Threat Intelligence – Bitdefender TechZone
Gain comprehensive insights into emerging cyber threats, exploit vulnerabilities, and enhance your security infrastructure with Bitdefender's high-quality APIs and feeds.
Building a comprehensive threat intelligence solution can be challenging. Not all organizations have the resources or expertise to collect, process, and store a vast amount of threat data while keeping it up to date.
Bitdefender Threat Intelligence processes data on cyber threats, actors, and their tactics, making it a foundational component of your organization's cybersecurity defenses. It can help you identify a broad range of IoCs like IP addresses associated with known ransomware groups, file hashes of trojans, or any other relevant artifact for your security operations. For example, Bitdefender Threat Intelligence can help you prioritize vulnerability management by providing information on current popular exploits actively used in the wild associated with CVEs, old or new, together with more details, including CVSS scores.
In this technical brief, we discuss how we collect data and how our Reputation, Operational, and Tactical Intelligence capabilities can improve the efficiency of your security operations.
Telemetry
Our unique advantage lies in the consolidation of the massive quantities of Indicators of Compromise (IoCs) in real-time from multiple sources including live systems in our Bitdefender Global Protective Network (GPN). Real-time IoCs like IP addresses or domains of C2 servers are further correlated by internal security researchers, threat hunters, security analysts, and research and development specialists in the Bitdefender Labs, focusing on cloud, emerging technologies, and machine learning. By analyzing this comprehensive dataset, we can identify suspicious activity, potential security threats and vulnerabilities in real-time as they appear and share them with partners to enhance the defender's capabilities.
We extract TI from our telemetry in compliance with data privacy regulations like the GDPR. Information is anonymized before it reaches our cloud, and we do not share information about the organization that is the source of the data or any personal identifiable data (PII).
Global Protective Network
Bitdefender Global Protective Network (GPN) is a series of interconnected cloud services strategically distributed worldwide, offering comprehensive protection and support to various products. Leveraging a distributed architecture, GPN safeguards hundreds of millions of systems, consumer devices, the technology of licensing partners from the OEM ecosystem, and more, processing an astounding 50 billion daily threat queries from these systems.
GPN enables two-way communication with protected technologies. First, it augments our detection engines for partners by delivering real-time security verdicts. Second, it aggregates information from these sources to continuously improve telemetry. This includes data from anti-spam, anti-phishing, and anti-fraud technologies, along with URLs identified and processed by Bitdefender global install base, internal crawling systems, email traps, honeypots, and monitored botnets.
Threat Intelligence Solution
Bitdefender provides a highly scalable Threat Intelligence (TI) Solution that can be easily integrated into existing security infrastructures by unified API. TI solution was designed to handle many concurrent requests from end-users worldwide, offering low-latency and high-throughput distributed query services.
There are two service types that are available when using the Threat Intelligence solution:
APIs - exposes threat intelligence, aggregated into Threats (collections of related IoCs), via a REST API. This Human-Readable Threat Intelligence (HRTI) helps you get maximum visibility into threats from isolated indicators and make informed decisions about potential attacks. Responses are typically fast, formatted according to a fixed schema, and well-suited for automated use cases where rapid and accurate IoC verification is crucial. Additionally, the service offers timely threat updates valuable for your forensic investigations.
Feeds - delivered in a fixed format, the information is constantly pushed to internal storage and kept readily available for extended periods (often a 7-day window). You can easily access and retrieve this stored data using utility APIs. Focused on real-time detection and prevention, these continuously updated feeds deliver IoCs with minimal false positives. You can integrate Machine-Readable Threat Intelligence (MRTI) feeds seamlessly with your SIEM, EDR/EPP, NGFW, WAF, DNS Security, IDS/IPS, CDN, and CASB solutions. This empowers you to manage dynamic blacklists/whitelists of IoCs, effectively preventing the spread of new malware variants and enhancing your defenses against previously identified threats.
Splunk Integration
For organizations leveraging Splunk, the Bitdefender Threat Intelligence for Splunk solution provides a dedicated, seamless integration that significantly enhances your existing Security Information and Event Management (SIEM) capabilities. The includes:
Real-time ingestion of IoCs (domains, IPs, URLs, file hashes, CVEs).
Actor and malware family attribution correlated to IoC.
Confidence and severity scoring for prioritization.
Prebuild dashboards, such as Operational Feeds Overview, Operational Feed Details, Reputation Feed Details, and Correlation Alerts, provide immediate context on active threats. Furthermore, integration with Splunk Enterprise Security allows you to create custom correlation searches and alerts, enabling faster incident response.
Bitdefender IntelliZone
Bitdefender IntelliZone is our Threat Intelligence Portal, exposing the capabilities of our Threat Intelligence solution. It provides UX-optimized, human-readable visualizations of Threats and Indicators of Compromise (IoC). IntelliZone integrates search and navigation functionalities, offers AI-powered user support, and includes other valuable features, all optimized for the security analysts.
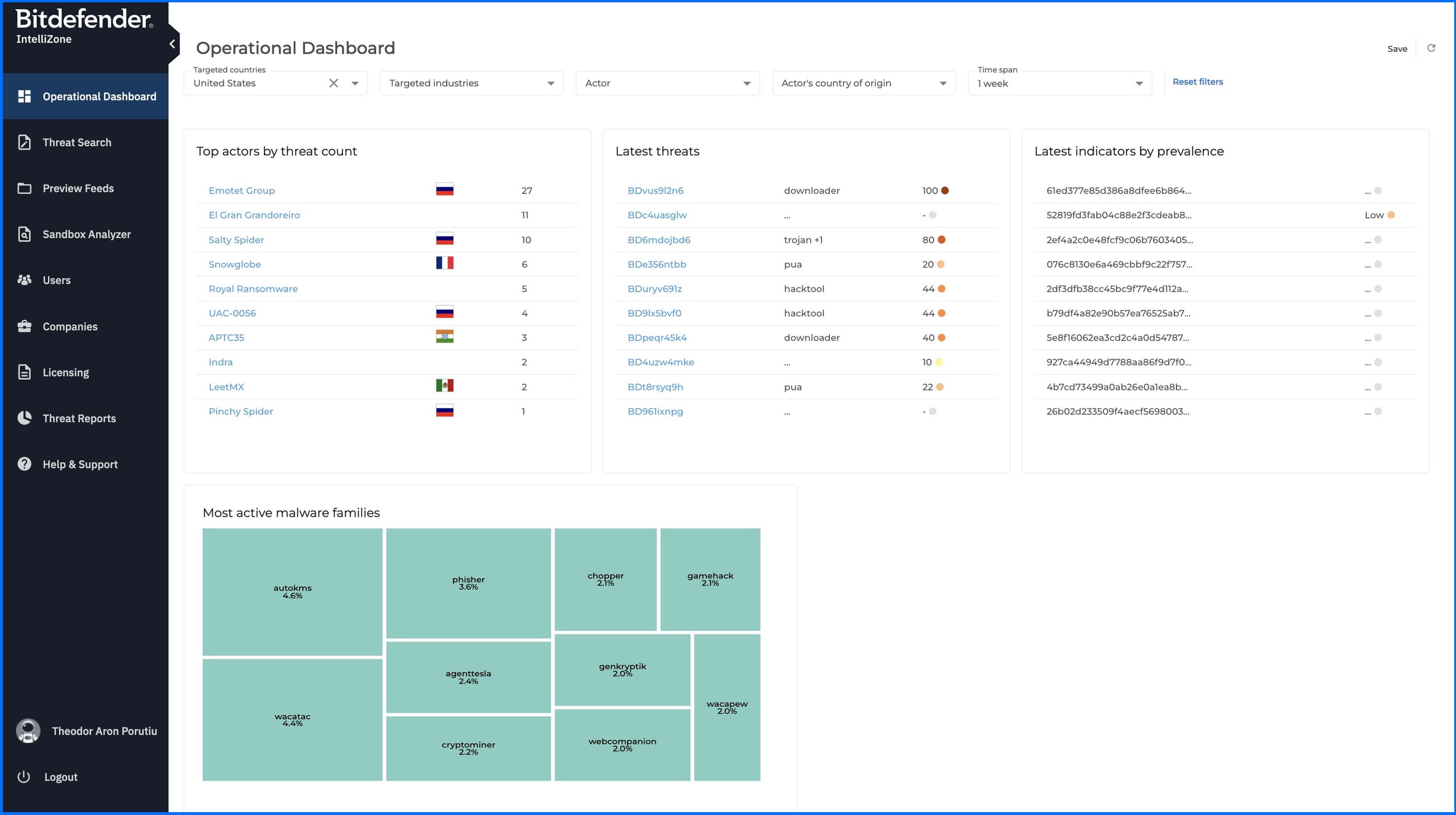
IntelliZone functionality
Operational Dashboard
IntelliZone features an Operational Dashboard that you can use to keep up with threat landscape.
Higher Visibility: Monitor actors, latest threats, latest indicators, and malware families, based on your area of interest.
Highly Customizable: The dashboard can be filtered to focus on particular countries, industries, actors, actors' countries of origin, and time span.
Threat Search
IntelliZone Threat Search lets you search for indicators of compromise (IOCs) using either simple or cumulative searches.
Simple Search: Locates all known threats associated with a specific IOC. You can search by domain, URL, IP address, hash, or certificate hash.
Cumulative Search: Identifies threats based on their connection to multiple attributes. For now, you can filter the search results by using the following criteria (more filter criteria are permanently added):
threat_actor - name or alias of the actor.
malware_threat_family - name of the malware family contained within.
country - country of origin of the threat.
industry - industry the threat originated from.
device_type - type of device and operating system that the threat uses to penetrate victims’s defenses.
min_score – filter to search only for threats with a threat score equal to or higher than this value.
min_confidence – filter to search only for threats that have an attribution confidence equal to or higher than this value.
indicator - An Indicator of Compromise associated with the threat.
For example, if you want to search for IOCs with a minimum score of 60 associated with the United States and the United Kingdom, you would use the following autocompletion-assisted syntax:
country "United States" AND country: "United Kingdom" AND min_score: "60"
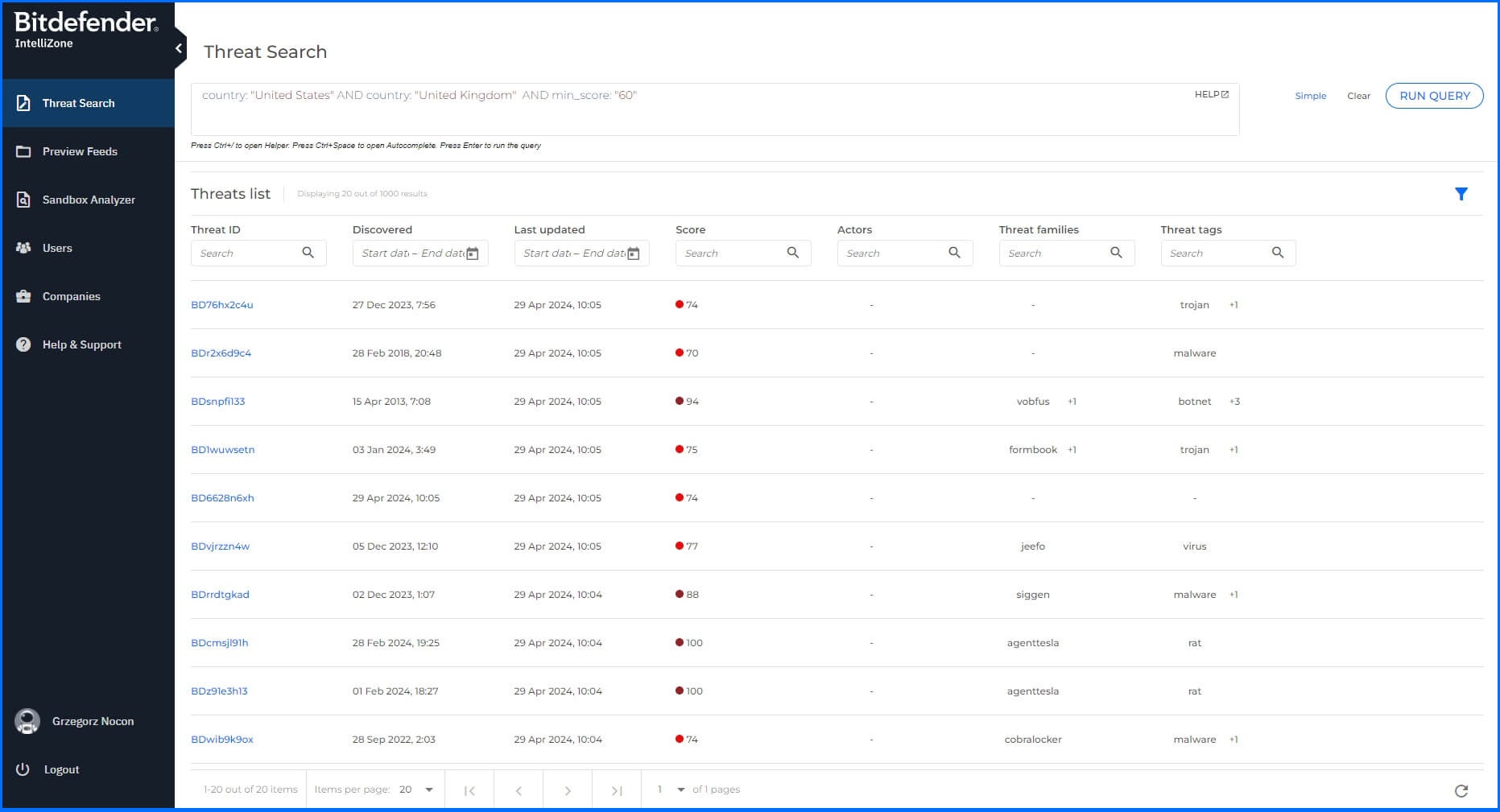
Both searches (simple, cumulative) allow you to retrieve the latest 20 threats containing the specified indicator, with the option to view detailed information about each threat in an optimized format.
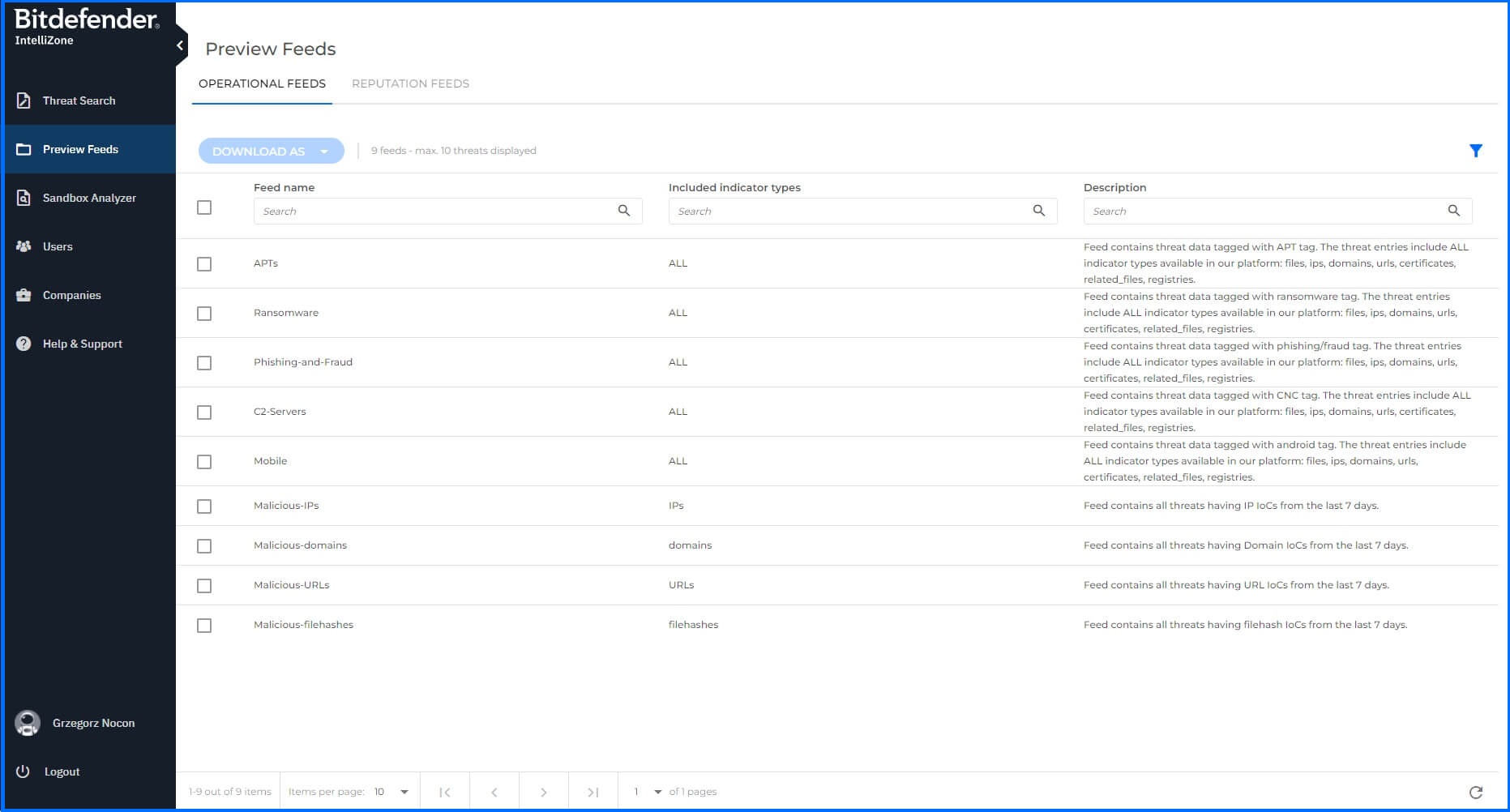
Preview Feeds
The Preview Feed section lets you download all the Operational and Reputation Feed samples described above in this article. It is important to note that these feeds are limited to 10 threats.
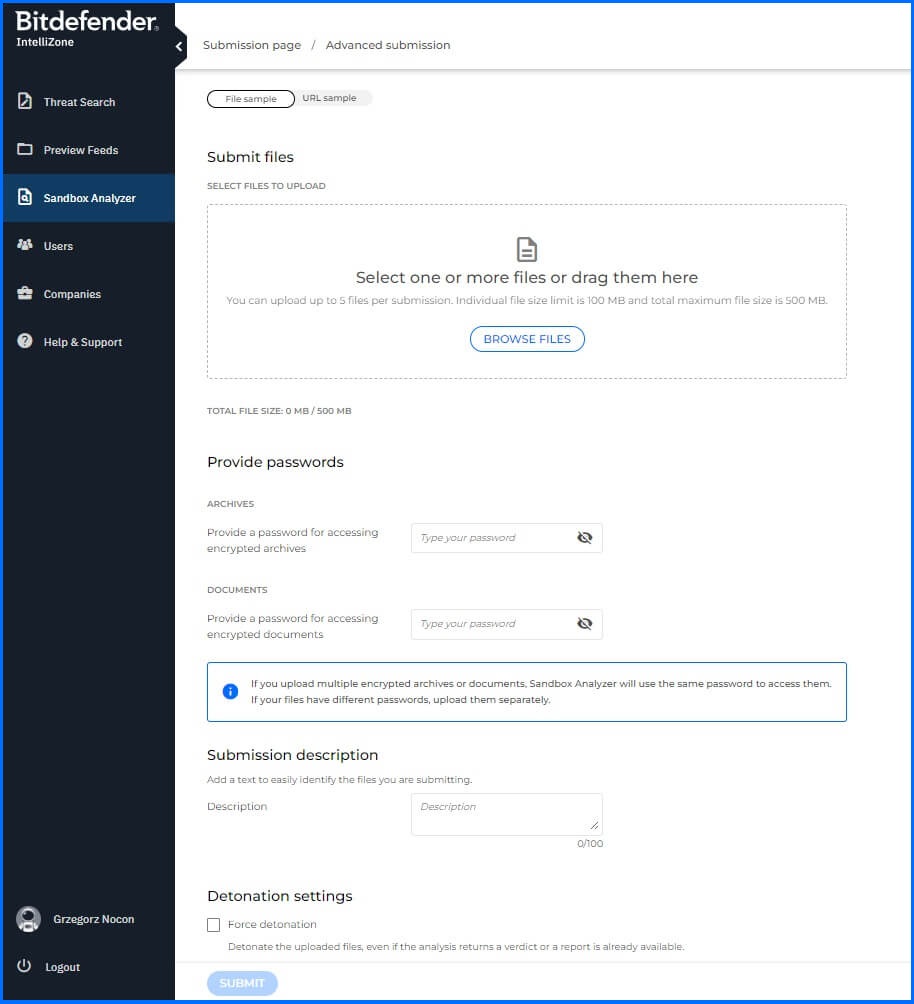
Sandbox Analyzer
Even if a file or URL isn't known to us, you can still investigate its potential for malicious behavior. The Sandbox Analyzer allows you to detonate it (for files) or analyze it (for URLs) in a safe, isolated environment. This allows you to observe the malware's behavior firsthand, identifying its origin, family, and the techniques it uses, all within a matter of minutes. You can choose between a simple or advanced submission option.
Simple Submission: You can upload a single file.
Advanced Submission: You can submit one or more files at once. Additionally, you can submit password-protected files and include a descriptive comment for each file. This option also allows you submit URLs and query the reputation service.
When you submit a file, you will receive a comprehensive analysis report within minutes. It includes information about known threat actors and the family of the detected infection, details on the detection process, including the security mechanisms responsible for identifying the infection's behavior, and its mapping to Mitre techniques. The system can learn from the threat's behavior, presenting a timeline display of the changes it attempted to make to the system, along with tree graphs depicting its interactions and structure. Additionally, it captures a screenshot of the message or error the user encounters when the system is infected, such as a ransomware note.
A detailed description of how our Sandbox service works and how reports look can be found here.
IntelliZone demo
Reputation Threat Intelligence
Reputation Threat Services collect extensive amounts of verified threat data with a high level of accuracy and a low incidence of false positives. They provide all information in real-time and present it in a simplified format, allowing you to enhance your detection and filtering efficacy.
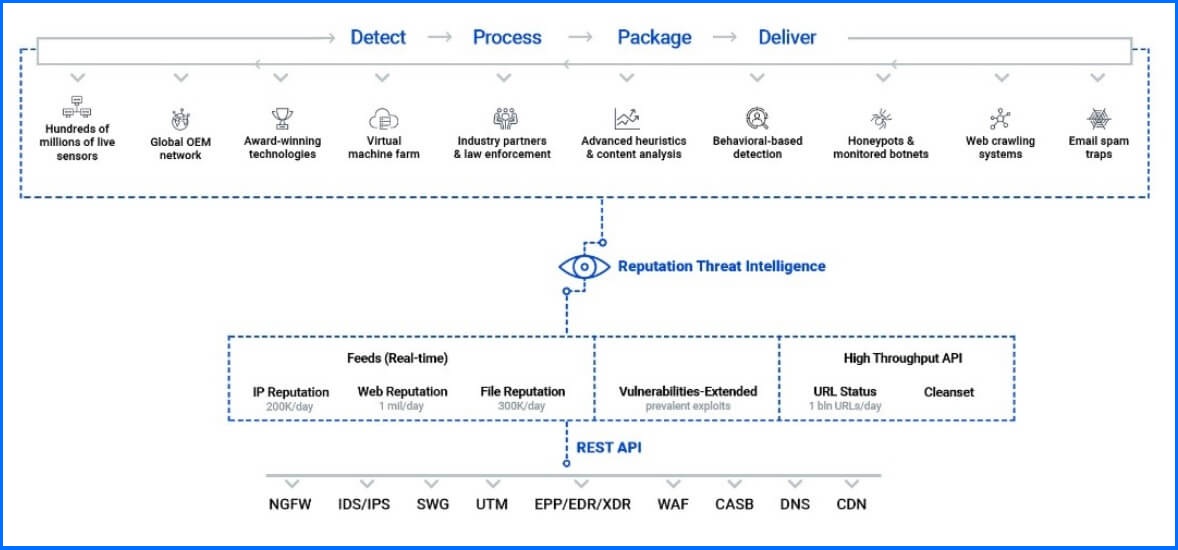
Feeds
IP-Reputation (real-time) - The IP Reputation Feed empowers you with a real-time stream of Machine-Readable Threat Intelligence (MRTI) on malicious IPs detected by our live sensors. It includes a set of key information for each Indicator of Compromise (IoC) delivered, allowing you to effectively parse the data, classify it, and prioritize it based on your customized criteria. This way, you can narrow down the data to what is most relevant for your business needs. IP Reputation feeds deliver IoCs from our live systems along with crucial threat context, making it easy to update IP blocklists in real time:
Tags - Indicate the type of threat or specific attacks associated with the IP.
Severity and Confidence - Assess the level of threat and confidence in the verdict.
Ports and Protocols – Identify the ports and protocols used by the IP in its malicious activity.
Countries - List up to 5 countries associated with the IP.
Domains - Show the 5 most recent domains resolving to the IP.
Popularity - This value (ranging from 1 to 5, with 5 being the most popular) highlights the prevalence of attacks, potentially influencing rule priority. If the IP's popularity changes, an updated record is sent.
First seen, timestamp, and TTL - This information advises you on how long to consider this detection valid.
Web-Reputation (Real-time) - The Web Reputation Feed delivers a continuous stream of threat information about malicious domains and URLs detected by our live sensors. It provides a set of key details for each Indicator of Compromise (IoC), allowing you to effectively parse the data, classify it, and prioritize threats based on your customized criteria. This way, you can easily narrow down the information to what is most relevant for your business needs. URLs are conveniently grouped and presented with their attributes for a clear understanding of each threat.
File-Reputation (Real-time) - This real-time stream delivers Machine-Readable Threat Intelligence (MRTI) on malicious file hashes detected by our active sensors. Each Indicator of Compromise (IoC) provides you with essential details, empowering you to efficiently analyze and categorize the data based on your specific criteria. For your convenience, files are grouped and presented with their attributes, offering a clear picture of each potential threat.
Vulnerabilities-extended - This Vulnerability Feed provides you comprehensive information about software products with documented vulnerabilities (CVEs with CVSS scores). Additionally, the feed includes exploit data and real-time detection of vulnerable files, ensuring you have actionable threat context. Data is updated every 6 hours for continuous vigilance. Presented in JSONL format, the feed is tailored for seamless integration scenarios involving both Machine-Readable Threat Intelligence (MRTI) and Human-Readable Threat Intelligence (HRTI), empowering you to understand risks and implement effective mitigations.
APIs
IP Reputation API - The IP Reputation API is a service that allows you to query malicious information about a specific public IP, IPv4 or IPv6. When such information is found, it is delivered with additional context, including a timestamp and a TTL ("time-to-live").
URL Status API - You can use the URL Status API to retrieve information about a specific URL, domain, or subdomain. Once your request is submitted, the URL is checked against Bitdefender threat intelligence datasets. If available, information on whether the URL is safe will be returned, including additional details such as the type of threat found in the URL (if it is deemed unsafe) and the category of the content available on the URL.
Dual Network Service (IP Reputation + URLStatus API) - You can use this dual service to query a specific public network resource, whether it is a public IP or a URL, domain, or subdomain.
File Reputation API - The File Reputation API allows you to check a specific file hash (MD5, SHA256, SHA1) against Bitdefender's Threat Intelligence. If the file is known to be malicious, the reply will confirm its malicious status and provide actionable threat context like malware type, a severity score, and more.
Cleanset API - The Cleanset API allows you to check a specific file hash (MD5, SHA1, SHA256) against Bitdefender Threat Intelligence databases and receive information on whether the file is known to be clean or not. The primary use case for this service is to reduce false positives detected by other security tools. Additionally, it can be used to prioritize a long list of hashes before undergoing a more extensive investigation.
Dual Filehash Service (File Reputation + Cleanset) - You can utilize this dual service to check a specific file hash against Bitdefender Threat Intelligence. If the file is recognized by Bitdefender, the response will confirm whether the file is known to be clean or malicious.
Vulnerabilities API - This API enables you to query a specific CVE (Common Vulnerabilities and Exposures) against Bitdefender Threat Intelligence search for specific CVEs using customized criteria such as CVE, vendor name, product name, and CVSS score, or retrieve a list of exploits currently in use or known to exist.
Operational and Tactical Threat Intelligence
With Operational Threat Intelligence, you gain comprehensive global visibility into threats such as malware, APTs, zero-days, and C2 communication channels and active threat actors. Operational TI is based on raw data extracted from our live systems that is processed by analysts in the Bitdefender Lab to enrich it with more actionable threat context.
The Information is delivered in human-readable formats within a few hours of being collated, making it readily usable for your SOC analysts. This extends your visibility, allowing you to gain a broader understanding of the global threat landscape. It helps streamline alert triage, improve the efficiency of your security operations, and reduce investigation and response time by providing you with vital context around threats and revealing their root cause.
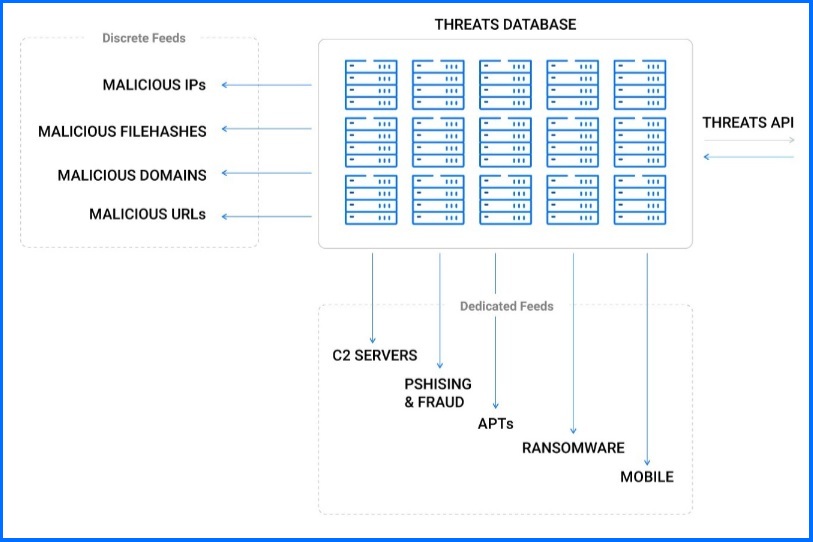
APIs
Threats API - The Threats API is an Operational Threat Intelligence service that aggregates information into Threats, which are collections of related IoCs (indicators of compromise) used by malicious actors to carry out attacks. This human-readable threat intelligence (HRTI) is designed to assist your security experts and SOC/MDR/MSSP analysts when investigating incidents, hunting threats, or researching the global threat landscape to improve security posturing. Partners can search for threats with these filters:
URLs - includes IPs, domains or subdomains, and URLs
Hashes - includes file hashes (SHA-256, MD5, SHA-1)
Certificate hashes (SHA1)
Country codes
Industry
Penetration media type (such as endpoint, server, mobile device, printer, router, IOT, cloud storage, external drive)
Actor ID
Malware family ID
Threat score (minimum value)
Confidence (minimum value)
Actors API - The Actors API provides Tactical Threat Intelligence on threat actors associated with the threats. It exposes dynamically calculated fields based on operational data, along with descriptive knowledge about the specifics of each actor.
Feed
APTs Feed - Advanced Persistent Threats (APT) feed contains the latest Threats coming from Bitdefender's Analysts as a result of our own Lab analysis, sometimes using a distilled partner or public reports. APT attackers employ multiple dynamic infrastructure items, using far more sophisticated files and TTPs; unlike regular attacks, APT attacks unfold at a slower pace and establish a longer persistence. APT feeds contain:
File hashes of malware files used in APT attacks harvested from lab analysis. The hash types supported are MD5, SHA1, and SHA256. Full threat information and indicators are presented together.
IPs used in APT attacks in the wild to propagate malware collected from lab analysis. Full threat information and indicators are presented together.
Domains, Subdomains, and URLs used by the malware in APT attacks collected from lab analysis. Full threat information and indicators are presented together.
Phishing-and-fraud - Phishing and fraud feeds contain the domains and URLs used by malware in phishing or fraud attacks. Most of these (>90%) are usually short-lived, lasting less than a day. Additionally, the feeds include other indicator types, such as files, IP addresses, certificates, and related files. Full threat information and indicators are presented together.
Ransomware - The Ransomware feed contains the latest threats identified by Bitdefender's analysts. Ransomware attacks behave differently than regular ones, as they typically contain at least a ransomware encrypting-payload file or artifacts indicating a Ransomware-as-a-Service (RaaS) infrastructure. The threat entries include all indicator types available in our solution: files, IP addresses, domains, URLs, certificates, related files, and registries.
C2 Servers - C2 Servers feed contains IP addresses and domains of the Command and Control (C2) servers used by malware to propagate, harvested from both live systems and lab analysis. The IPs are in IPv4 format. The feed groups them under "Indicators/IPs" within threat entries and presents them with their associated attributes. Additionally, the feeds include other indicator types, such as files, certificates, related files, and registries. Full threat information and indicators are presented together.
Mobile - This feed contains file hashes of malware files used in mobile attacks. The supported hash types are MD5, SHA1, and SHA256. It also includes IPs and domains (including subdomains) used in mobile attacks or as part of a mobile scam infrastructure. Full threat information and indicators are presented together.
Malicious Filehashes - Contains file hashes of malware files harvested from live systems and lab analysis. The hash types supported are SHA256, MD5, and SHA1. Hashes are grouped in threats under Indicators/Files and presented with their attributes.
Malicious IPs - Contains IPs used by malware in the wild to propagate collected from live systems and lab analysis. The IPs are in IPv4 format. IPs are grouped in threats under Indicators/IPs and presented with their attributes.
Malicious URLs - Contains the URLs used by the malware collected from live systems and lab analysis. URLs are grouped in threats under Indicators/URLs and presented with their attributes.
Malicious-domains - Contains the Domains and Subdomains used by the malware collected from live systems and lab analysis. Domains are grouped in threats under Indicators/Domains and presented with their attributes.
Recommended Content
To learn more about the technology behind the GravityZone platform, we recommend reading the next article Cloud and Virtualization Optimization.
More Resources
Bitdefender Threat Intelligence official website: Bitdefender Advanced Threat Intelligence
To request a demo, you can click here: Advanced Threat Intelligence Inquiry
Bitdefender IntelliZone Guided Tour: IntelliZone Guided Tour with Click & Discovery
Discover the IntelliZone full potential with our dedicated video masterclasses: Bitdefender Masterclass
Cyberthreat Real-Time Map: Real-Time Map