Ransomware Protection - Bitdefender TechZone
Combat evolving ransomware threats with Bitdefender's multi-layered defense. Intercept malicious software, fast incident response, and efficient file recovery for robust protection.
Everyone can fall victim to ransomware attacks. Attacks are increasing in both complexity and impact, targeting organizations of all sizes. Hackers often use phishing attacks, compromise services, or exploit zero-day or unpatched vulnerabilities to gain initial access to victims' networks.
Primarily ransomware attacks were isolated incidents, with criminals targeting specific companies. However, as the digital economy grew, these individual attacks evolved into large-scale extortion operations. As a result, ransomware slowly migrated to a model known as "Ransomware-as-a-Service" or RaaS, which operates on a subscription-based model. This allows intermediary hackers to use pre-developed ransomware tools to execute attacks.
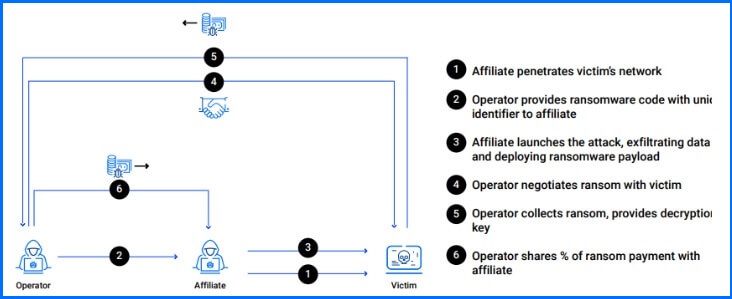
Once hackers gain access to an organization, they typically initiate their attack by staging malicious tools, conducting network reconnaissance, spreading laterally across the network, and establishing persistence. Subsequently, they attempt to escalate their privileges to domain administrators, destroy backups, and, in some cases, exfiltrate sensitive data before deactivating security systems and deploying ransomware.
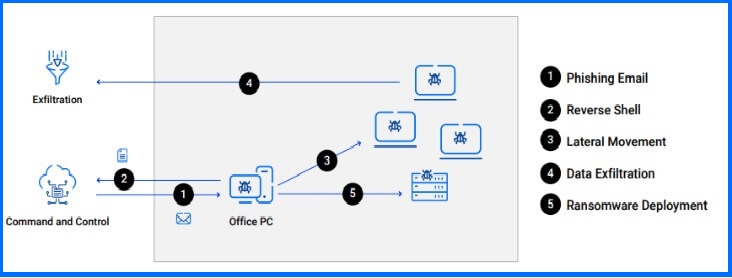
Executing targeted ransomware attacks is often a challenging task. As a result, the process from initial compromise to network encryption can span from days to weeks, or even months. This allows organizations to identify and halt the attack before the final encryption takes place. However, establishing a strong ransomware defense requires a collaborative effort involving technology, people, and processes.
The best protection against modern ransomware attacks is to implement a defense-in-depth architecture. Start with reducing the attack surface, combined with automated prevention controls to prevent most security incidents. For the remaining incidents, you must rely on security operations, enhanced with great detection and response tools.
Bitdefender provides comprehensive ransomware protection from initial access to execution using multiple layers of defense. These layers generate multiple detections across the GravityZone platform, enabling rapid response and preventing attacks.
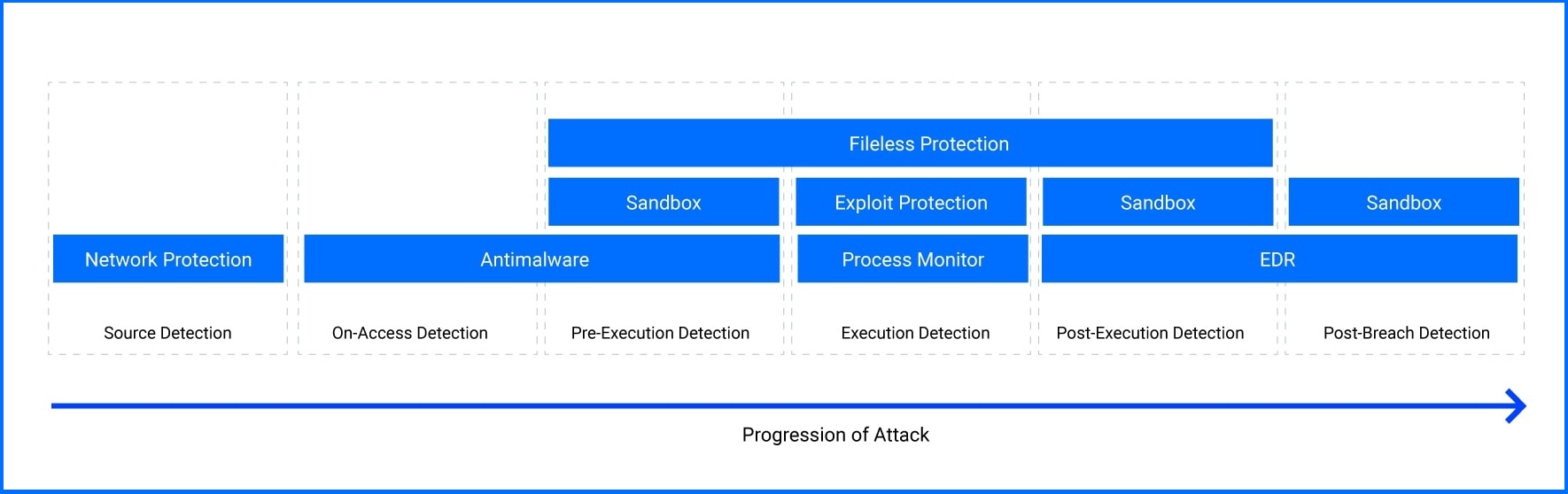
To understand how these technologies work together, you should read our ransomware whitepaper.
Ransomware mitigation
With the Ransomware Mitigation module, you can protect your data against ransomware attacks. GravityZone allows you to monitor your endpoints and block processes that attempt to alter your data. When an attack is blocked, you'll receive a report in GravityZone, including information about the user session on the endpoint and the impacted files. You have the option to restore your files manually, using the console interface, or automatically when an attack is detected and blocked..
It is highly advisable to enable the functionality directly from GravityZone, as ransomware protection serves as a critical third line of defense. In instances where other security layers, such as Fileless Protection and Exploit Protection, are unable to detect the threat, ransomware protection steps in to safeguard your systems and data.
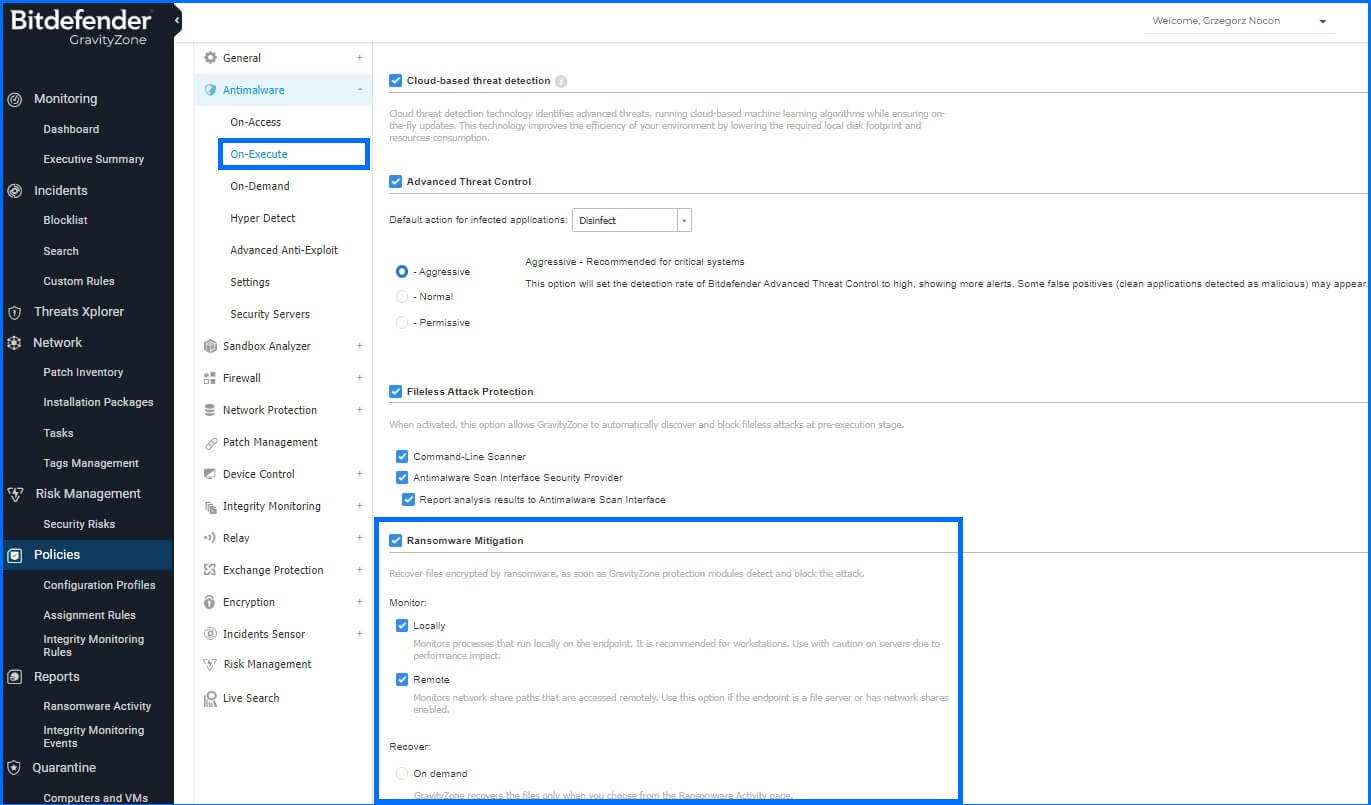
By activating this feature, you add an extra layer of protection against the growing ransomware attacks. This advanced technology encompasses three primary areas: operating system level, files, and cloud support. Each area focuses on specific aspects of ransomware defense, ensuring comprehensive protection against evolving attack techniques
Detailed information about Ransomware mitigation configurations can be found at our Bitdefender Support Center here.
Operating system level
At the Operating System level, Bitdefender utilizes mini filters to intercept process creation and file access. We categorize processes into groups based on various criteria, including digital signature, reputation (leveraging our technology Process Protection), and identification of suspicious behavior such as process injection and unethical techniques like a doppelganger.
In addition, we also consider insights from other Bitdefender technologies, such as Process Protection, Anomaly Detection, and Integrity Monitoring to identify potentially suspicious behavior. By analyzing these factors, we can determine if a process falls into an untrustworthy group. Once an untrustworthy group is identified, we closely monitor its actions, such as file creation, deletion, renames, writing, and reading. We track these actions either for a specific duration of time or until a certain number of actions have been performed, whichever comes first. This monitoring allows us to promptly identify any malicious or suspicious activities performed by the identified group of processes.
By employing these interception techniques and monitoring mechanisms, Bitdefender ensures a proactive approach to security, enabling the detection and prevention of potential threats at the operating system level.
Files level
During the files monitoring, Bitdefender takes proactive measures by preemptively backing up files based on the potentially destructive actions a process may undertake. This allows for a comprehensive analysis of the changes experienced by the files. However, this process presents various challenges as file encryption can occur in different ways, such as in-place encryption, encryption in a separate file, or within an archive.
To determine the extent of file modifications, Bitdefender examines the transformation of the "encrypted" file. It analyzes specific portions of the file and applies statistical formulas, including entropy and chi-square tests, to detect indications of file encryption.
Additionally, the file type is considered, as certain file types inherently possess internal structures that resemble encrypted files. For instance, documents (.docs) and spreadsheets (.xlxs) are essentially packed scripts, while archives exhibit high entropy values. The underlying principle behind these statistical checks is that encryption, whether full or intermittent, tends to homogenize the distribution of bytes within a file. By observing this uniformity, Bitdefender can identify potential instances of file encryption.
Our heuristics for file access and encryption are derived from a comprehensive analysis of ransomware samples provided by our Bitdefender Labs team. This analysis is an ongoing process, with daily testing using fresh ransomware samples in our specially designed automated system. To ensure accurate detection and minimize false positives, we continuously monitor cloud metrics and gather feedback from our customers.
Bitdefender offers an additional mechanism that focuses on monitoring locally exposed shares on servers, to detect and protect against potential attacks originating from other computers within the same network that have write access rights to the shared data. One important notice is that in this scenario, the attack might originate from a different computer where Bitdefender might not be installed, and we lack the indicators typically available when monitoring processes or groups of processes. Bitdefender's solution diligently monitors the activity on exposed shares, keeping a vigilant eye on potential ransomware threats. By leveraging its advanced detection mechanisms and security measures, Bitdefender helps safeguard shared data and mitigate the risk of unauthorized modifications or encryption from external sources within the network.
The Limits of VSS in Ransomware Recovery
The Volume Shadow Copy Service (VSS) is a part of the Windows operating system responsible for creating point-in-time snapshots of your files and volumes, allowing you to revert files or entire systems to a previous state. However, VSS is a frequent target of ransomware groups. When VSS is disabled, it prevents the creation of new Shadow Copies, and if existing Shadow Copies are deleted, you lose a critical recovery option. Disabling VSS is part of almost every modern ransomware playbook, as you can see in the real-life case example below, where we captured Ryuk Ransomware in Root Cause Analysis targeting VSS for deletion.
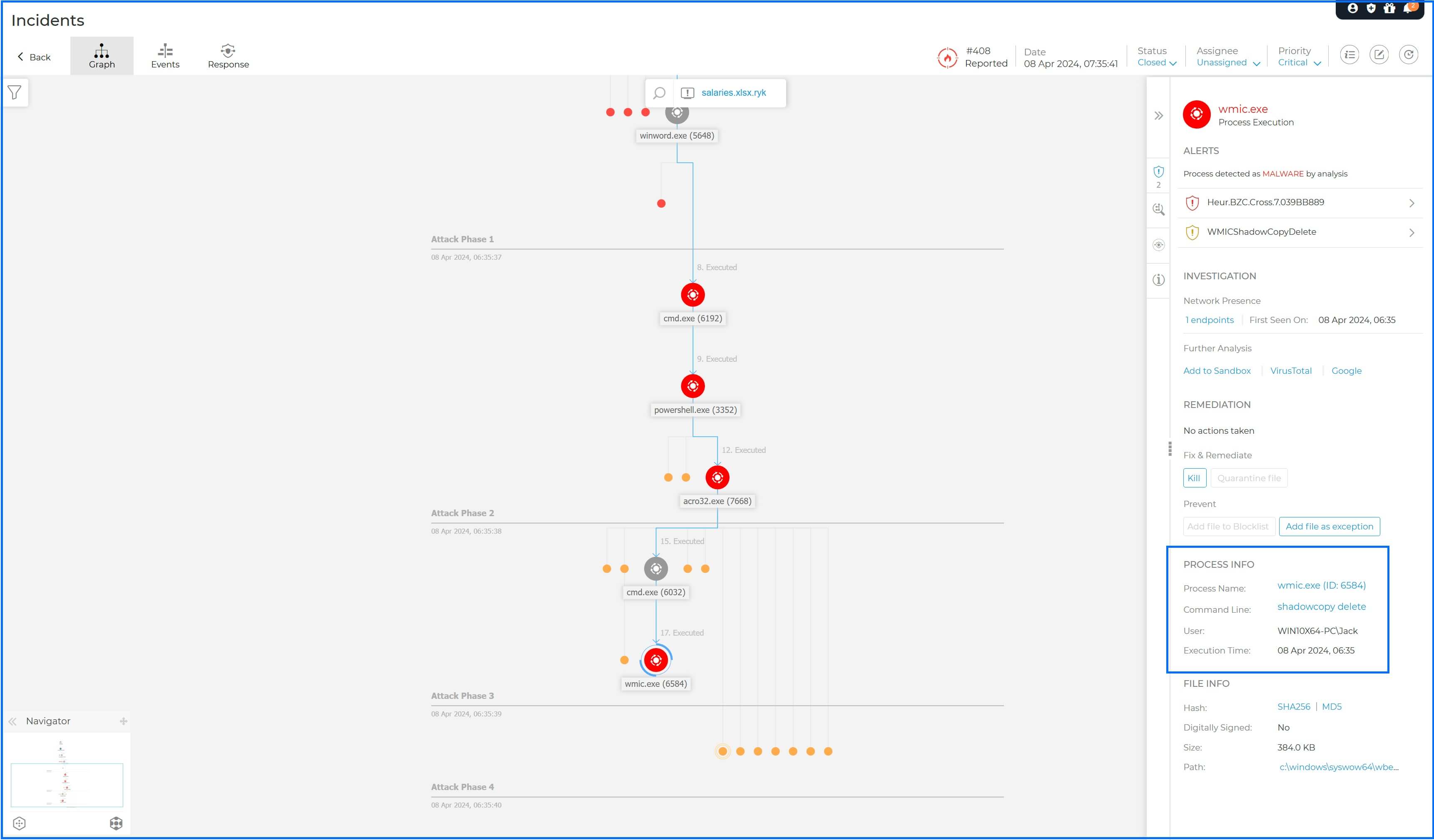
Therefore, Bitdefender employs a real-time backup process triggered only when necessary, independent of the Shadow Copy mechanism. Instead, Bitdefender has developed its own internal mechanisms, using proprietary encryption technology, ensuring resilience and minimal impact on overall system performance. Our primary focus is on making prompt and accurate decisions, swiftly identifying when a process should be considered untrusted and promptly determining whether its actions are legitimate or illegitimate.
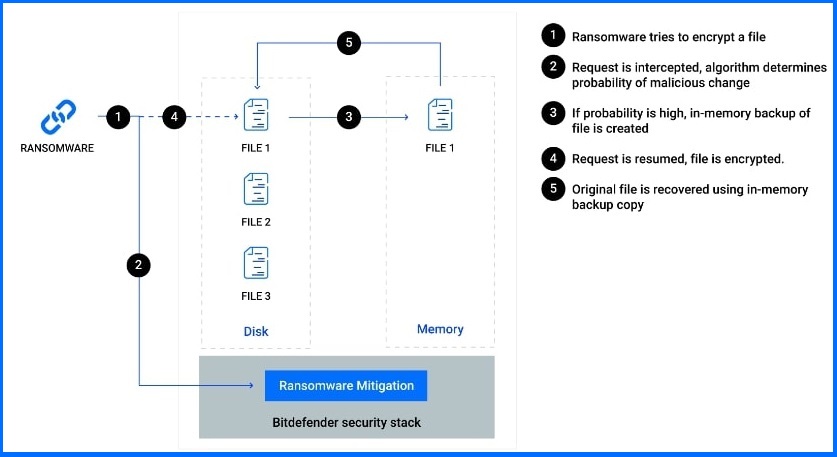
In the event of ransomware detection, Bitdefender GravityZone allows users the option to terminate the malicious process and restore the affected files. The administrator can choose to restore his files either manually, using the console interface, or automatically when the attack is detected and blocked.
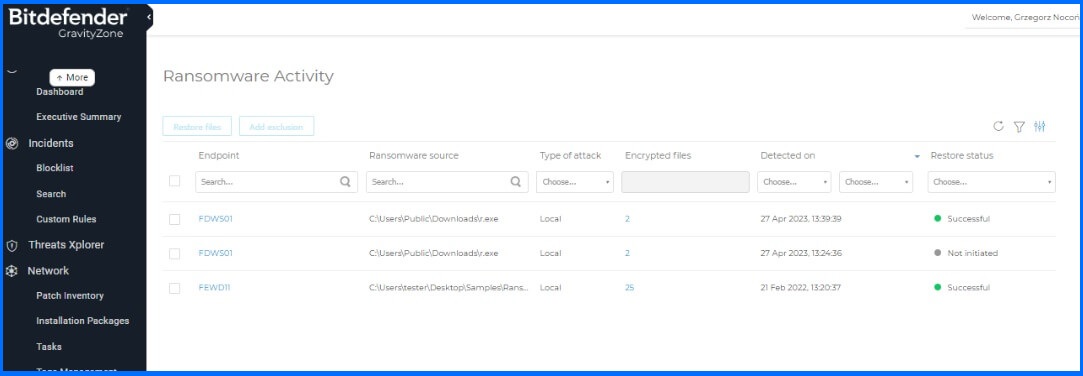
Attacks blocked by the Ransomware Mitigation module are displayed in the GravityZone Cloud console in the Ransomware Activity section. You can view the list of files that were encrypted during the attack, the deadline until the restore task can be initiated, and information about the original path, the path where the file has been restored, and the restore status respectively.
Cloud support Level
Cloud services for Ransomware mitigation have three primary purposes, enhancing our overall ransomware defense capabilities:
Heuristic tuning and new algorithm testing: The cloud services provide a dedicated environment for fine-tuning existing heuristics and testing new ones. By utilizing this platform, we can continually enhance the accuracy and effectiveness of our detection mechanisms, ensuring optimal performance against emerging ransomware threats.
Fast False Positive Mitigation: In cases where local heuristics are uncertain or trigger false positive alerts, cloud services serve as a swift mitigation solution. By leveraging the expertise and analysis capabilities of cloud services, we can rapidly validate the observed behavior and provide a definitive verdict. To learn more about our approach we recommend reading this article: Minimizing False Positive
Fast False Negative Mitigation: Similarly, when local heuristics fail to identify a potential ransomware threat (false negatives), the cloud services act as a rapid response mechanism. By submitting the observed data and actions to the cloud services, we can promptly evaluate the information and deliver an accurate assessment. This agile process mitigates the risk of undetected ransomware incidents and allows for immediate remedial actions.
Recommended Content
To learn more about the technologies included in the protection layer we recommend reading the next article Mobile Security.