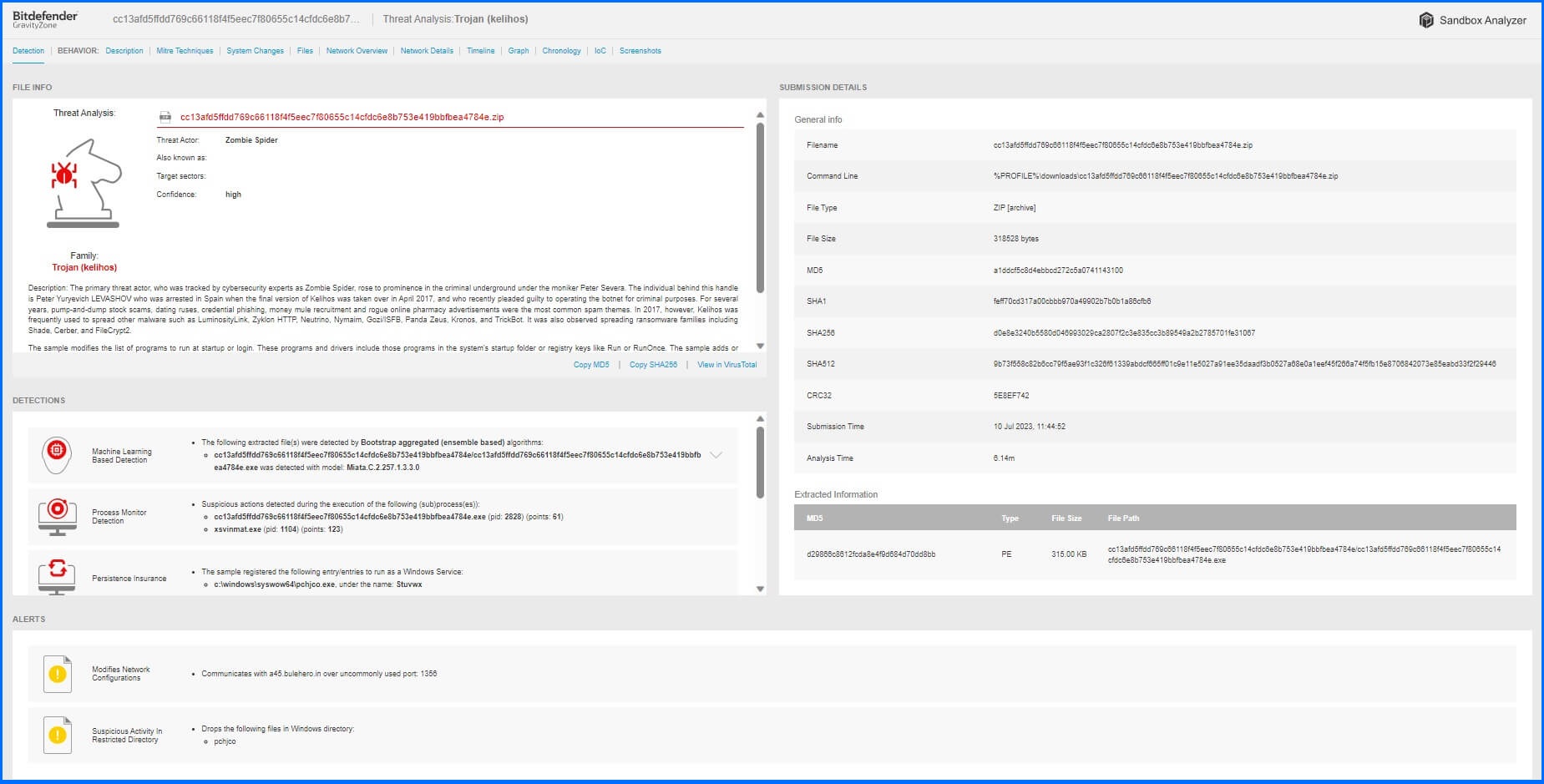
The tool also offers valuable insights into the behavior of the threat and its mapping to Mitre techniques. It can learn from the behavior of the threat and present a timeline display of the changes it attempted to make to the system, along with tree graphs depicting its interactions and structure.
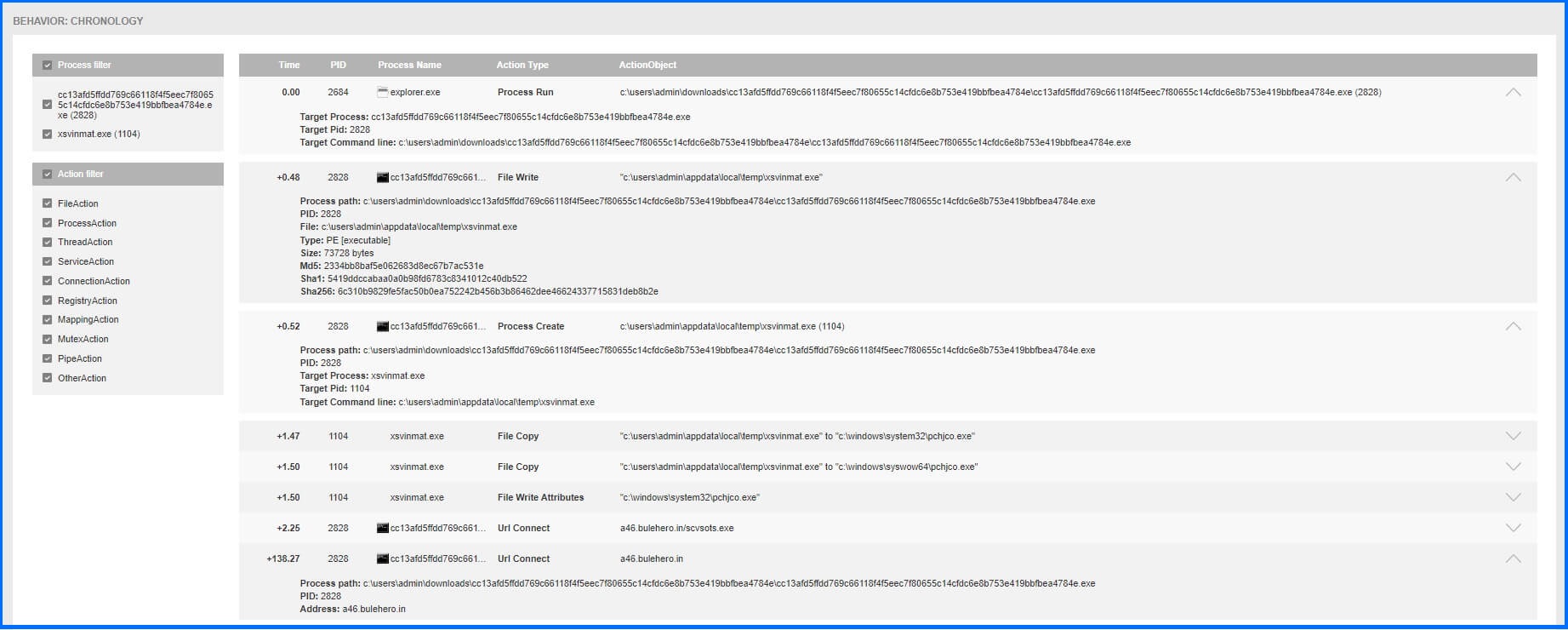
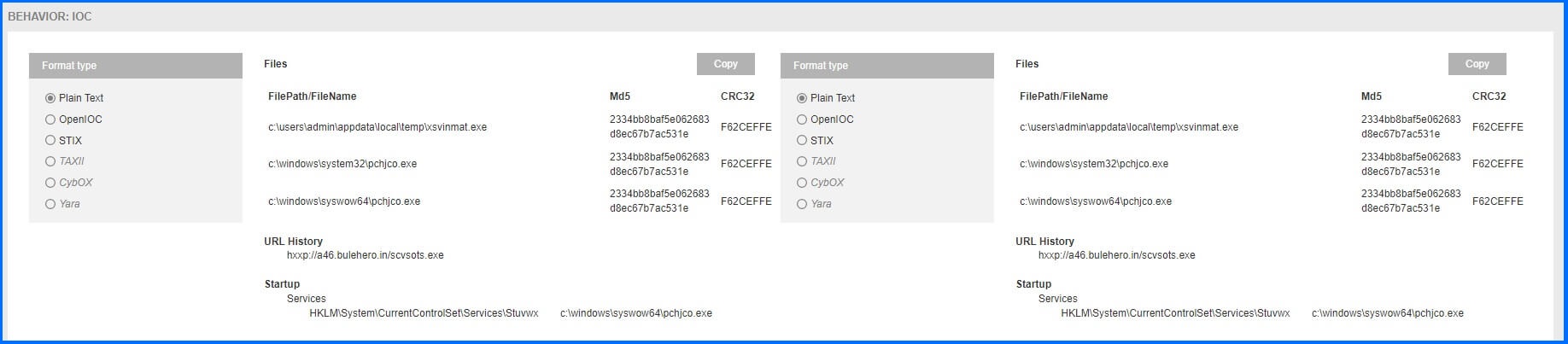
Additionally, it captures a screenshot of the message or error the user encounters when the system is infected, such as a ransomware note. Administrators have access to external related information on Virus Total to check verdicts from various antivirus engines and all the IoC artefacts, providing essential indicators to detect and prevent similar threats in the future.
Recommended Content
To learn more about the technologies included in the protection layer we recommend reading the next article Ransomware Protection.
More resources
Bitdefender Sandbox Analyzer official website: Sandbox Analyzer - Bitdefender GravityZone