Stopping Ransomware: A Technical Deep Dive into Attack Vectors & Mitigation Strategies – Bitdefender TechZone
Stopping Ransomware White Paper: A Technical Deep Dive into Attack Vectors & Mitigation Strategies with Bitdefender
Ransomware's evolution, accelerated by the introduction of Ransomware-as-a-Service (RaaS) model, requires a continuous reevaluation of defense strategies. This whitepaper deconstructs the modern ransomware kill chain, exposing attacker methods at each stage. We'll explore how RaaS has changed attacker behavior and why a multilayered defense-in-depth architecture remains the most effective way to combat ransomware threats.
As ransomware constantly evolves, so does this article. Bookmark this page to stay informed, and for the latest ransomware insights, check out our monthly Bitdefender Threat Debrief report.
Ransomware Ecosystem
Before diving into the technical details, let's understand the financial side of ransomware attacks. We'll also clear up some common misconceptions about the RaaS model.
The cybercrime ecosystem is driven by the same economic forces as regular markets. A new business concept or idea can quickly become the new standard, eventually replacing previous business practices. Ransomware itself has undergone a revolution with the introduction of RaaS.
RaaS is often described as a model that enables less technically skilled individuals to participate in cybercrime. This perceived ease of access to ransom tools might suggest why ransomware attacks seem so common. However, this is a misconception. Ransomware as a Service (RaaS) allows for specialization among attackers, leading to a collaborative model where teams of specialists, rather than individuals, orchestrate attacks. This shift from generalists to specialized teams is the reason behind the increasing sophistication, scalability, and higher ransom demands of attacks.
Often incorrectly described as a franchise model (which was the early RaaS model in 2017), RaaS has transformed. Today, it functions more like a gig economy model. The world's largest taxi company doesn't own any cars. The world's largest accommodation company doesn't own any property. And the largest ransomware groups don’t deploy ransomware.
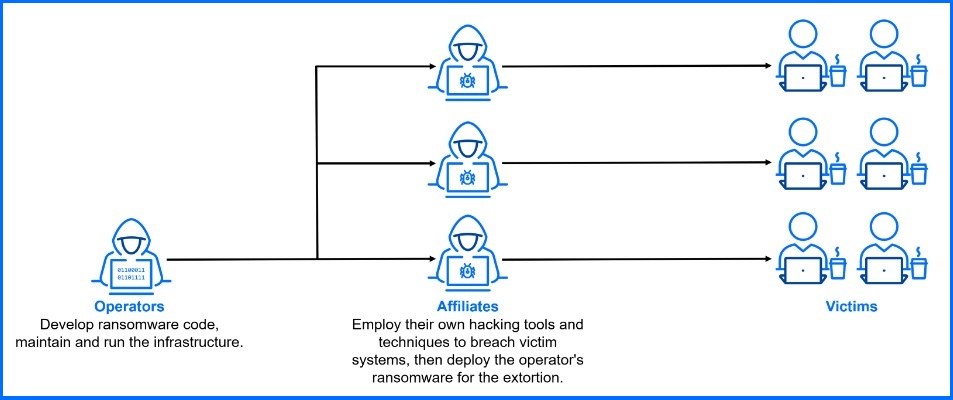
But let's start with the two key players: operators and affiliates.
Operators: Think of them as the "platform providers" in the regular economy. They build the ransomware code, manage the infrastructure, but also handle the money – negotiating and collecting ransoms.
Affiliates: These are the attackers who carry out the actual hacking, everything from initial access to deploying the ransomware.
Continuously, new specialists such as brokers focusing on initial access and negotiators handling ransom payments are joining the ranks. These specialists help RaaS groups make more money. For example, better initial access can lead to more victims, skilled negotiators can increase pressure on targets, and legal experts can help navigate cyber insurance policies and compliance requirements.
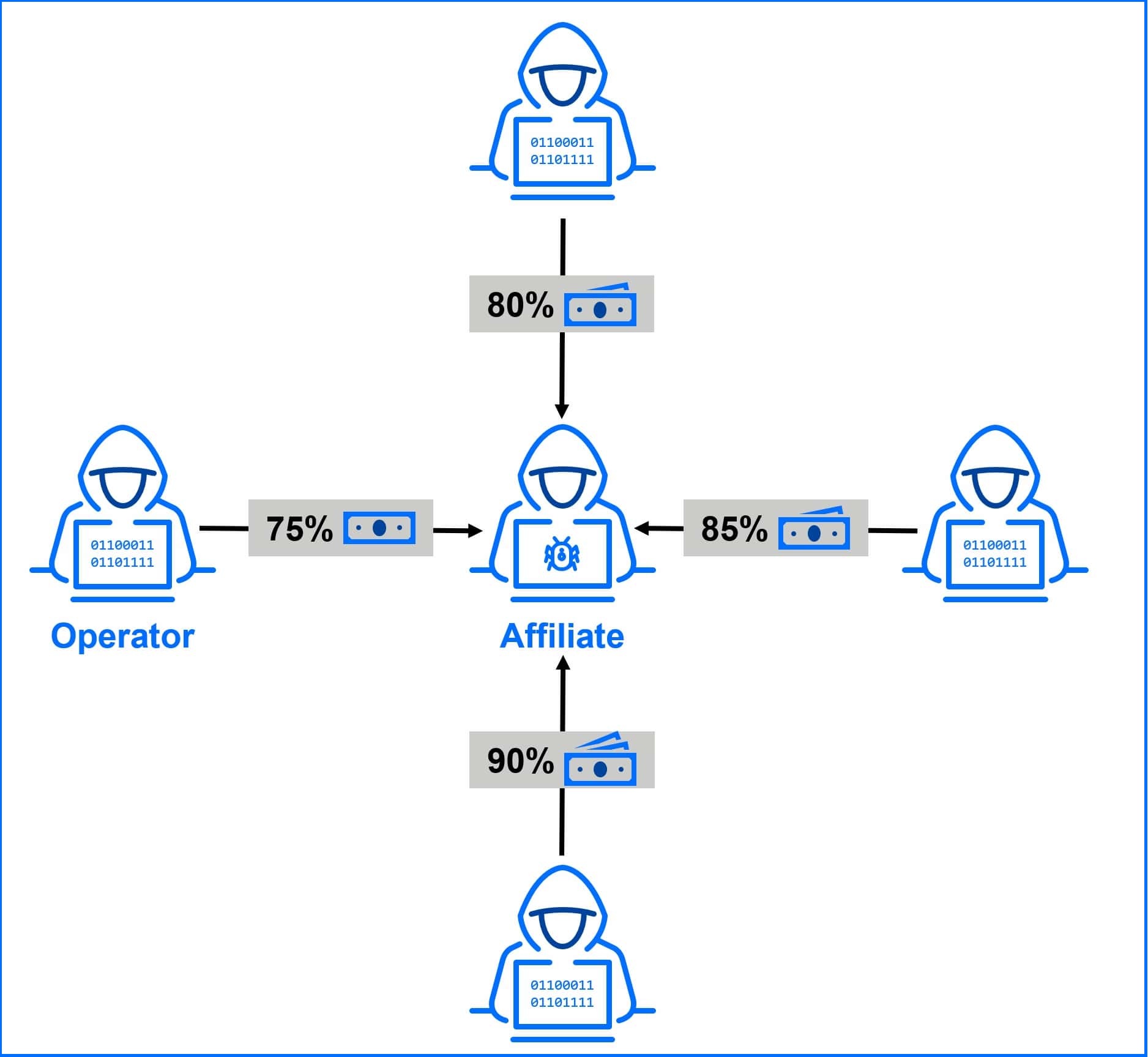
The news might focus on RaaS groups, but in the ransomware world, affiliates are the real muscle behind attacks. These are the hackers who deploy the ransomware and keep the lion's share of the ransom (typically 75-90%), all while staying anonymous. Affiliates aren't locked into one group. They can switch between RaaS groups or even work for multiple groups at once. RaaS groups compete fiercely to attract these skilled affiliates by offering the most attractive deals.
The manual nature of their work makes modern ransomware operations surprisingly like nation-state attacks of the past. This means any organization that could be a target needs robust security that defends against manual hacking techniques.
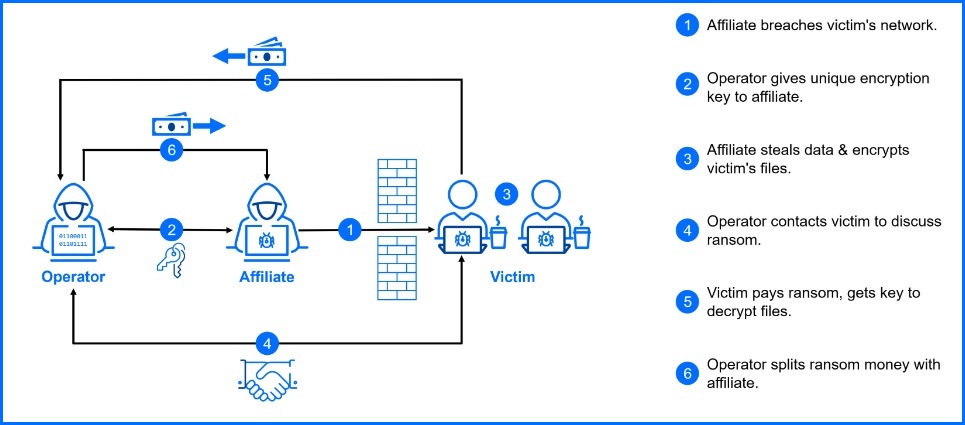
There is another important mechanism from the gig economy model: affiliates don't get paid directly by the victim. The RaaS group, acting as a platform provider, negotiates, collects, and then distributes the ransom. This means affiliates invest significant time and effort upfront (weeks or even months) with no guarantee of a payout. They have to trust the operator to collect the money and then hand over their significant share.
Ransomware-as-a-Service profit-sharing model. Affiliates own access to networks and receive the biggest share of profit.
Even legitimate gig platforms rely on trust between workers, platforms, and clients. However, the trust within the RaaS model is a twisted version, existing between cybercriminals with a shared interest in ill-gotten gains. This very foundation becomes its Achilles' heel when free decryption tools, like those Bitdefender provides to NoMoreRansom.org, and successful law enforcement takedowns come into play.
These disruptions lead to frustration and anger within the RaaS network, with affiliates demanding compensation from operators for wasted time and resources due to faulty malware or issues with operations security.
We have debunked the myth of ransomware as a simple attack. It’s a complex hacking operation fueled by a profit-sharing network of specialists, and ransomware deployment is just the final payload. Next up: How these attacks work, and how to build a defense-in-depth architecture to stop them.
Anatomy of the Ransomware Attack
Ransomware's constant evolution is a major reason it remains a top cybersecurity threat for businesses of all sizes. The problem is twofold: first, unlike the earlier versions that simply locked a single machine, modern ransomware attacks are manual hacking operations targeting whole networks. Manual attacks are harder to anticipate because they're more flexible and rely on exploiting any opportunity they find. This constant change makes it difficult for defenses to stay ahead.
Second, many ransomware groups have shifted their focus from merely encrypting data, which compromises availability, to stealing and threatening to publicly expose it, a breach of confidentiality. This evolution in tactics suggests that even the term 'ransomware' may now be somewhat outdated. Essentially, ransomware has become a much more sophisticated threat, with the focus on maximizing damage and pressure, not on the speed of attack. Attackers can spend weeks or months preparing for the execution of an attack.
Weeks of groundwork often go into a ransomware attack. Hackers don't just launch in – they spend weeks infiltrating your network and setting the stage.
Many ransomware attacks now originate in the extended supply chain, not just through compromised software updates (traditional software supply chain attacks). Attackers target any weak link – a compromised supplier, customer, vendor, or contractor – to gain access to other connected businesses. This allows them to potentially launch larger-scale attacks, and we've even seen cases where attacks on multiple victims are coordinated. Even if the specific scenarios described here don't directly apply to your company's setup, a compromise within your extended supply chain can lead to your security breach.
The best defense against a constantly changing attacker is a flexible defense strategy. Here's the key idea:
Reduce Your Attack Surface: Identify and minimize the weaknesses attackers could exploit (your network's "exposed areas"). This includes hardening systems, using strong passwords, and educating employees about phishing scams (prevention).
Layered Security: Build a multi-layered shield by implementing tools like firewalls and anti-malware software (protection).
Be Ready to Respond: Have a plan to identify and address any signs of a cyberattack ("indicators of compromise") (detection and response).
Unlike simpler attacks, modern ransomware involves active hacking throughout the process. The good news? This active phase often generates a lot of "noise" on your network. This means with the right tools and strong security practices you can detect these attacks before they become major breaches.
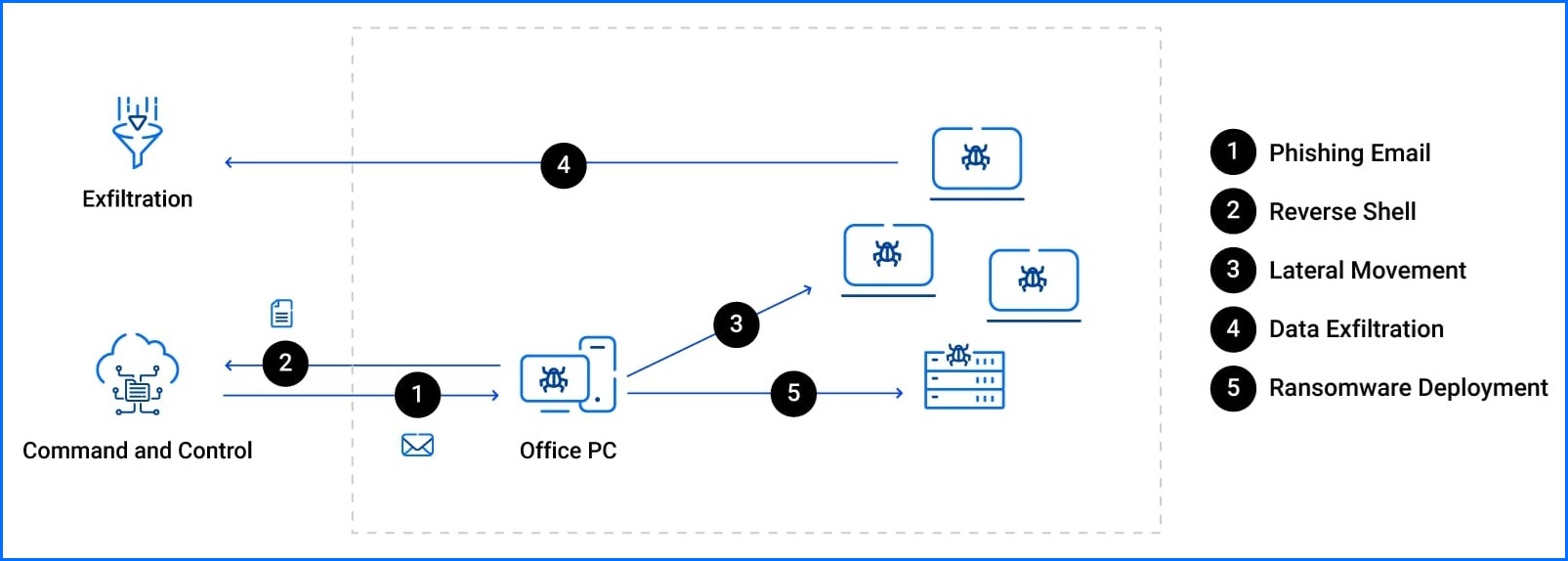
By understanding the different stages of a ransomware attack, you can identify opportunities to block the attack entirely or detect and respond to it while it's happening.
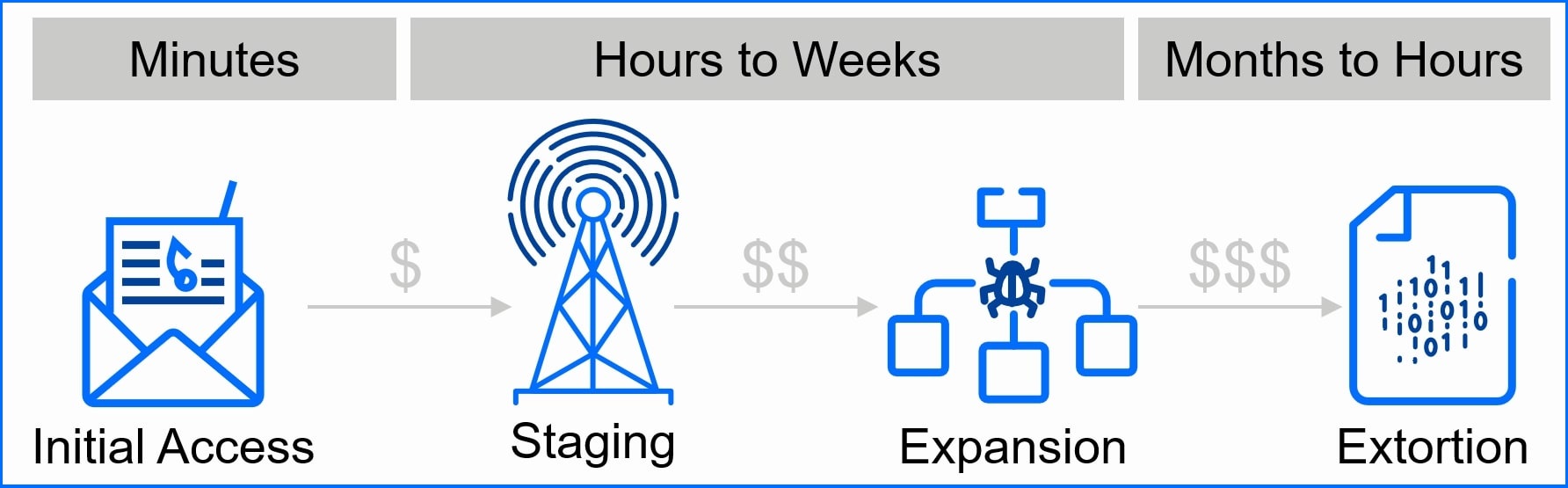
The following sections dive deep into the four stages of a typical ransomware attack: Initial Access, Staging, Expansion, and Extortion. We'll explore what attackers do at each stage, and more importantly, how you can fight back with effective security controls and best practices.
Initial Access

This chapter dives deep into the various methods attackers use to achieve initial access. We'll explore common attack vectors like phishing emails, exploited vulnerabilities, and compromised credentials. By understanding these techniques, you can take proactive steps to harden your defenses and significantly reduce the risk of a ransomware attack succeeding.
The distinction between targeted and opportunistic attacks used to be a key factor in initial access. However, with the rise of automated vulnerability scanning and exploitation tools, this line has become increasingly blurred. Ransomware groups can now compromise a vast number of victims in a short period, but it can take them months to sort through them. For this reason, the direct vs. delayed attack distinction offers a more practical framework for defense.
Direct Attacks
With direct attacks, attackers move swiftly, launching subsequent stages of the attack shortly after compromising the victim.
The most common example of this method is targeted social engineering, typically spearphishing emails. Deceptive emails designed to trick recipients into clicking malicious links or opening infected attachments remain a simple, but effective tactic. Traditionally, user awareness training has been a defense against spearphishing emails. But LLMs have empowered attackers to craft highly believable spearphishing emails, rendering user awareness training even more insufficient than it already was. LLMs can personalize these emails with relevant details and even mimic writing styles, making them difficult to distinguish from legitimate messages.
We've mentioned multi-layered security a few times already. Now, let's dive into a real-world example: a phishing email, and see how layers of defense can stop it.
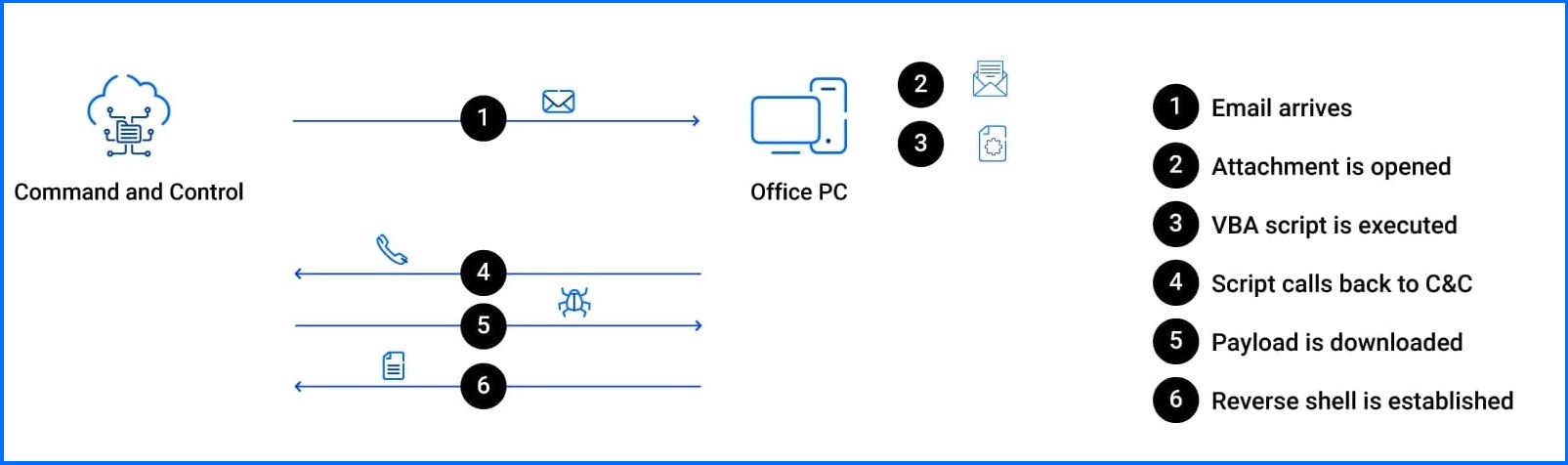
A phishing email with a malicious document containing VBA code is the first stage of an attack. This code connects to a command and control (C2) server to download the actual payload. Once executed, the payload establishes a reverse shell, allowing the attacker to connect to the system remotely.
Even a seemingly simple attack like this can trigger multiple detections across a multi-layered security platform, highlighting the importance of comprehensive defenses. Bitdefender GravityZone, for example, demonstrates this by activating various detection mechanisms in response to such threats.
Email Protection: Before a suspicious email even reaches your inbox, GravityZone scans it with multiple engines and threat intelligence to identify potential dangers.
Malware Protection: If you open an attachment, it undergoes further scrutiny. A static engine checks if it's a known threat, while machine learning helps detect even cleverly disguised malware.
Sandbox Analysis: If the attachment seems suspicious, it's uploaded to a secure "sandbox" environment where it can be detonated safely. This allows GravityZone to analyze its behavior in detail and understand what the embedded VBA code might do.
Multi-Layered Protection During Execution: If the VBA code starts running, various security modules kick in:
Fileless Protection: Analyzes the code itself, monitors its activity using AMSI and our proprietary command-line scanner.
Software Exploit Protection: Focuses on vulnerabilities in popular software like Microsoft Outlook, including special heuristics for VBA and shellcode detections.
Process Protection: Monitors processes (even the ones we trust) in real-time, looking for suspicious behavior, such as a Microsoft Office program trying to launch a command prompt.
Network Protection: Even if the code attempts to download additional malware from a remote server (C2 server), GravityZone uses threat intelligence to check the server's reputation. If it's known to be malicious, the download is blocked.
Network Attack Defense: In the worst-case scenario, if the attacker manages to execute malicious code and establish a reverse shell connection, our deep packet inspection solution Network Attack Defense can still intervene. It can recognize suspicious traffic patterns and block the connection; it can even identify custom-built network protocols used for malicious purposes. Even if it's allowed, content scanner can recognize and identify executable code fragments within the network packets.
Any downloaded code from C2 would still face multiple layers of security measures designed to identify and stop potential threats.
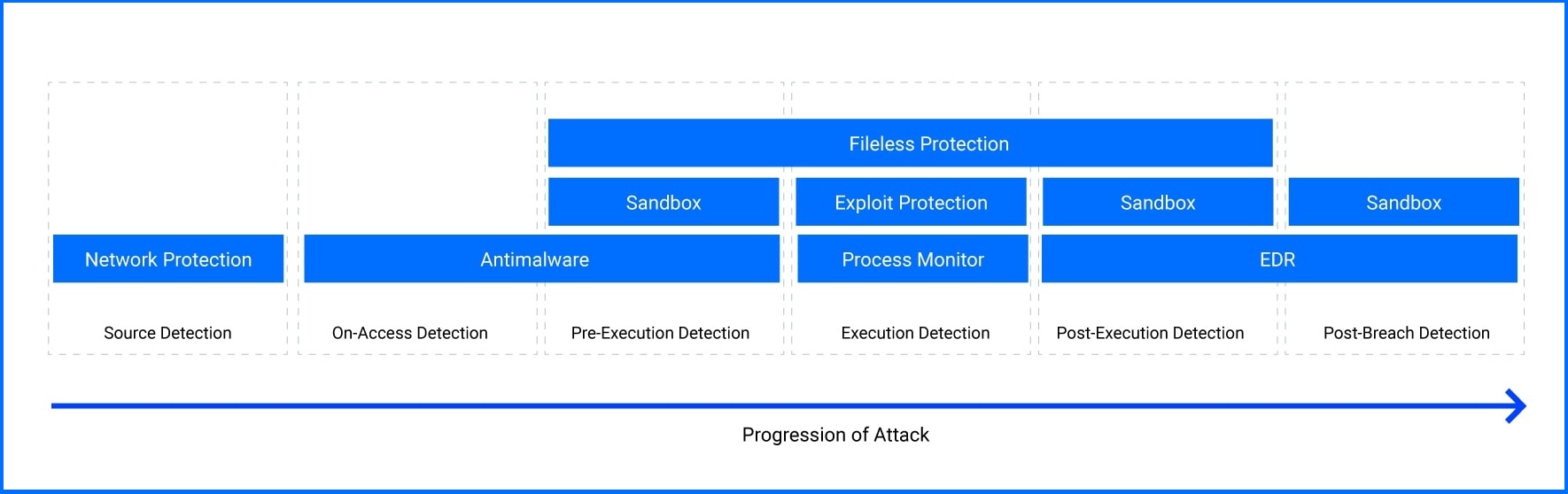
Overlapping security modules, mapped to various malware execution stages, detect and stop threats throughout the entire attack lifecycle.
This is just a glimpse of the security layers working together. GravityZone platform isn't static. Over the years, we’ve constantly improved our defenses by adding more layers while keeping false positives to a minimum.
Delayed Attacks
Delayed attacks involve a significant time gap (days or weeks) between initial access and the next stage. Often, these attacks involve initial access brokers (IABs). IABs specialize in gaining initial access to networks and then selling that access to other cybercriminals, including ransomware groups. In these scenarios, the attackers who gain initial access may have no connection to the eventual ransomware deployment. Beyond social engineering, credential leaks and brute-force attacks on edge devices are additional avenues IABs exploit.
Leaked credentials, often circulating on the dark web, can grant attackers easy access to your systems. Bitdefender MDR team actively monitors for such leaks, alerting you when compromised credentials are found and helping you take immediate action to revoke them. Brute-force attacks often target edge devices and internet-facing assets. Focus on securing RDP, VPN, and SSH access points on these devices, especially for smaller companies that might have limited IT resources and experience. However, the best defense is a strong offense – while password less authentication (like FIDO2) offers the ultimate defense against stolen credentials, multi-factor authentication (MFA) remains a more realistic first step. MFA adds a crucial extra layer of security beyond passwords, significantly reducing the risk of unauthorized access.
In addition to strong authentication measures, GravityZone Risk Management can significantly reduce your vulnerability to these threats. Risk management is part of the prevention layer, identifying weaknesses on your devices and within your user base. They can pinpoint misconfigured settings on endpoints, outdated software vulnerabilities, and even risky user behavior patterns. This valuable information empowers you to take targeted actions, such as patching vulnerabilities, strengthening endpoint security settings, and providing security awareness training to users most susceptible to phishing scams. Extending your risk management strategy to the cloud with a Cloud Security Posture Management+ (CSPM+) solution adds another layer of protection. CSPM offers continuous monitoring of your cloud environment, identifying misconfigurations that attackers could exploit.
We've saved the most critical attack method for last: exploiting software vulnerabilities in edge devices. While patching has always been the solution, this tactic has become a much bigger threat in recent years (starting in 2021 with Log4Shell). The big shift is the speed at which new vulnerabilities are weaponized.
Malicious actors, including both financially motivated cybercriminals and nation-state actors, prioritize finding vulnerabilities with a high CVSS score, particularly those that enable remote code execution (RCE) and affect publicly accessible systems. Once a high-risk vulnerability is discovered, attackers build automated scanners that exploit the weakness. These scanners can compromise vulnerable systems and establish a backdoor (like a web shell) for later access, often within 24 hours of the vulnerability details being released.
To stay ahead of attackers, you need to see your organization through their eyes. Use automated solutions like GravityZone External Attack Surface Management (EASM) to help you understand your internet-facing assets (websites, cloud applications), and their associated vulnerabilities. Together with Patch Management, you can keep operating systems and software applications up to date.
Both patch management and risk management are mostly effective when implemented as continuous processes. Choosing a well-integrated, easy-to-use solution helps establish good cyber hygiene routines across your organization.
After the initial compromise, there is the second stage of the attack:
Stage 1: The Initial Blitz (Hours or Days) Attackers exploit the vulnerability with automated tools, potentially compromising hundreds or even thousands of networks in a very short time frame.
Stage 2: The Long Game (Weeks or Months) After the initial breach, attackers need to sift through the compromised systems, prioritizing high-value targets. They proceed with manual hacking phase.
The transition from the initial breach (Stage 1) to the deployment of ransomware or data theft (Stage 2) can take weeks or even months. This delay happens because attackers need to sift through the many compromised systems they've gained access to, prioritizing the most valuable targets. Stage 2 also involves manual hacking work, which takes even longer.
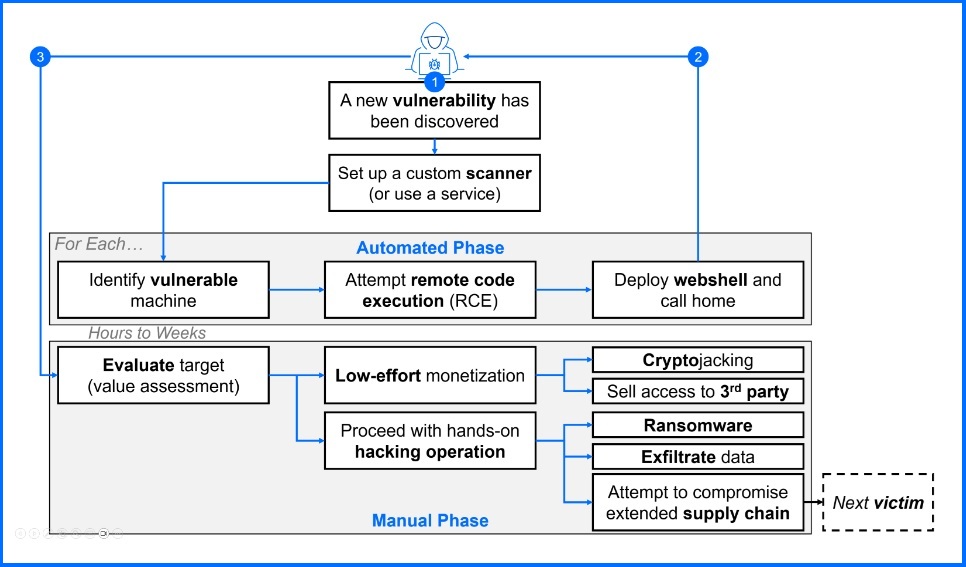
Major ransomware groups are increasingly using opportunistic initial access methods to launch their manual hacking operations
Here's why detection and response (EDR, XDR, or MDR) solutions are becoming so popular: they minimize the time attackers spend undetected within your systems (often called "dwell time"). These tools were originally developed to combat sophisticated attacks from nation-state actors, but today, they're just as important to combat RaaS affiliates employing similar tactics. By identifying and stopping attackers before they can launch their final attack, these solutions can significantly reduce the risk of a security breach.
Staging

After attackers gain initial access to your network, they might find themselves in a few different locations. These can be areas like the DMZ, a buffer zone between your internal network and the internet, isolated cloud environments, or even development and testing environments that are only temporary. Regardless of the initial entry point, the attackers' primary focus during the staging phase becomes establishing a more persistent presence within your network.
Imagine a thief breaking into your house. They wouldn't just grab the first thing they see and disappear. Instead, they might be more interested in setting up a way to come back later with the right tools for a bigger heist. For some threat actors, establishing persistent access is the final goal. Access brokers can sell this access on dark web marketplaces to other threat actors, such as affiliates associated with one of the ransomware groups.
Here's what attackers will try to do next:
Try to Access More Systems: Attackers actively try to access additional systems within your network beyond their initial entry point.
Look out for: Unauthorized access attempts. An unusual network activity suggesting someone is mapping your network layout.
What to do: Divide your network into smaller segments. This limits the areas attackers can access if they gain entry, making it harder for them to move laterally and find valuable assets.
Install Persistence Mechanisms: Attackers establish persistence mechanisms to maintain persistent access to your network for future attacks.
Look out for: Signs of suspicious software installations or attempts to modify system configurations.
What to do: Operationalize detection of persistence mechanisms, leverage EDR/XDR for suspicious event review, and conduct regular threat hunts for hidden attackers.
Test Ways to Gain More Control: They experiment with different methods (exploits) to gain higher user privileges (escalate their access).
Look out for: Indications of exploit testing on your systems.
What to do: Restrict access to critical systems and data to only authorized users with the minimum privileges they need to do their jobs. In addition to access control, implement continuous monitoring of user activity to detect any suspicious behavior.
Cover Their Tracks: Just like a sneaky thief might erase fingerprints, attackers often try to erase their activity logs to make it harder for you to detect them.
Look out for: Attempts to delete activity logs, which could be a sign someone is trying to hide their tracks.
What to do: Ensure logging is enabled, functional, and provides sufficient information and historical data for effective support when needed. Regularly review and update logging configurations to capture relevant security events and maintain visibility across the environment.
The staging phase is critical because it's the calm before the storm. While no data is necessarily stolen or encrypted yet, attackers are setting the stage for a more significant attack. The good news? This period also provides a window of opportunity. The key to stopping attackers during staging is to be on the lookout for suspicious activity. While they're trying to stay hidden, their actions will generate some "noise" that you can detect if you're looking for it.
Any of the multiple overlapping GravityZone modules can be triggered during this stage – from privilege escalation to lateral movement across the network. Each of these detections can trigger an incident response, preventing a ransomware attack from fully expanding. Bitdefender security stack provides protection before, during, and after a suspicious event.
While having strong protection is important during the staging phase of an attack to generate alerts, a mature approach to security operations is even more critical. Attackers are persistent – if they have a foothold and you give them enough uninterrupted time, they'll find a way in. The key is to set up your environment to reduce background "noise" from normal operations. This allows you to clearly identify any suspicious activity that might indicate an attacker. Be prepared to respond quickly once you spot something amiss.
XDR with anomaly detection shines in these scenarios. It can identify unusual behavior, even by privileged accounts, that might otherwise go unnoticed. Imagine a user attempting to cover their tracks by disabling monitoring services. GravityZone XDR's sensor can detect this, for example, by identifying when a user stops Amazon's logging service on AWS. Similarly, the Azure AD sensor can flag situations where an application is granted global administrative rights, a potential red flag.
The secret sauce behind this powerful detection lies in our custom machine learning models. Unlike generic models, these are trained specifically on each customer's system. In other words, each system within your environment has its own unique machine learning model, customized to recognize the normal activity patterns specific to your organization. This tailored approach allows XDR to identify even subtle deviations from the norm, potentially indicating an attacker's presence.
Even better, don't wait for a real attack to test your defenses. Consider using "ethical hacking" services. These simulate real-world attacks, helping you identify weaknesses and ensure your security tools are properly configured.
Expansion

After gaining initial access to your network, attackers typically enter an "expansion phase." Their primary goal here is to amplify the impact of their eventual ransomware attack.
Taking Control: Attackers will target systems that grant them broader control over your network. This often includes compromising domain controllers, which manage user accounts and access permissions, and hypervisors, which control virtual machines. By compromising these systems, attackers can potentially lock you out of critical resources or deploy ransomware across multiple machines simultaneously.
Finding Your Valuables: Imagine a thief searching for valuables in your house. Attackers will actively search for sensitive data they can steal, such as financial records, customer information, or intellectual property. This data can be used for various purposes, including selling it on the dark web or using it to pressure you into paying a ransom. To calculate an appropriate ransom amount, attackers might try to gather information about your cyber insurance coverage.
Assessing Your Defenses: Attackers will try to gather information about your cybersecurity preparedness. This includes your incident response plan, which outlines how your organization would handle a security breach, or your backup strategy, tools, and procedures.
Attackers understand the value of "Living off the Land" (LOLbins) – utilizing legitimate administrative tools already available on your systems. These tools, like PowerShell, WMI/WMIC, and PsExec, are familiar to IT professionals and blend seamlessly into network traffic. This makes them significantly harder to detect compared to easily identifiable malware or known hacking tools.
Attackers can take LOLbins a step further by exploiting your existing software portfolio. Imagine them reading your remote access documentation and obtaining a legitimate VPN certificate or leveraging pre-deployed remote control software like TeamViewer or AnyDesk. By exploiting your own tools and procedures, they can establish a facade of legitimacy, making their activity appear innocuous and delaying detection.
Attackers don't settle for a single point of entry. They diversify their backdoors by deploying them in various locations across your network and use a variety of tools and techniques for creation. This redundancy offers attackers multiple points of entry if their initial foothold is discovered. The sheer number and variety of backdoors can make them incredibly challenging for defenders to identify and eliminate. This complexity is a calculated move by attackers to extend their persistence within your network.
However, this strategy also carries a risk for attackers. The more backdoors they deploy, the greater the chance that one of them might be uncovered during a routine threat hunt. If a single backdoor is detected, it could lead to the exposure of their entire operation.
As attackers near the ransomware deployment stage, their pre-attack testing phase offers one of the last opportunities for security teams to identify an ongoing threat. Watch for signs of tampering with your endpoint security software, unusual activity involving Group Policy Objects (GPOs) or other mechanisms that can distribute malware across your entire network. If you detect small-scale data encryptions, this could indicate attackers testing their encryption tool before launching a full-blown attack.
The expansion phase presents a unique challenge for security teams because attackers often rely on legitimate tools. Unlike earlier stages where malware detection might be straightforward, identifying malicious intent here hinges on spotting unusual activity. This is where solutions like Bitdefender XDR or Bitdefender MDR come into play, focusing on identifying suspicious behaviors that might indicate an attack in progress, even if it's not a perfect match to a known threat. Events are collected by XDR sensors, then analyzed for suspicious behavior and assigned a risk score. If the probability of malicious intent is high enough – a security incident is reported. In addition to analyzing individual incidents, security analytics also analyze relationships between individual alerts and incidents. With cross-organization correlation, a security incident can be detected faster, and we can interrupt the kill chain before it fully develops.
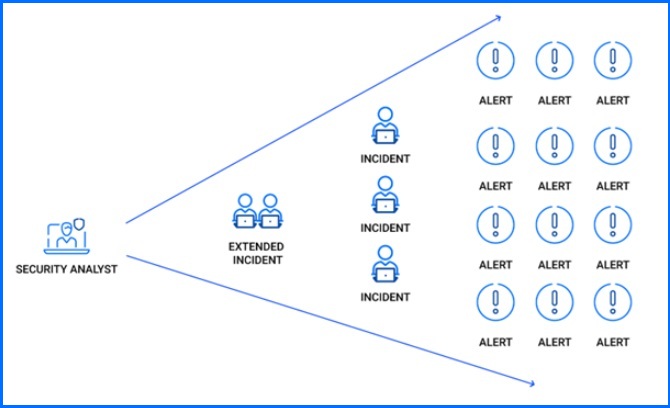
Bitdefender XDR connects events to alerts, then to incidents, providing a single-page view of suspicious activity for faster investigation.
An XDR solution doesn’t see all alerts as equal – it assigns them different weights and treats them differently. For example, automated blocking of malware in an email attachment is an isolated incident that doesn’t require human intervention. On the other hand, detecting a ZeroLogon attack against one of the domain controllers from inside the network should trigger an immediate response. Central correlation engine can use this incident to map the whole kill chain, even triggering detections that would otherwise go unnoticed – for example, a seemingly harmless PowerShell script is blocked if it is linked to previous actions of threat actors (see demo of GravityZone XDR).
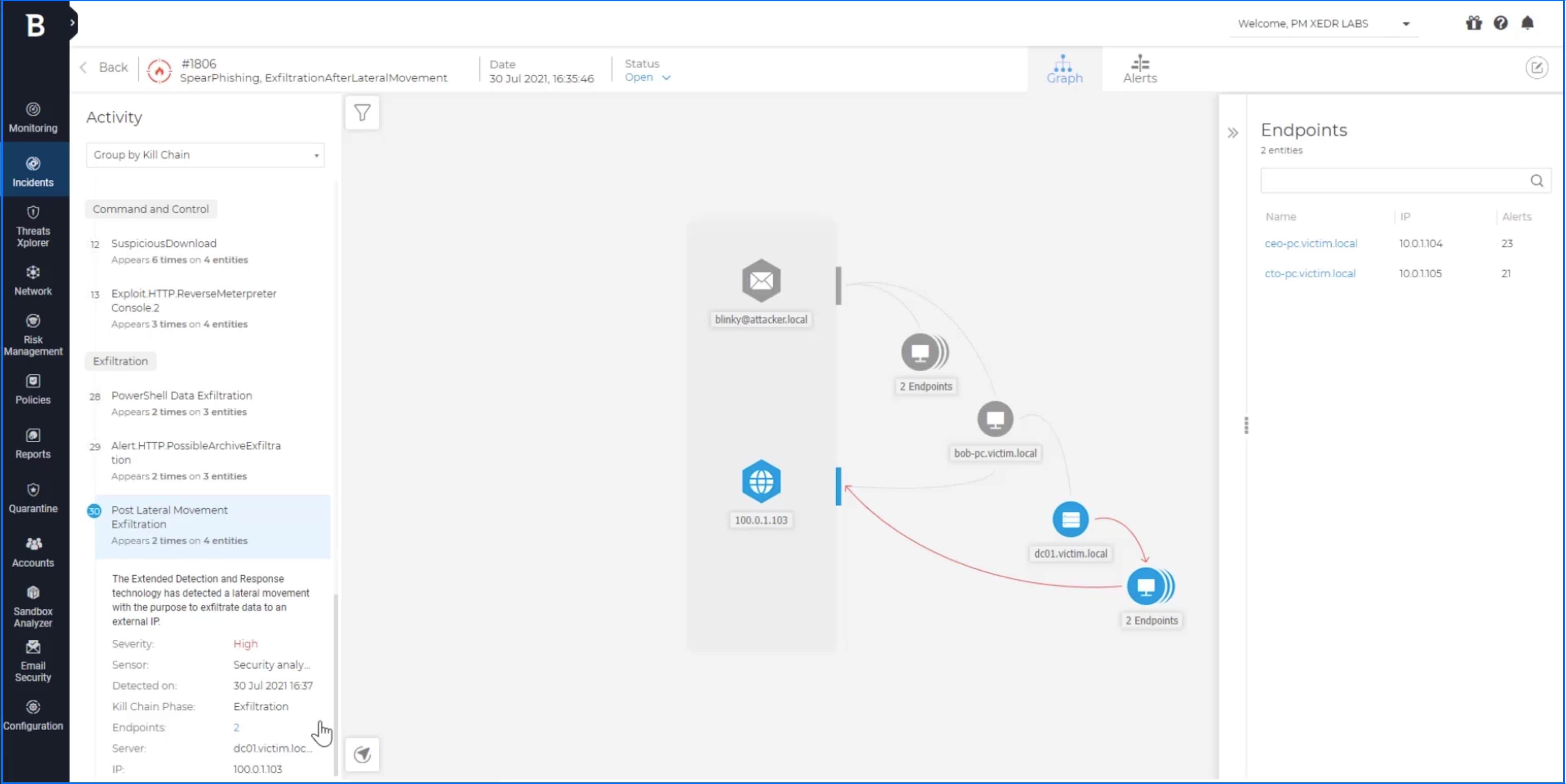
Example of extended incident visualization. PowerShell data exfiltration after the lateral movement was automatically detected.
Extortion

While encryption remains a popular tactic, many ransomware groups are increasingly prioritizing data exfiltration. This means they steal your sensitive information – financial records, customer data, intellectual property – before or even without encrypting your systems. This stolen data becomes the primary tool for extortion. The threat of releasing this confidential information to the public or selling it on the dark web creates immense pressure on organizations to pay the ransom, rendering traditional backup strategies less effective. Even the term "ransomware" itself starts to feel misleading, as data theft takes center stage. Unfortunately, many companies learn this harsh lesson the hard way, only to discover that backups can't recover the stolen data and their only hope rests on paying the ransom or mitigating the fallout of a data breach.
Attackers leverage various tools and techniques to steal your sensitive information, but in most cases, they favor simplicity and effectiveness overelaborate methods. This could involve using standard FTP protocol or public cloud storage to transfer stolen data to their own locations. Some RaaS platforms offer affiliates more advanced options like custom exfiltration tools and even dark web storage. Using more exotic methods like steganography or DNS data exfiltration is not common or even necessary. To further minimize detection, attackers typically exfiltrate data in smaller batches over a longer period, rather than attempting a single, large transfer. Data exfiltration often reaches its peak during the expansion phase.
Once your data leaves your network, especially through anonymized channels, retrieving it becomes an uphill battle. The sooner you identify and contain the threat, the less data attackers can steal. While some data exfiltration may still occur during the extortion phase, it's often a continuation of the process that began earlier.
While stolen data gives them leverage through the threat of exposure, encryption throws another wrench into the recovery process and increases pressure on a victim. Attackers often favor familiar tools readily available on your network to deploy the ransomware. These tools might include PsExec/WMI, commonly used for remote administration, or even legitimate management tools like Group Policy or Microsoft Intune.
Bitdefender’s Ransomware Mitigation is a feature designed to mitigate the impact of an active ransomware attack. When a file is encrypted the randomness (or entropy) of the file goes up significantly. Ransomware Mitigation monitors for this increase in entropy of files on the disk, and during write attempts. When a request is made to encrypt a file (an increase of randomness over a certain limit), a temporary backup is created in memory and the original file is restored after the file changes are done. Importantly this method does not rely on the Volume Shadow Copy service or other static backup solutions, as this backup data is almost always deleted by threat actors. Requests to delete shadow copies are one of the triggers for an EDR incident. Using this approach, we provide ransomware mitigation even against previously unseen ransomware variants.
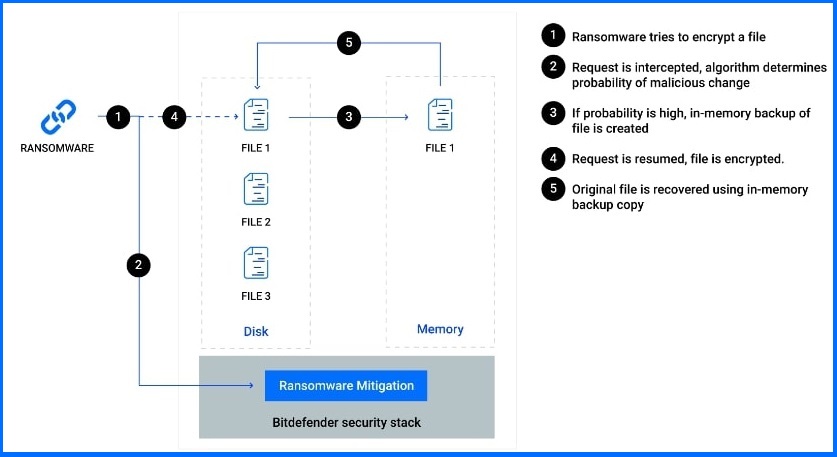
Ransomware Mitigation recovers the content of encrypted files using an in-memory backup
Ransomware Mitigation is supported for both local and remote scenarios. For Local Ransomware Mitigation, administrators can configure Bitdefender’s security policy to monitor endpoint processes and recover the encrypted files as soon as the adaptive technology detects and blocks the attack. Even if ransomware manages to encrypt the local files, mitigation technology immediately jumps in to recover those files, either automatically or on-demand where the admin controls the timing of the recovery of the encrypted files.
For Remote Ransomware Mitigation, the security administrator can enable the technology to monitor network share paths that can be accessed remotely and prevent the files from being encrypted. On the remote endpoint, the user agent confirms that Ransomware Mitigation intercepted the remote malicious process behavior and protected the files. Bitdefender administrators can quickly run audit reports and find out more information about the IP address from where the remote ransomware attack was launched and the security module which protected the endpoint, and they can also receive an email notification when an attack is blocked containing information about the attacker’s IP address.
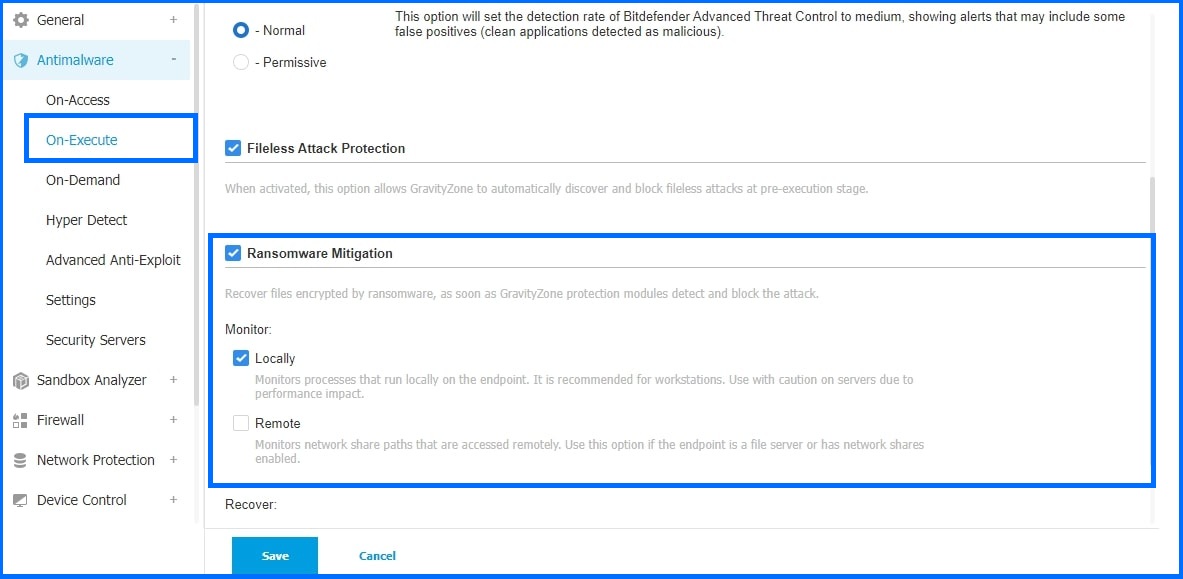
Ransomware Mitigation can mitigate attacks against local and remote files
GravityZone platform also offers ransomware activity reporting for a quick overview of infected machines and their restore status. After an active attack is detected, you can quickly understand how it impacted your endpoints and the steps that are needed to recover your business.
In some cases, attackers might target hypervisors, which manage virtual machines within your data center. While ransomware on individual desktops might restrict access to your data, encrypting hypervisors renders all virtual machines, essentially bricking the machines.
Conclusion
Ransomware is constantly evolving, but there's a proven way to stay ahead: a defense-in-depth, multi-layered security architecture. This time-tested approach strengthens your defenses throughout the entire attack lifecycle – from prevention to detection and response.
Prevention: Implement risk management and patch management to proactively address vulnerabilities before attackers can exploit them.
Protection: Equip your endpoints with robust security solutions to identify and stop threats at the point of entry.
Detection and Response: Utilize an EDR/XDR solution or a Managed Detection and Response (MDR) service to gain continuous visibility into your environment. This allows for rapid detection of suspicious activity and a swift response to contain threats before they escalate.
Remember, the best security is the one that's actively used and provides clear visibility. If it takes weeks to review alerts, you're leaving your organization vulnerable. By adopting a multi-layered approach and prioritizing real-time threat detection, you can significantly strengthen your defenses and stay ahead of the ever-evolving ransomware threat.