Malware Protection - Bitdefender TechZone
Discover the vital role of the malware protection component within Bitdefender GravityZone comprehensive multi-layered security strategy, ensuring robust defence against evolving digital threats.
Malware is software designed to harm or compromise a computer system. Not all malware is explicitly malicious (for example, some Potentially Unwanted Applications, or PUAs, might be intrusive but not outright harmful).
Malware is not static, it constantly evolves. We detect approximately 1000+ new, previously unseen malware samples every minute, highlighting the dynamic nature of the threat landscape.
To protect against these threats our multi-layered security strategy, where all components work together to create overlapping security measures, includes the Malware Protection module. This module is a key component that recognizes complex attacks and unusual actions before they happen. By leveraging core functionality integrated into our Endpoint Protection Platform, it offers flexible modes of operation, allowing you to customize security profiles based on your system needs and balance performance with protection.
Operational Models
Antimalware modules prevent new malware threats from entering the system by scanning local and network files when they are accessed (opened, moved, copied, written, or executed), boot sectors and potentially unwanted applications (PUA).
Malware protection behaves differently depending on how the security agent installed on endpoints is set up to run:
Detection and prevention mode: This operation mode sets the Antimalware module to detect and block threats. The agent automatically attempts to perform the best disinfection method available, this can be removing the malicious code from an infected file or removing the malware and it’ is tracesd from the system.
EDR (Report only) mode: This operation mode exclusively enables On-execute scanning, set to only report threats, and not blocking them. This mode of operation is available for users who want to install a lightweight EDR solution in their environments, that can run alongside other prevention solutions. The installation package includes only Advanced Threat Control, EDR Sensor, Network Protection with Content Control and Network Attack Defense functionality.
Protection Profiles for core components
Malware protection can be customized across various tiers. Within the Policies configuration, administrators can set it up in both the On-Access and On-Demand scanning sections.
Depending on the chosen scanning option, administrators have the flexibility to select from three predefined profiles, each offering varying levels of protection. Alternatively, they can create a custom policy and fine-tune the configuration to their specific requirements. These profiles define the trade-off between security and system performance, allowing for tailored security measures.
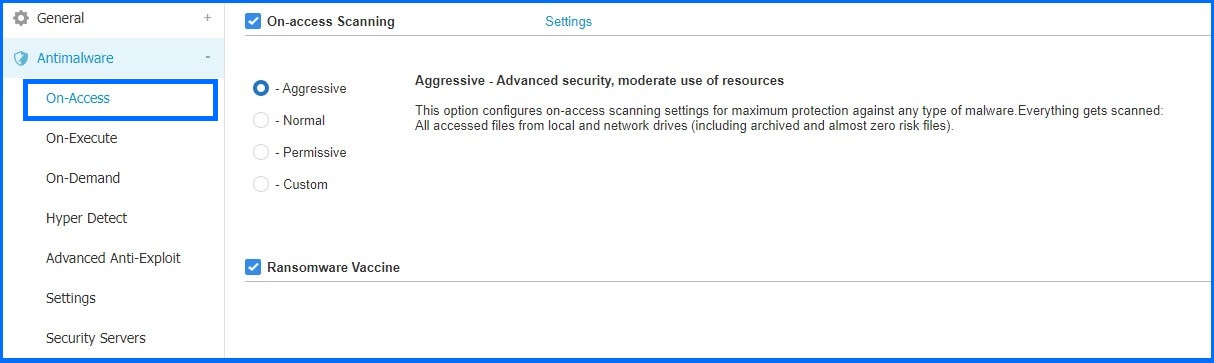
The core difference between the Normal, Aggressive, and Permissive scanning profiles is the detection threshold. After a file, process, or item is analyzed by the scanning engines, it collects "scores." The profiles represent different thresholds for this accumulated score, which determines if the file or process is classified as malicious or not. The more aggressive the threshold (meaning fewer points are required to trigger a detection), the higher the security, but this also increases the potential number of false positives (FPs) and results in a higher consumption of endpoint resources (CPU/RAM).
The default Permissive Profile selectively scans newly modified or updated local and remote files, as well as Potentially Unwanted Applications (PUAs). This profile can be beneficial for systems with lower processing power or older hardware, although it is important to note that it is not the recommended choice for optimal security.
In contrast, the default Aggressive Profile offers the highest level of protection by thoroughly scanning all types of malware. In addition to what the Permissive Profile scans, it also includes the scanning of archives, boot sectors, and keyloggers, providing a comprehensive defence against potential threats.
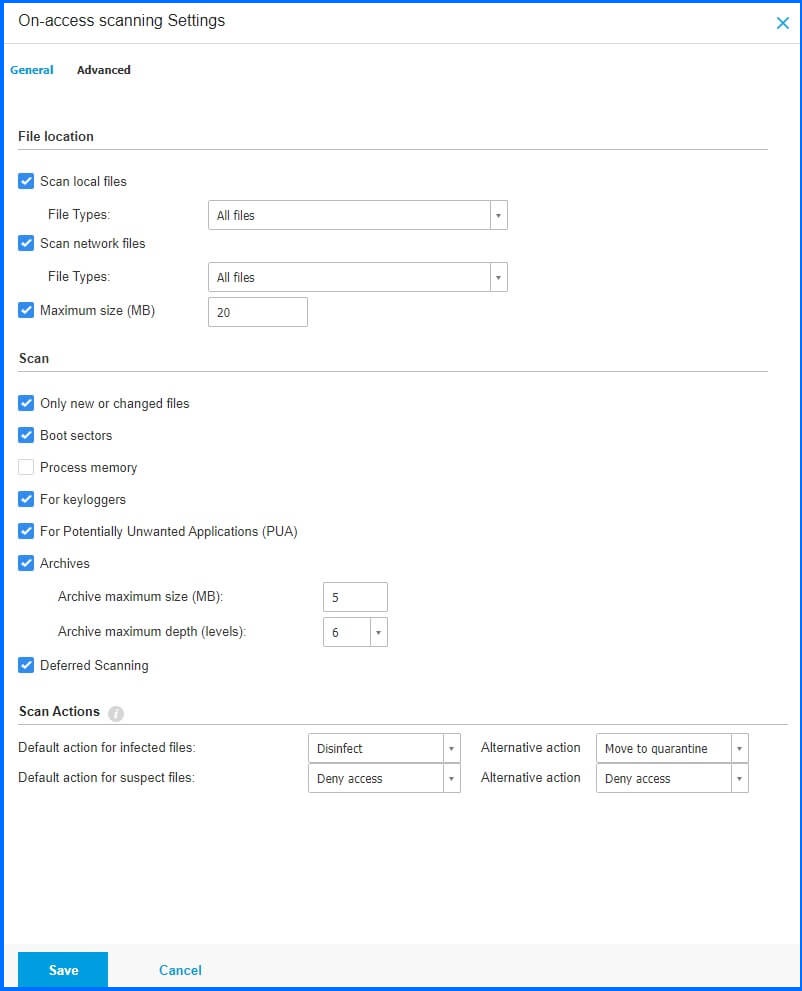
The administrator faces the challenge of striking a balance between system protection and performance optimization when configuring their settings. There is no one-size-fits-all recommendation, as it depends on the specific needs and capabilities of the system.
For instance, consider the functionality of scanning inside archives, which is known for being a slow and resource-intensive process. Archives containing infected files may not pose an immediate threat to system security; their impact is only realized if the infected files are extracted and executed. The primary configuration mechanism designed for detecting Keyloggers possesses the ability to both recognize and prevent any endeavours to capture keystrokes and transmit them to a malicious operator over the Internet. Thanks to the robust, multilayered security approach and the presence of overlapping protective measures, even if this parameter is deactivated, other protection modules will continue safeguarding the system. Additionally, rootkits are a category of software that can potentially provide an attacker with elevated, administrator-level access to the system. These various factors must be carefully weighed and configured according to the unique security and performance requirements of the system in question.
It is important to emphasize in this section that the Ransomware vaccine parameter provides immunity to machines against known ransomware, effectively thwarting the encryption process, even in cases where the computer is already infected. By default, the Ransomware vaccine feature remains deactivated. Bitdefender Labs continuously assesses the behaviour of prevalent ransomware strains, and with each security content update, new signatures are delivered to counter the most recent threats.
Detailed information about Malware Protection configurations can be found at our Bitdefender Support Center here.
Functionality
The Malware protection features within Bitdefender GravityZone can be divided into two primary components: core functionality and Hyper Detect. In this in-depth section, we will offer an overview of both elements.
Core components
One of the fundamental components of this system is designed to thoroughly scan various types of local content, including files, images, installers, emails, documents, memory buffers, and even boot sectors. By its design, this system can unpack files and extract their underlying code for later analysis. This is a crucial step as malicious code often employs various packing and obfuscating techniques to conceal its harmful intent. In many instances, these techniques involve not so frequently used system APIs, APIs that usually are not supported by emulators.
Upon extraction, the scanning process proceeds to employ several local emulators capable of simulating the behaviour of the analyzed content. These emulators are vital for behavioural analysis, evaluating binaries, JavaScript, VBScript, and other code to discern potential threats. Content analysis encompasses a range of verifications, including token extraction, identification of potential exploits, tracking of execution flow APIs, extraction of code and payloads, string verification, and cryptographic analysis.
With this wealth of data at its disposal, the system conducts a multifaceted analysis using heuristic, rule-based engines, and behavior-based detection methods. It is important to note that this analysis is not limited to static examination alone. Instead, it leverages the extraction data to create new scanning features that are incorporated into our Machine Learning models, enhancing the overall security posture of the system.
The disinfection capabilities enable us to eliminate the malware code from infected files and restore the original file. By default, if an infected file is detected, the Bitdefender security agent will automatically attempt to disinfect it. If disinfection fails, the file is moved to quarantine to contain the infection. However, it is important to note that for certain types of malwares, disinfection is not feasible due to the file being entirely malicious and the infected file is deleted from the disk. In addition to removing the malware code from infected files, the disinfection module goes a step further by identifying and erasing any other traces left by the malware. For instance, if an installer not only drops malware but also writes a registry key to ensure the malware runs at startup, the disinfection module will detect and delete the associated registry key, ensuring a thorough cleanup of the system.
Hyper Detect
Hyper Detect is our tunable Machine Learning functionality that can be configured via the Policies configuration.
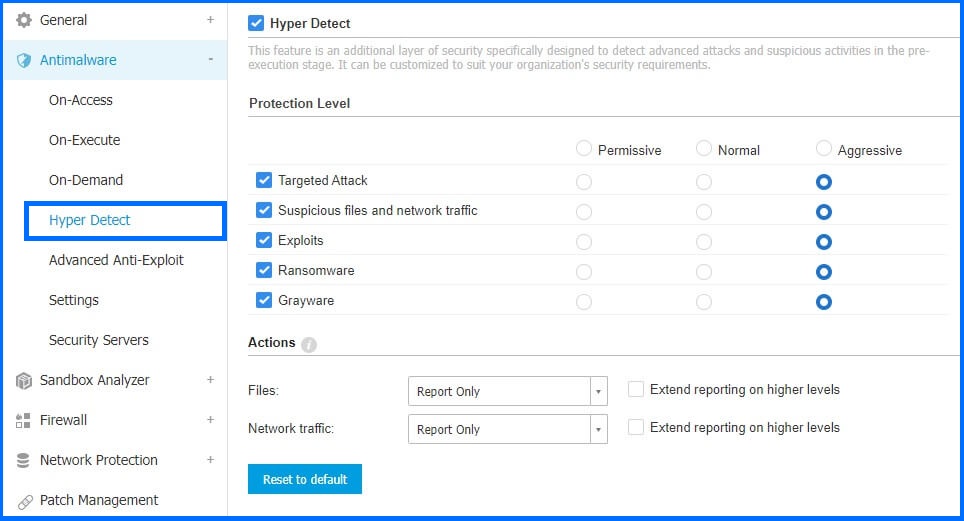
Within the configuration settings, administrators have the flexibility to fine-tune five distinct protections by levels ranging from Permissive to Normal and Aggressive heuristics detection. A higher level of aggressiveness in detection is inclined to identify new and previously unseen malware, albeit it may occasionally trigger false positives. Conversely, a more Permissive heuristic engine tends to yield a lower false positive rate but may result in reduced detection capabilities.
Detailed information about Hyper Detect configurations can be found at our Bitdefender Support Center here.
Functionality Deep-dive
Hyper Detect technology constitutes a specialized segment within the core components, featuring heightened heuristics detection capabilities aimed at identifying advanced attacks and suspicious activities during the pre-execution phase. It excels at recognizing a wide array of abusing legitimate tools, such as Rclone, Gsudo, TacticalRMM or Sysinternals suite. It is important to note that this detection is critical for maintaining the security and integrity of systems, as it helps identify potential misuse or malicious activities that could compromise data and networks. Effective detection of legitimate tools being abused allows organizations to defend against advanced threats.
From a file-centric standpoint, it is of utmost importance to identify files that have been packed with an unfamiliar packer or those utilizing a packer commonly associated with malicious intent. Additionally, discerning files compiled with well-known compilers such as Visual Studio or Delphi is equally crucial. This proactive approach helps to flag potential threats and suspicious files.
Furthermore, the capability to discern unconventional paths and names for executable files, as well as detect unusual process correlations, plays a pivotal role in comprehensive security. This includes identifying executable files with atypical directory locations and file names and recognizing processes that show abnormal parent-child relationships.
Recommended Content
To learn more about the technologies behind the Protection layer, we recommend reading the next article Process Protection.
More Resources
GravityZone Security Products official website: GravityZone Security Products