Cloud and Virtualization Optimization – Bitdefender TechZone
Optimize Virtualization and Cloud Security with Bitdefender's advanced security solutions for virtualized environments, reducing resource consumption and improving performance.
Cloud and virtualization offer resource optimization, server consolidation, scalability, and cost savings. However, traditional antivirus struggles in these environments, causing performance issues, update storms, disk bottlenecks, and incompatibility with non-persistent desktops, ultimately limiting the full potential of cloud and virtualization's efficiency.
Bitdefender GravityZone tackles these challenges. It is an integrated Cloud Workload Security Platform purpose-built to protect servers, containers, and virtual desktop infrastructure (VDI) workloads. It achieves this through comprehensive integrations with technologies from Citrix, Nutanix, VMware, and public clouds like Amazon AWS and Microsoft Azure.
In this article, we delve deeper into our concept of security for virtual environments and explore how this approach integrates with cloud infrastructure.
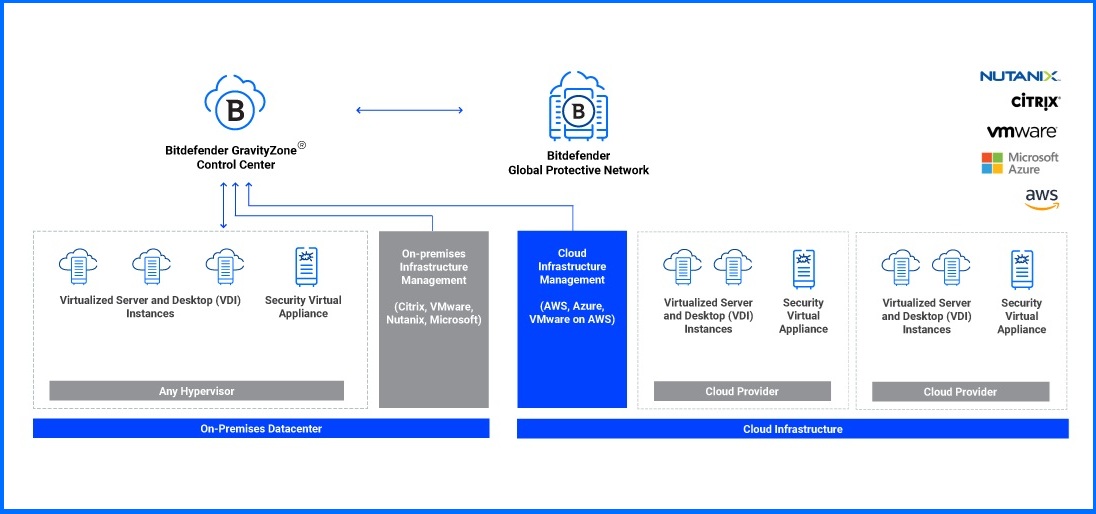
Security for Virtualized Environments
GravityZone Security for Virtualized Environments (SVE) includes Security Virtual Appliances (SVA) to optimize performance and reduce operational costs. SVE is built from the ground up for virtualization and cloud computing, allowing linear scaling with built-in features such as high availability (to avoid security service single point of failure) and load distribution.
Security for Virtualized Environments Architecture
SVE technology is available in two architectures:
SVE - NSX Guest Introspection (Bitdefender Agentless):
Leverages VMware Technology: SVE leverages VMware's NSX Guest Introspection technology.
Centralized Antimalware Services: Bitdefender provides centralized antimalware services managed by a Security Virtual Appliance (SVA).
Remote Scanning via NSX: The SVA is deployed on a host and utilizes NSX functionality to perform agentless scanning of guest VMs.
SVE Multi-Platform:
Independent Operation: SVE operates independently of the hypervisor, eliminating the need for hypervisor integration.
Security Components: Bitdefender provides two key components for SVE Multi-Platform:
Security Virtual Appliance (SVA): The SVA offloads scanning and caching functionality.
Bitdefender Endpoint Security Tools (BEST) Integration: BEST offers a comprehensive security suite, including features like Advanced Threat Control, Exploit Protection, Malware Protection, Network Protection, Patch Management, etc.
SVE utilizes multi-level caching and scan offloading to minimize CPU, memory, and storage impact on endpoint security. Its architecture also integrates intelligent scheduling and anti-storm mechanisms to optimize security scans. By leveraging intelligent caching and offloading, antimalware scanning engines and threat intelligence databases are centralized on Security Virtual Appliances. This centralization reduces the number of updates required in non-persistent environments like VDI clients.
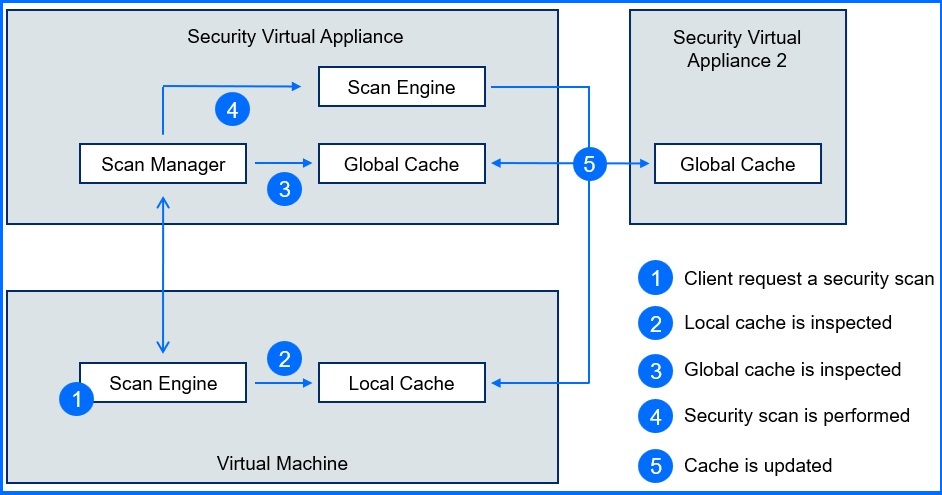
Scan Engine leverages local and global SVA caches for faster lookups. If no match is found, the SVA updates both caches while scanning, ensuring global synchronization across SVA’s. To further optimize performance, caches are pre-populated with known system files and learning by deduplicating scans as the environment is analyzed. Scanning and caching functionality is based on file segments, minimizing data transfer between BEST on a virtual machine and the SVA.
If there are connectivity issues or unexpected failures, the local agents will automatically search for an alternative SVE appliance. Alternatively, they will revert to local scanning as a fallback option. Despite this preference for central scanning, agents can still provide complete security independently if needed. For more configuration details, check out our Bitdefender Support Center here.
Our architecture streamlines virtual machines Golden Image deployments, saving you from headaches caused by missing or duplicate machines. Traditional security solutions often create challenges during golden image creation, imagine you include the endpoint agent in the image – cloning can lead to problems like unnecessary license consumption, compromised reporting, or even unprotected virtual machines.
vCenter Integration
Integrating the GravityZone Cloud Console with vCenter version 6.7 and above streamlines security operations in virtual environments and offers:
Effortless Agent Deployment: Facilitates the seamless installation of the BEST agent when the BEST with Relay role is already deployed within your network.
Unified Security Management: Provides a centralized platform to manage both Security Virtual Appliances (SVA) and BEST agents. This enables comprehensive security tasks, including initiating scans, performing risk and patch assessments, applying patches, and isolating compromised endpoints.
Automated Inventory Synchronization: GravityZone automatically populates its inventory directly from vCenter via API. This synchronization brings in your complete vCenter structure, encompassing Folders, Datacenters, Compute Resources, Cluster Compute Resources, Host Systems, Resource Pools, Virtual Apps, and Virtual Machines, all organized hierarchically. This ensures your vCenter inventory layout (from either the Hosts & Clusters or VMs and Templates views) is accurately reflected. Please note that vCenter-imported items cannot be deleted or moved directly within the GravityZone console.
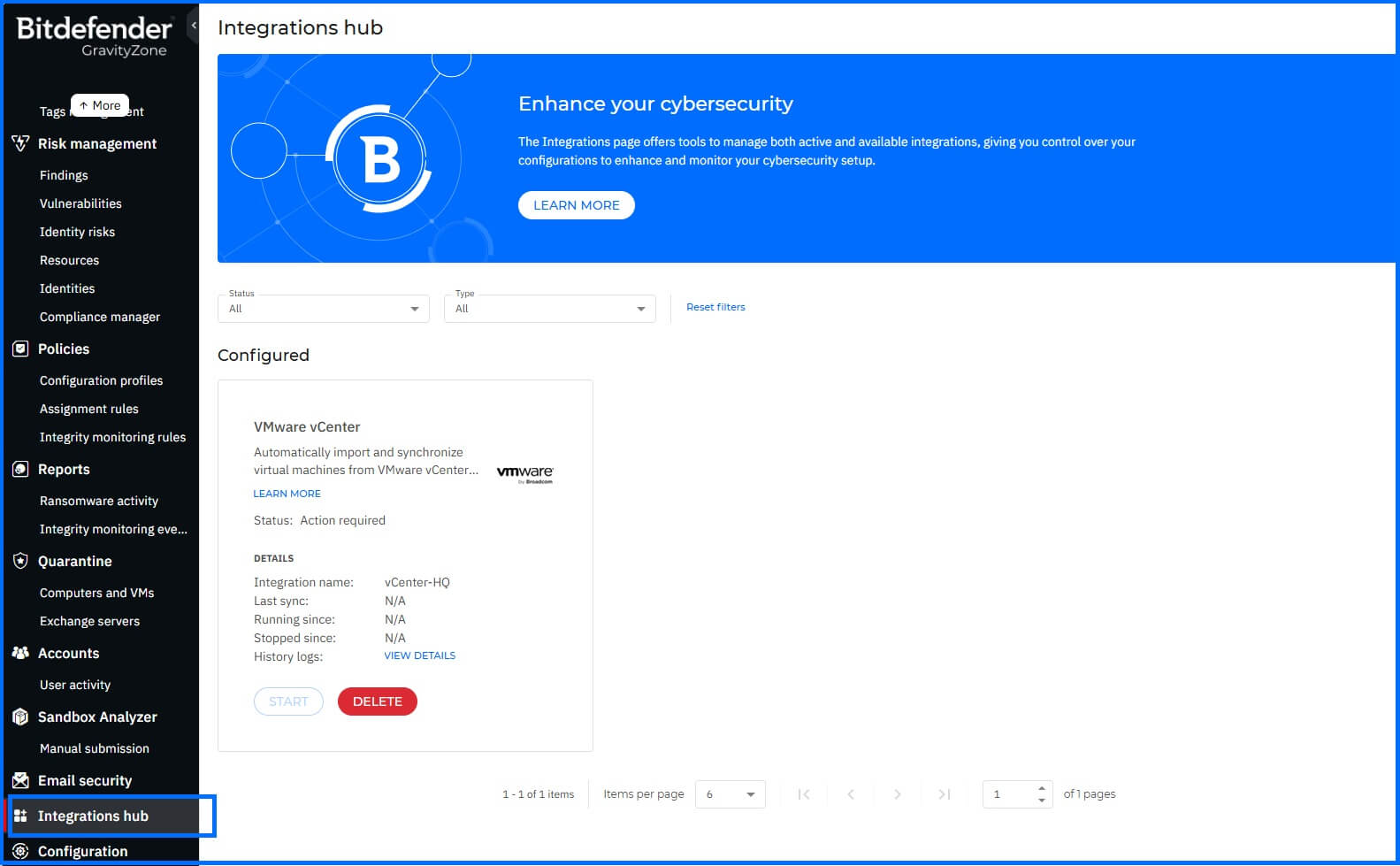 vCenter integration in the Integration Hub of GravityZone. |
Detailed information about vCenter integration can be found at our Bitdefender Support Center here.
Security for Virtualized Environments demo
Security for Cloud
Building on our previous discussion about SVE's adoption for multi-platform compatibility, let us delve deeper into this concept to explore the possibilities of cloud deployment in Amazon AWS and Microsoft Azure.
Security for Amazon AWS (EC2)
To maximize the benefits of cloud implementation, you have the option to choose between two models of AWS integration.
Firstly, Bitdefender Security for AWS protects Amazon EC2 instances running Windows or Linux operating systems. To protect your Amazon EC2 instances, you must install the Bitdefender Endpoint Security Tools agent on each one. Agents include modules like Malware Protection, Advanced Threat Control, Device Control, Content Control, Network Attack Defense, Encryption, and Risk Management.
Security agents on your EC2 instances send scan requests to the closest security server hosted by Bitdefender in your AWS regions, which performs the actual scan. These servers are in multiple Amazon availability zones and based on the AWS region where they are hosted, EC2 instances will automatically establish a connection with the nearest server, so you don't need to deploy them in your environment. For more configuration details, check out our Bitdefender Support Center here.
Security for AWS integrated in the GravityZone Control Center additionally provides a real-time synchronized EC2 instances inventory grouped by Amazon regions and Availability Zones. You can also generate dedicated reports about Amazon EC2 monthly usage and subscription status.
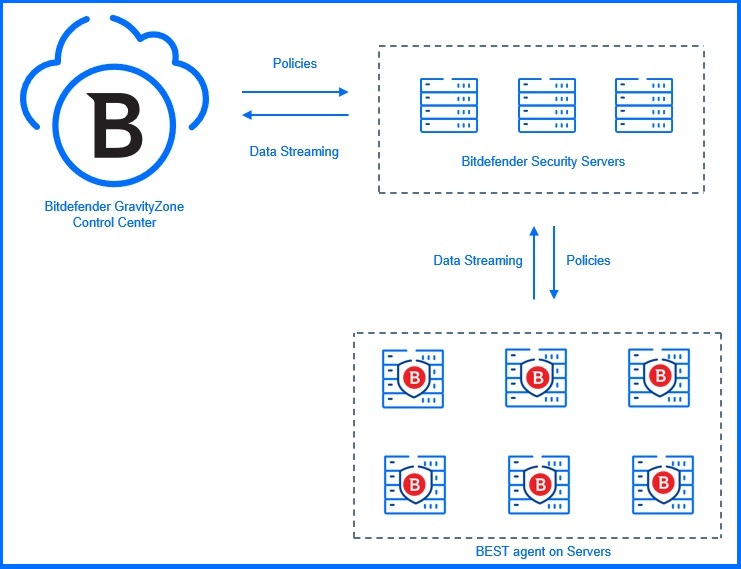
Secondly, you can choose standard BEST agent implementation on AWS with all engines and locally stored signatures. With this approach, all functionalities are accessible and fully operational on the cloud platform.
Security for Microsoft Azure
For Microsoft Azure, you have two security integration models to choose from.
Firstly, leveraging SVE Multi-Platform functionality, you can deploy Security Virtual Appliances (SVAs) manually or directly from the Azure Marketplace. This option offers resource efficiency and minimal performance impact, making it ideal for low-footprint deployments. In this scenario, you can choose to install a lightweight agent with a Security Server component. An agent must be installed on all protected instances and includes Malware Protection, with additional functionalities like Advanced Threat Control selectable by you.
Secondly, you can choose full BEST agent implementation on Microsoft Azure, including all engines and locally stored signatures. With this approach, all functionalities are accessible and fully operational on the cloud platform.
Security for VMware Tanzu
Bitdefender GravityZone offers dedicated integration for VMware Tanzu environments, streamlining the process of securing virtual machines (VMs) managed by the platform's BOSH component. This integration is available through the Integration hub in the GravityZone Console.
This is achieved through a dedicated tile for VMware Tanzu, which automates the deployment of BEST agents directly onto newly created VM instances. To optimize network traffic and distribute updates efficiently, you should install a BEST agent with the Relay role in your IaaS. For centralized scanning, a Security Server must be deployed in your IaaS.
BEST agents include modules like Machine Learning (Local and Cloud-Based), Malware Protection, Process Protection, Sandbox Analyzer, Application Control, and an integrated Patch Management (if available with your GravityZone license).
For more configuration details, check out our Bitdefender Support Center here.
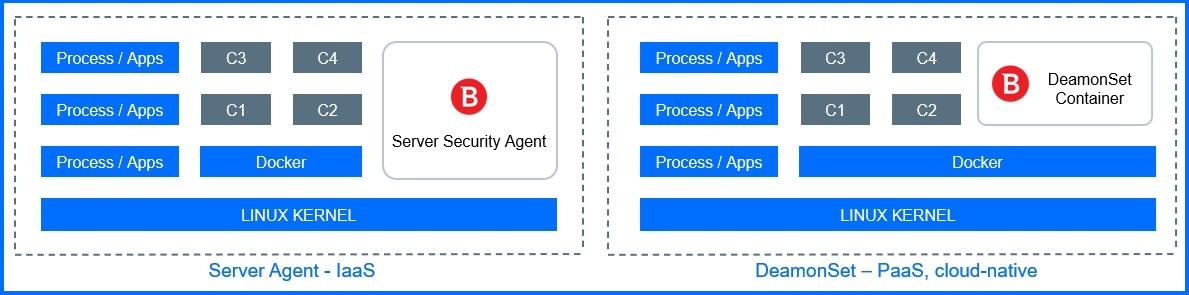
Security for Containers
While containers offer significant benefits for application development and deployment, securing these environments requires a different approach compared to traditional infrastructure. Here are three main methods you can use for container protection:
BEST Agent with Container Protection module: Install the BEST agent on your Linux machine. This provides all available functionalities (except Network Protection) for machine protection, including container scanning with Malware Protection, Advanced Threat Control, Exploit Protection, and EDR. No further configuration is needed for newly deployed containers. For more configuration details, check out our Bitdefender Support Center here.
Security Container: Deploy a dedicated Security Container (BSC) on your Linux host or within your cloud infrastructure platform. Security Container supports all Kubernetes environments (like Amazon Elastic Kubernetes Service (EKS), Azure Kubernetes Service (AKS), Google Kubernetes Engine (GKE) and Amazon ECS) and is deployed using a DaemonSet object. Security Container acts as a shield, protecting both the host system and all running containers. It utilizes features like Malware Protection, Advanced Threat Control, Exploit Protection, EDR and Risk Management. For more configuration details, check out our Bitdefender Support Center here.
Container Image Scanner: Using Bitdefender Container Security Tools command-line interface (bcsc-cli) scans container images from local sources, tarball archives in CI/CD pipelines, or from container registries, including AWS ECR, Azure Container Registry (ACR), and Google Artifact Registry, to identify vulnerabilities and misconfigurations. For more configuration details, check out our Bitdefender Support Center here.
Recommended Content
To learn more about the defense-in-depth security architecture, we recommend reading the next article Security Layers.
More Resources
Bitdefender Cloud Workload Protection official website: Enterprise Grade Cloud Workload Protection
Bitdefender GravityZone Security for Containers official website: GravityZone Security for Containers
For comprehensive insights into Container, we invite you to watch our masterclasses: Containers
For comprehensive insights into KSPM, we invite you to watch our masterclasses: Securing Kubernetes Environments with GravityZone
Protecting your Containerized Infrastructure Guided Tour: Securing Your Containers and Kubernetes Environments
Securing Your Cloud Workloads Guided Tour: Securing Your Cloud Workloads
Securing Your VMs Guided Tour: Securing Your VMs