Process Protection- Bitdefender TechZone
Explore GravityZone Process Protection, a proactive defense against advanced malware threats. Learn about Advanced Threat Control (ATC) and Process Introspection (PI) strategies for real-time threat detection.
Countering advanced and evasive malware is a constant challenge. Traditional signature-based approaches fall short when dealing with rapidly emerging threats. One part of our strategy to deal with previously unseen malware is Process Protection. Built on process behavior analysis, this technology offers a strong safeguard against both known and unknown threats. Process Protection is inherently proactive. It doesn't rely on known signatures; instead, it proactively identifies new and previously unseen malware based on their behavior. This provides a strong defense against rapidly emerging threats, such as ransomware outbreaks.
In this article, we dive deep into two key elements of Process Protection: Advanced Threat Control (ATC) and Process Introspection (PI).
ATC is mainly concerned with finding and stopping bad processes from doing harmful things, whereas PI is all about finding and stopping any processes (even the ones we trust) from turning bad after they've been compromised. For instance, ATC would spot malware trying to sneak into 'chrome.exe,' but PI would catch 'chrome.exe' when it tries to do something bad after being attacked.
GravityZone implements a multi-layered approach to security, often deploying multiple technologies that complement and overlap each other. ATC and PI use a mix of user-mode and kernel-mode integrations to enhance performance, stability, and minimize the attack surface. This makes them more resilient against user-mode attacks and fortifies their defenses against the majority of user-mode-based evasion techniques, including DLL unhooking.
Advanced Threat Control
ATC is a proactive and dynamic behavioral detection technology that continuously monitors process activities in real-time, including groups of processes. Its primary objective is to identify whether these activities exhibit malicious or benign behavior. ATC utilizes over 300 heuristics for detection. A selection of examples includes:
Heuristics for monitoring credential access – credential dumping, access to the SAM registry database, monitoring key presses…
Heuristics for persistence – scheduling tasks, registering a service, adding autorun entry…
Heuristics for disabling critical services – disabling Windows Update, security solutions or features, terminating critical processes…
Heuristics for suspicious file operations – replicating, dropping files with double extension, hiding files…
Heuristics for ransomware – atypical file enumeration or operations, backup deletion, known malware file extensions….
Heuristics for process injection – process hollowing, DLL or thread injections, reflecting DLL injections…
To look at the ransomware heuristics as an example, ATC takes a proactive stance to detect ransomware before it inflicts any damage on a compromised system. Most ransomware strains are identified in their early stages of execution, typically during activities such as reconnaissance, defense evasion via code injection, or attempts to establish persistence. The next layer of defense involves identifying ransomware when it attempts to remove backups, for example, by erasing volume shadows utilized by some antivirus vendors for file recovery (our proprietary Ransomware Mitigation uses a different approach). The final line of defense aims to detect ransomware very early in the encryption process to minimize the damage caused. In the event of suspicious file modifications, ATC promptly reports them to the disinfection engine, enabling ransomware remediation, provided that backup and restore technology is available.
In addition to heuristics, ATC leverages machine learning, which involves the analysis of more than 340 features extracted from groups of processes during their execution, including behavioral actions like API calls. These 'features' represent various characteristics or attributes that are relevant to process behavior. This machine learning approach utilizes supervised learning, a technique where an algorithm is trained on labeled data to recognize patterns and make predictions based on input features, helping to minimize false positives and detect threats on the client side.
Keep in mind that ATC is available on Windows and macOS (full version), and on Linux (report-only mode).
Process Introspection
Process Introspection is an additional layer of protection against advanced in-memory attacks. It operates by applying advanced security checks during key operations performed by processes, such as process creation or module loading. Through these checks, we can determine whether an operation occurred within a malicious context or if a process has been compromised. These key operations include, but are not limited to:
Loading certain modules (DLLs) that can be used for malicious purposes (for example network communication to C2, or ransomware encryption via crypt APIs)
Creation of child process (for example remote code execution vulnerability)
Creation of a new thread (either in the same process or in an external process)
Injection of code into another process
Loading kernel mode modules (drivers)
Creating a new socket (that can be potentially used for C2 communication)
These heuristics examine the process state to determine whether it has been maliciously altered. Notably, PI focuses on identifying malicious states, rather than merely monitoring malicious behaviors. For example, it can detect the process hollowing, regardless of the specific technique used.
A key distinction of PI is that it operates in kernel mode, eliminating the need for injecting user-mode components or placing hooks into protected processes. This improves performance, stability, and reduces the attack surface. PI exhibits resilience against user-mode attacks and remains resistant to most user-mode-based evasion techniques such as DLL unhooking. It has been validated against various post-exploitation frameworks (such as Metasploit, Cobalt Strike, Powershell Empire…) and their payloads.
Visualizing Process Introspection in ATC
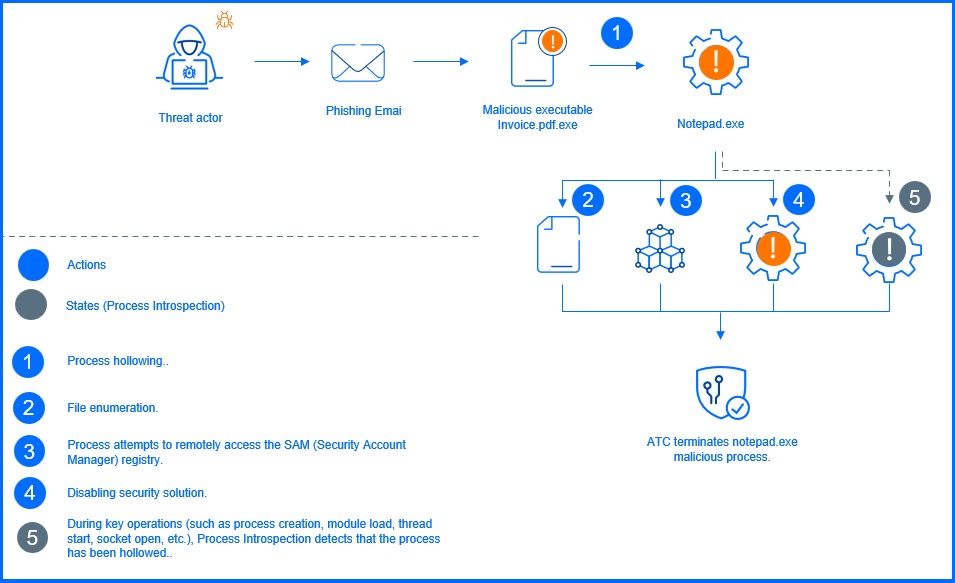 |
Configuration and Behavior
In GravityZone, a probability score is assigned to everything, including files, processes, users, and machines. Specifically, this score reflects the likelihood that a process poses a threat. Both ATC and PI contribute to determining this process score, with each suspicious behavior influencing the overall rating. When this rating reaches a predefined threshold, an alarm is triggered, indicating that the process is considered highly likely to be a security threat. The threshold is determined as follows:
The ATC/PI detection module calculates a behavioral score for each application
If uncertain, the code buffer can be forwarded to antimalware engines for additional analysis
If the score exceeds the threshold configured in the current profile, an action will be initiated for the application, which may involve terminating the process
Available configuration options, including profile thresholds for applications and actions to be taken when infected applications are detected, are available under GravityZone policy in the section Antimalware -> On-Execute.
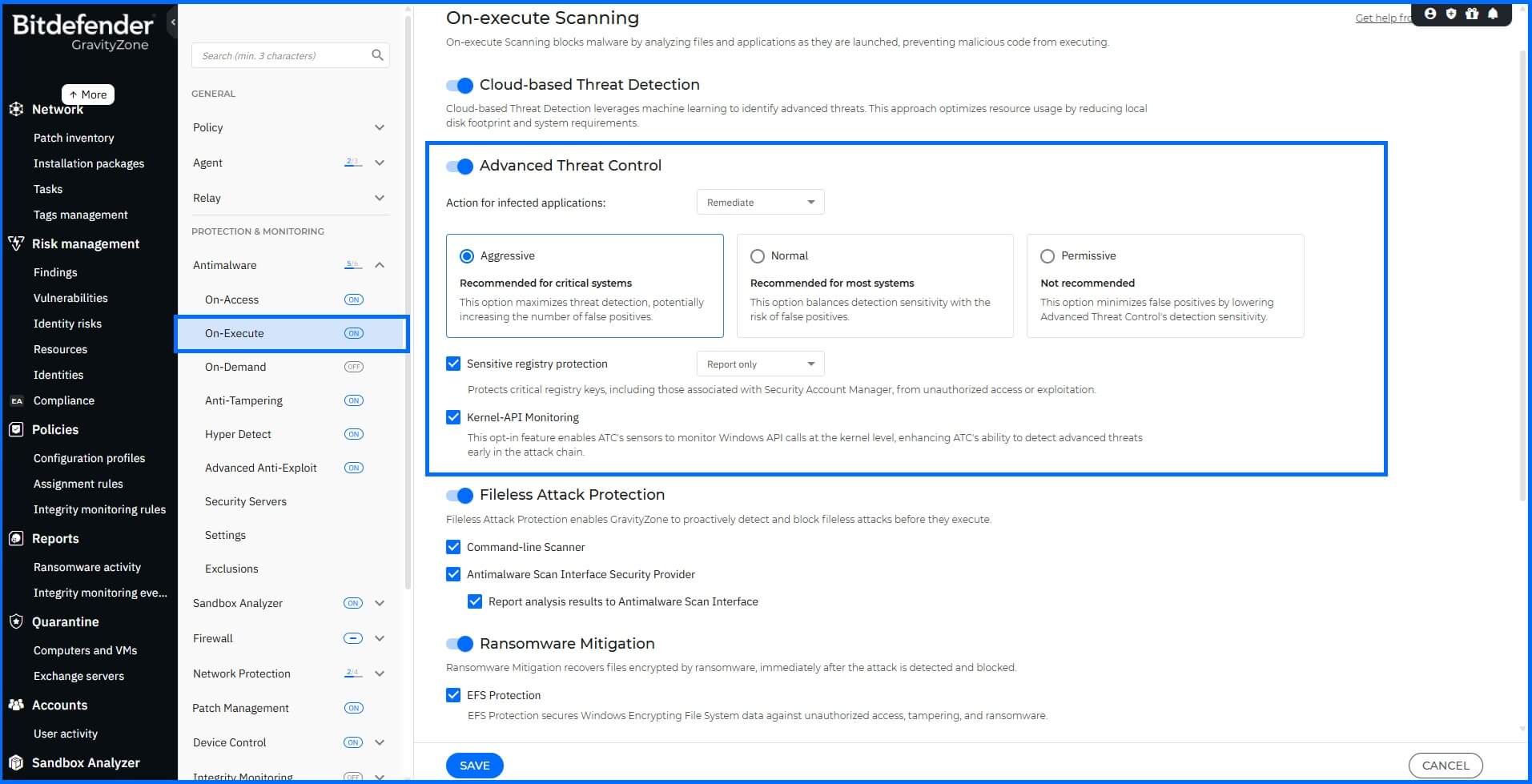
The ATC module supports exclusions from policy configuration for various types, such as file, process, file hash, certificate hash, threat name, and command line. Exclusion options can be configured in the Antimalware settings.
ATC offers configuration options for profile thresholds, each with a different approach:
Normal Mode: ATC is optimized for this mode, it is fine-tuned to minimize false positives.
Aggressive Mode: This configuration sets ATC to operate in a more aggressive manner. This mode may raise the risk of false positives for companies frequently changing or developing new applications and results in a higher consumption of endpoint resources (CPU/RAM).
Permissive Mode: In this mode, ATC provides processes with more freedom to perform potentially risky operations without immediate detection. While this can reduce false positives, it significantly increases the risk of false negatives, where malicious activity goes unnoticed. We recommend using this mode sparingly and only in specific cases. Whenever possible, it's advisable to create local exceptions to manage false positives instead of relying on this mode.
Sensitive Registry Protection, safeguards critical registry keys, including those associated with the Security Account Manager (SAM), from unauthorized access or exploitation via Windows Remote Registry Protocol (MS-RRP), which is used to remotely manage the Windows registry. For example the SAM registry stores hashed passwords for local user accounts. Attackers can use exploitation techniques like malicious registry key dumping to extract the SAM registry and then attempt to crack the hashed passwords. If ATC is active with the Kill Process action, it will terminate the process that attempts to access the registry.
Kernel-API Monitoring enables advanced kernel-level detection of system integrity exploitation attempts. This functionality allows ATC to identify malicious attempts to manipulate kernel APIs for privilege escalation, such as unauthorized modifications to process tokens, indicating an attacker's effort to gain elevated system privileges. For optimal deployment, the module is disabled by default, and we recommend testing it in a controlled environment first to verify its impact and compatibility with your system.
Detailed information about ATC configurations can be found at our Bitdefender Support Center here.
Recommended Content
To learn more about the technologies included in the protection layer we recommend reading the next article Software Exploit Protection.
More Resources
Use our tool to generate a fake malicious detection and test ATC: Test file.