Network Protection – Bitdefender TechZone
Enhance network protection with Network Attack Defense (NAD) a comprehensive solution. Prevent security breaches, detect threats, and gain valuable insights.
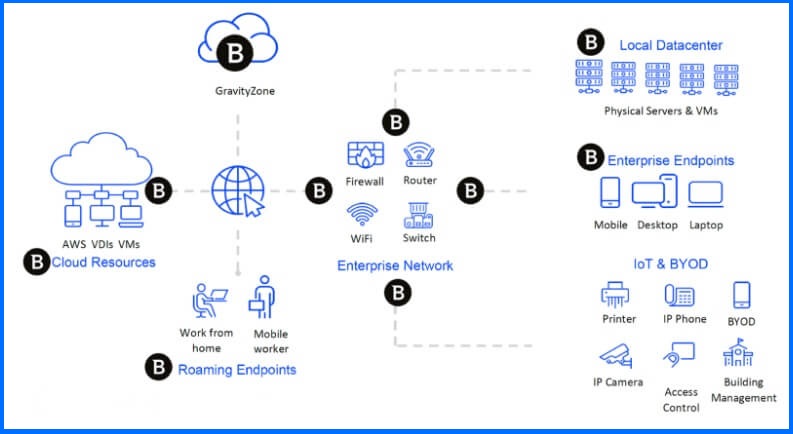
The rise of remote, work-from-home, and on-the-road work has become the new standard, with end users accessing company resources from diverse devices and networks. While the evolving work landscape has made relying solely on perimeter-based security inadequate, this has led to a tendency for many to shy away from network-based security in favor of alternative approaches.
But network-based security remains an essential component of a comprehensive defense-in-depth security strategy. Rather than viewing the security perimeter as obsolete, the focus should be on fortifying it around every device, irrespective of the connection point. No matter how stealthy or advanced the malware may be, its effectiveness can be nullified by blocking its download when it originates from a known malicious location.
In this technical brief, we will outline our approach to network protection and describe how we establish a robust protective perimeter around diverse endpoints, regardless of their physical location.
Network Attack Defense
Network Attack Defense (NAD) is the core of our network protection capabilities. NAD is a deep packet inspection solution that was designed to be OS-independent, allowing us to protect various workloads, from traditional endpoints (Windows, macOS, or Linux), through cloud workloads (including containers), to various IoT and networking appliances.
NAD uses streamed mode processing, analyzing, and processing network traffic in real-time. Depending on the type of deployment, it can work in several different ways, such as inline (when deployed as part of the Bitdefender endpoint security), tap-mode (network sensor for Bitdefender XDR), or PCAP packet capture (for later analysis).
Protocol Support and Features Extraction
NAD provides protection against network-based threats on the Internet (IPv4/IPv6), Transport (TCP/UDP), and Application levels (various protocols). Various application protocols are supported, including HTTP(S), SSL, SCP/SSH, (S)FTP, RDP, DNS, Telnet, SMB (including Samba-based subprotocols such as RPC), and many others. Specifically for incoming server traffic, Network Protection extends its scanning capabilities to protocols such as SMB, RPC, Kerberos, LDAP, and WinRM. Additionally, for enhanced security on Domain Controllers, enabling the 'Inspect encrypted domain controller traffic' option activates decryption for SMB, RPC, and Kerberos protocols on those specific servers. Email protocols such as POP3, SMTP, IMAP, and MAPI are also supported. For POP3, SMTP, and IMAP, infected emails are replaced by notifications to the recipients, while MAPI traffic is only monitored and reported.
For all supported protocols, NAD deconstructs the packets and extracts relevant attributes (a process known as feature extraction). NAD examines the content and structure of packets at a deep level, beyond just the basic header information, in order to understand the nature of the traffic and identify specific patterns or behaviors.
If a protocol is not recognized, NAD includes algorithms for generic content identification. This allows it to recognize objects such as executables or URL addresses even for previously unknown or custom-built protocols.
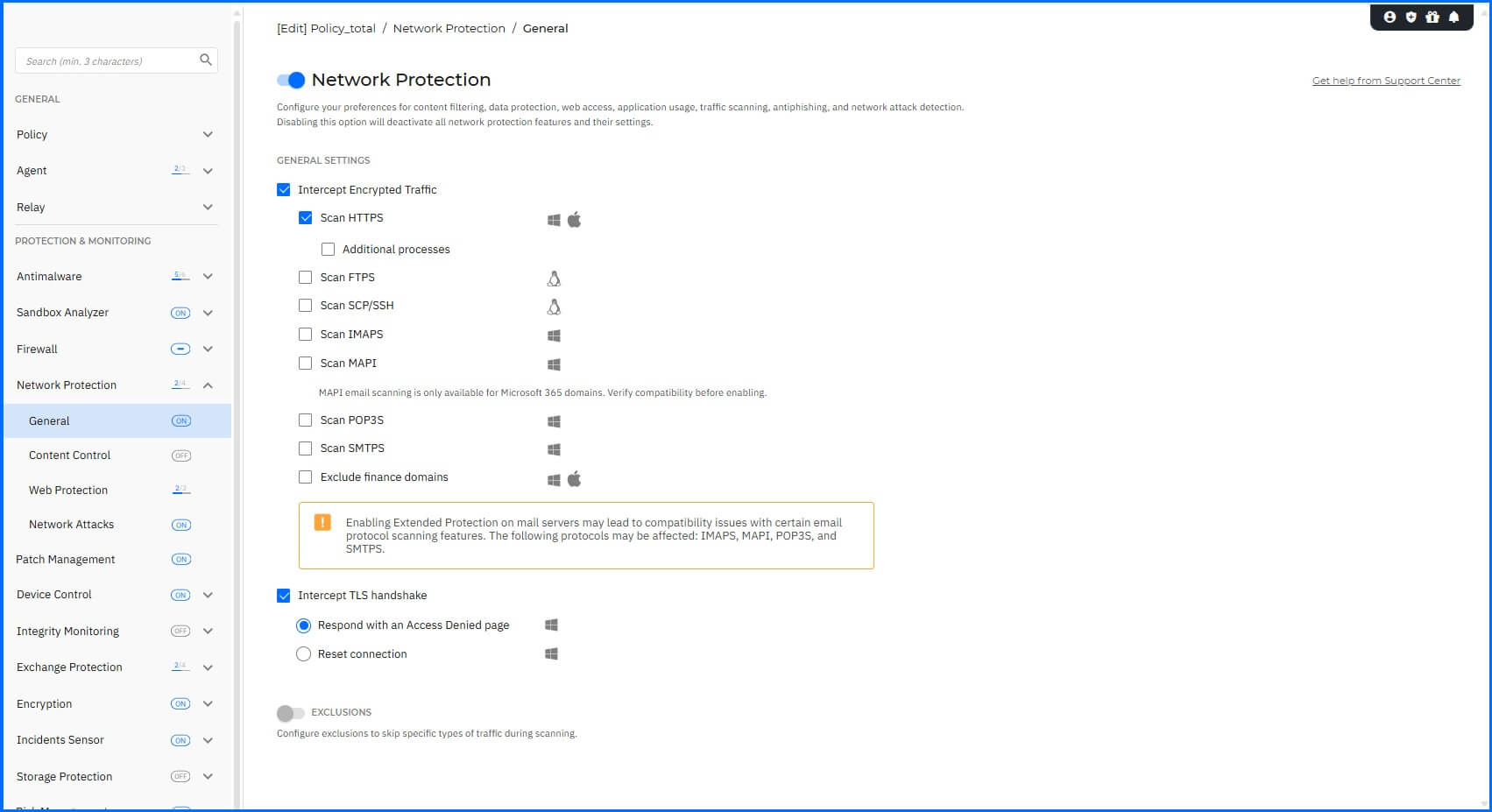 Network Protection Policy configuration |
On endpoints, Network Protection can be easily managed through Policy. For granular control, you can specify which protocols should be inspected by Secure Sockets Layer (SSL) for web traffic inspection. You can also define specific processes, such as those used by your Enterprise Browser.
Threat Intelligence Integration
The Network Attack Defense (NAD) solution continuously monitors the network traffic flowing to and from endpoints, enabling it to inspect network packets, headers, and payload data. This analysis provides valuable information about the traffic's source and destination. By integrating seamlessly with our Threat Intelligence platform, NAD gains access to a real-time database of reputation scores for domains, IP addresses, and URLs. These reputation scores serve as indicators of potential malicious activity.
Through active monitoring and analysis of network traffic, NAD identifies known malicious entities by leveraging the reputation scores provided by our threat intelligence platform. When network traffic attempts to access domains, IP addresses, or URLs with poor reputation scores, NAD promptly blocks access. This proactive approach effectively prevents endpoints from connecting to malicious websites, reducing the risk of malware infections, phishing attempts, and other network-based attacks.
By combining continuous network traffic monitoring, comprehensive inspection of packets, and integration with our robust threat intelligence platform, NAD offers a powerful defense mechanism. It detects and blocks access to known malicious entities, fortifying the security of endpoints and safeguarding sensitive data and systems from potential threats.
Content Scanner
When analyzing traffic flow, the NAD solution has the capability to recognize and identify executable code within the network packets. This includes file types such as binaries, HTML, JavaScript, or PDF files, often containing active content that can pose security risks. Upon identification of the executable code, the code is extracted and forwarded to an external content scanner for validation.
The content scanner modules specialize in analyzing the extracted code to determine its nature and assess if it poses any malicious intent or threat. The content scanner goes beyond simple file type recognition and employs advanced techniques to scrutinize the code for indicators of malicious behavior. It examines the code's structure, behavior, and embedded elements to identify any signs of malicious activity, such as attempts to exploit vulnerabilities, execute unauthorized commands, or propagate malware.
In addition to handling individual executable files, the NAD also supports the analysis of various archived files. Archives, such as .zip files or .eml (email) files, are commonly used to bundle multiple files or data together. NAD ensures that these archive formats are processed by extracting their contents and subjecting them to the content scanner's analysis. This comprehensive approach helps to identify potential threats even within compressed or bundled files.
Network Detection Capabilities
Both content scanning and reputation services offer effective protection at various stages of the kill chain. But what makes the NAD module truly powerful are the detection and correlation modules that provide Bitdefender EDR/XDR solutions with important insights about what’s happening across the organization.
Deployment Overview
NAD can be installed directly on each endpoint, including desktop computers, laptops, servers, and other devices connected to the network. In addition to individual endpoint deployment, NAD is also available as the XDR Network Sensor, which functions as a network appliance. The XDR Network Sensor is designed to analyze network traffic from devices like iPads that connect to the same network but do not have an agent installed. These devices, without endpoint-specific NAD installations, can still contribute to the overall network security by having their traffic captured and analyzed by the XDR Network Sensor. This approach ensures comprehensive visibility and protection for the entire network, while also protecting individual users that are working outside of the network perimeter.
By combining data from NAD-enabled endpoints and the XDR Network Sensor, the central correlation engine strengthens its understanding of the network environment. It can detect anomalies, identify potential threats, and generate alerts or take automated actions to mitigate risks promptly. This centralized approach ensures a unified and coordinated response to security incidents across the network.
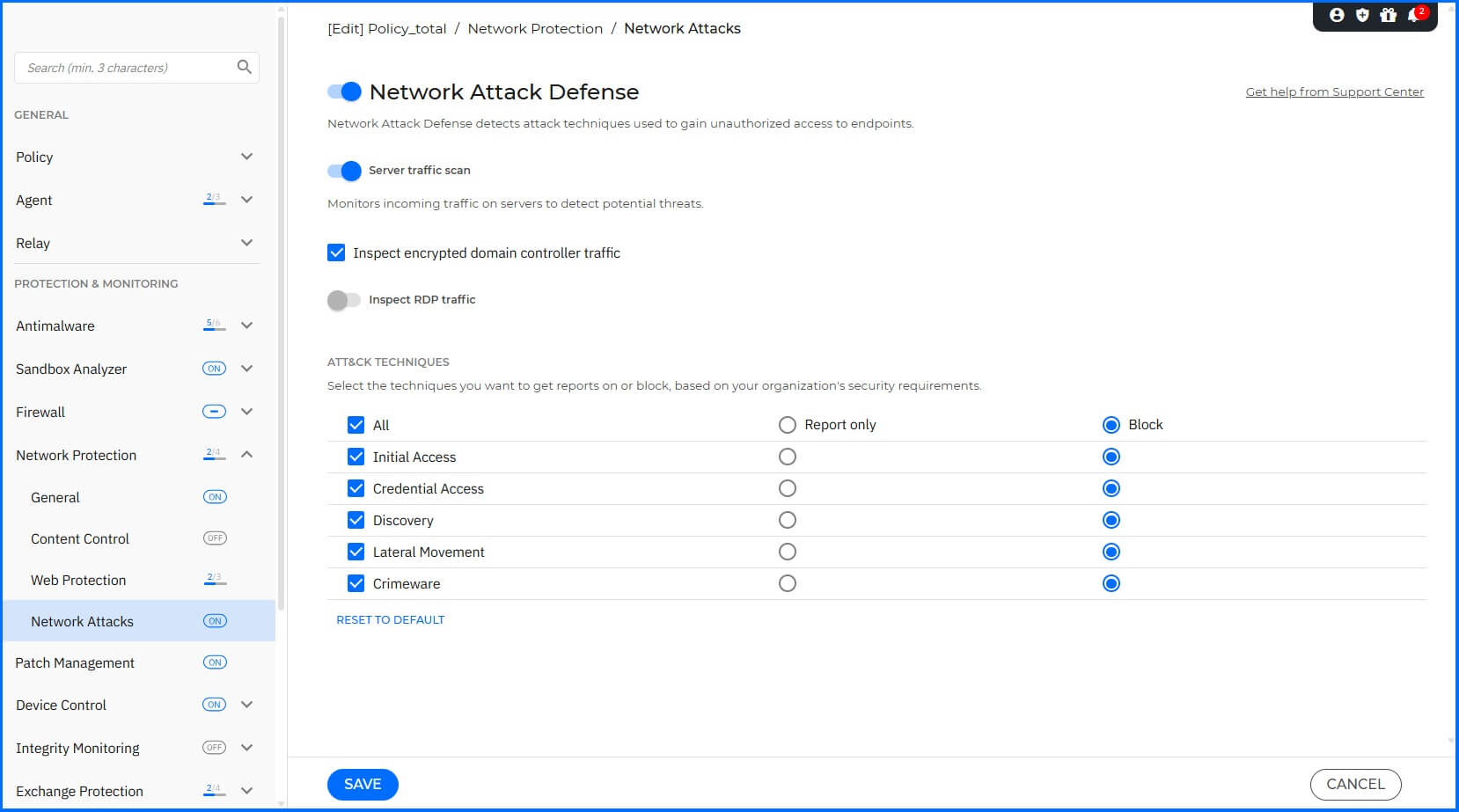 Network Attack Defense settings |
Detailed information about Network Attack Defense configurations can be found at our Bitdefender Support Center here.
Example of Detections
The NAD solution leverages multiple sources of data, a diverse range of protocol attribute extraction capabilities, and powerful machine learning and AI capabilities to detect and identify malicious or suspicious activity. The integration of different data sources, coupled with advanced analysis techniques, allows NAD to uncover patterns, anomalies, and indicators of compromise across the network. Through continuous monitoring and analysis, NAD can effectively identify potential threats, mitigate risks, and provide valuable insights for proactive threat response.
Let's explore a scenario where we can highlight the diverse methods through which NAD can prevent a security incident from escalating into a security breach. Please note that for the purpose of this example, we will focus solely on NAD, disregarding the other security layers integrated into our GravityZone platform.
Reconnaissance and Initial Compromise
In the context of initial access, which typically originates from external sources, NAD provides several mechanisms to prevent security incidents. Here's an overview of the capabilities offered by NAD:
Reputation-based Blocking: NAD leverages a reputation service that automatically blocks external sources involved in previous attacks. If an attacker's source has a known history of malicious activity, NAD prevents their access, fortifying the network against potential threats.
Email-based Attacks: When an attack is initiated through email, NAD examines the email protocol and extracts any malicious code embedded within it. By analyzing the content and behavior of the email, NAD can identify and neutralize email-based threats before they compromise the network.
Vulnerability Exploits: In situations where threat actors attempt to exploit vulnerabilities, NAD is equipped to detect and block network-based exploits. Notably, well-known exploits such as ZeroLogon, PrintNightmare, or EternalBlue are recognized by NAD, and appropriate measures are taken to prevent their success.
Behavioral Analysis: NAD employs advanced analytics to identify patterns associated with malicious activities. It can detect activities like port scanning or brute force attacks targeting protocols such as RDP (Remote Desktop Protocol) or HTTP. By recognizing these suspicious behaviors, NAD can swiftly respond and thwart potential threats.
Establishing Foothold
In the critical phase of establishing foothold and persistence following an initial compromise, NAD plays a pivotal role in preventing a security incident from escalating into a security breach. By focusing on the initial "call home" connection between malware and the Command & Control (C2) server, NAD employs various criteria to effectively block potential threats. As with the previous example, reputation-based blocking is highly effective, as threat actors often reuse existing infrastructure for attacks. But there are other methods of how NAD can identify “call home” connections:
Behavioral Analysis: NAD goes beyond reputation analysis and examines the behavior of malware when communicating with the C2 server. It can identify traffic patterns associated with well-known post-exploitation frameworks like Metasploit. By recognizing these patterns, NAD promptly intervenes to halt unauthorized activities and maintain the security posture.
Custom-Built and Unseen Malware: NAD's sophisticated analysis capabilities extend to identifying C2-style traffic exhibited by custom-built and previously unseen malware. Through advanced machine learning and AI techniques, NAD can detect anomalies in communication behavior, even in the absence of prior knowledge, effectively mitigating emerging threats.
Detection of TOR/Onion Traffic: NAD offers the ability to recognize specific traffic patterns associated with TOR/Onion networks. This capability proves particularly valuable in combating certain ransomware families that leverage these networks for communication with their C2 infrastructure. By identifying TOR/Onion traffic, NAD strengthens defenses against ransomware attacks.
Lateral Movement
In situations where threat actors have successfully compromised the network and switched to stealth mode, NAD proves highly valuable by providing critical data to the central correlation engine that powers our EDR/XDR platform. This integration enables enhanced visibility and context, allowing for more effective threat detection and response.
NAD is effective in identifying malicious operations that may be concealed or harder to detect without this additional context. Here are some examples of how NAD contributes to identifying and understanding such activities:
Active Directory Domain Controller Activity: NAD can identify connections to Active Directory Domain Controllers, which are crucial components of network infrastructure. By monitoring and analyzing the queries and interactions with the Domain Controller, NAD can identify abnormal or unauthorized activities, such as unauthorized user enumeration or attempts to escalate privileges. With the 'Inspect encrypted domain controller traffic' option enabled, NAD inspects encrypted SMB, RPC and Kerberos traffic. This allows for the detection of highly sophisticated attacks, such as the use of forged Kerberos tickets (e.g., Golden Ticket), by identifying anomalies and behavioral patterns within the authentication stream. This provides essential insights to the central correlation engine for addressing advanced forms of lateral movement and privilege escalation.
Lateral Movement Technologies: NAD recognizes common techniques used for lateral movement within the network, such as Windows Management Instrumentation (WMI) calls. By detecting and flagging these activities, NAD provides valuable insight into potential lateral movement attempts, enabling swift response and containment.
Remote Code Execution: NAD comprehends various technologies employed for remote code execution, including Remote Procedure Call (RPC), remote scheduled tasks, and Distributed Component Object Model (DCOM)-based execution. By understanding the behavior and characteristics of these technologies, NAD can identify suspicious instances of remote code execution, aiding in the detection and prevention of unauthorized access and activities.
Data Exfiltration
When it comes to data exfiltration attempts, NAD serves as a proactive defense mechanism, actively identifying and thwarting such activities while offering additional insights. As with all previous cases, reputation service would block connections to known malicious destinations. But NAD employs various other methods to detect and prevent data exfiltration, including:
Pattern Recognition with Machine Learning: NAD utilizes powerful machine learning algorithms to identify patterns associated with malicious data exfiltration. By continuously analyzing network traffic, NAD can recognize suspicious data transfer patterns, such as large volumes of sensitive information being transmitted to an unauthorized destination. When such patterns are detected, NAD takes immediate action to block the exfiltration attempt.
Content Analysis: NAD not only analyzes individual files but also inspects archives, such as zip files, to identify potential hidden or compressed data that may be exfiltrated. By scanning the contents of these archives, NAD ensures comprehensive protection against data leakage through various file formats.
Credential Exfiltration Detection: NAD is capable of identifying attempts to exfiltrate credentials, such as usernames and passwords. By monitoring network traffic and analyzing authentication protocols, NAD can swiftly detect and block unauthorized attempts to send sensitive login information outside the network.
Recommended Content
To learn more about the technologies behind the Protection layer, we recommend reading the next article Malware Protection.
More Resources
Bitdefender Network Attack Defense official website: Network Attack Defense
GravityZone NAD Stops C2 Attacks: AV-Comparatives NGFW Egress C2 Certification Test Analysis