Mobile Security - Bitdefender TechZone
GravityZone Security for Mobile offers robust Mobile Threat Detection (MTD) for Android, iOS, and Chromebook devices, providing risk identification, threat detection, remediation, and reporting to enhance the overall security posture.
Mobile devices remain connected to the internet 24/7 and serve both personal and business purposes. Some companies are using corporate-owned devices, others adopt Bring Your Own Device (BYOD) policies, permitting employees to utilize their personal devices for work. These devices play a vital role in keeping employees connected, accessing critical information, and sustaining productivity - especially in remote work scenarios. They often serve as conduits to sensitive company data, encompassing emails, documents, confidential records and accessing MFA applications. While this enhances flexibility and productivity, it concurrently exposes security vulnerabilities.
In the absence of adequate safeguards, these devices become susceptible to data breaches, unauthorized entry, and cyberattacks, thereby risking the compromise of sensitive information. Such security breaches can inflict significant harm on a company's reputation. The resultant erosion of trust among customers and partners in the company's data protection capabilities can yield enduring adverse repercussions
GravityZone Security for Mobile is designed to provide organizations with advanced Mobile Threat Detection (MTD) and security for Android, iOS, and Chromebook devices including extensions so that employees can access corporate data in a safe and secure way. It detects both known and unknown threats, including zero-day, phishing, and network attacks. The solutions protect devices against primary attack vectors, even when the device is not connected to a network.
What is Mobile Threat Detection
As the Mobile Security market covers different solutions like MDM, EMM, UEM and MTD it is important to understand the differences.
MDM (Mobile Device Management) focuses on the management of mobile devices. Control system settings, monitor device status, collect inventory, distribute applications, and take remote actions (remote wipe, uninstall app etc.).
MAM (Mobile Application Management) is a system designed to manage and control mobile applications within an organization. Its primary focus is on the management of individual applications, eliminating the complexities and privacy concerns associated with managing entire devices.
EMM, or Enterprise Mobility Management, represents the natural progression in the evolution of MDM (Mobile Device Management). It seamlessly integrates both MDM and MAM approaches into a unified platform.
UEM (Unified Endpoint Management) is the logical next step of EMMs. UEMs target all platforms instead of just mobile devices. Windows, Linux, Unix, Mac, IoT etc.
MTD stands for "Mobile Threat Defense." It refers to security solutions designed to protect mobile devices, such as smartphones and tablets, from various cyber threats and attacks thereby safeguarding sensitive data and maintaining user privacy. It is the only solution responsible for eliminating cyber threats.
MTD serve as an additional layer of defence on top of solutions such as MDM and UEM, enhancing the overall security posture of mobile environments by focusing specifically on identifying, preventing, and mitigating threats and vulnerabilities targeting individual mobile devices and the applications they interact with. Those are not opposing solutions but, rather, can work together.
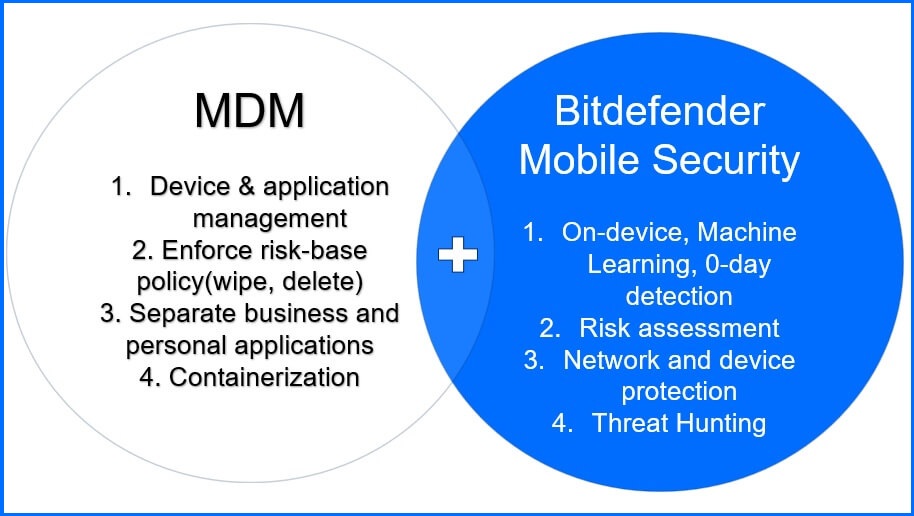
Bitdefender Mobile Security
Security for Mobile was built on three security layers – Prevention, Detection and Response to protect against a wide variety of threats, both anticipated and unexpected. In this section, we will describe in detail the tasks assigned to each layer.
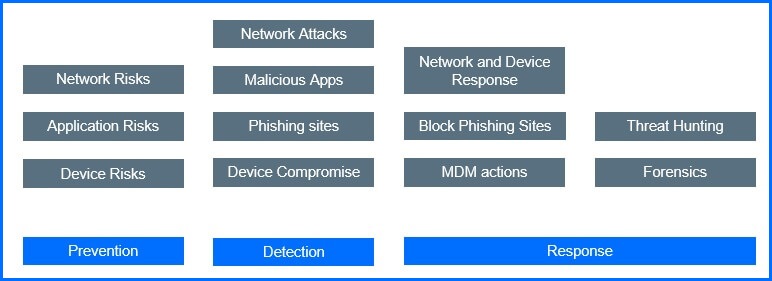
Prevention
The risk identification Prevention layer involves multiple engines of security measures. The initial layer focuses on reducing the attack surface through three main components. First and foremost, the risk of each device needs to be assessed. The administrator will possess a comprehensive global overview of the vulnerabilities present in each device. Security for Mobile proactively identifies operating system vulnerabilities and devices that are unable to receive updates. This overview ensures the efficient prioritization and mitigation of these vulnerabilities. Also, the system will gather information about unmanaged profiles and jailbreaks, which will enhance security measures and provide a more thorough identification of potential risks.
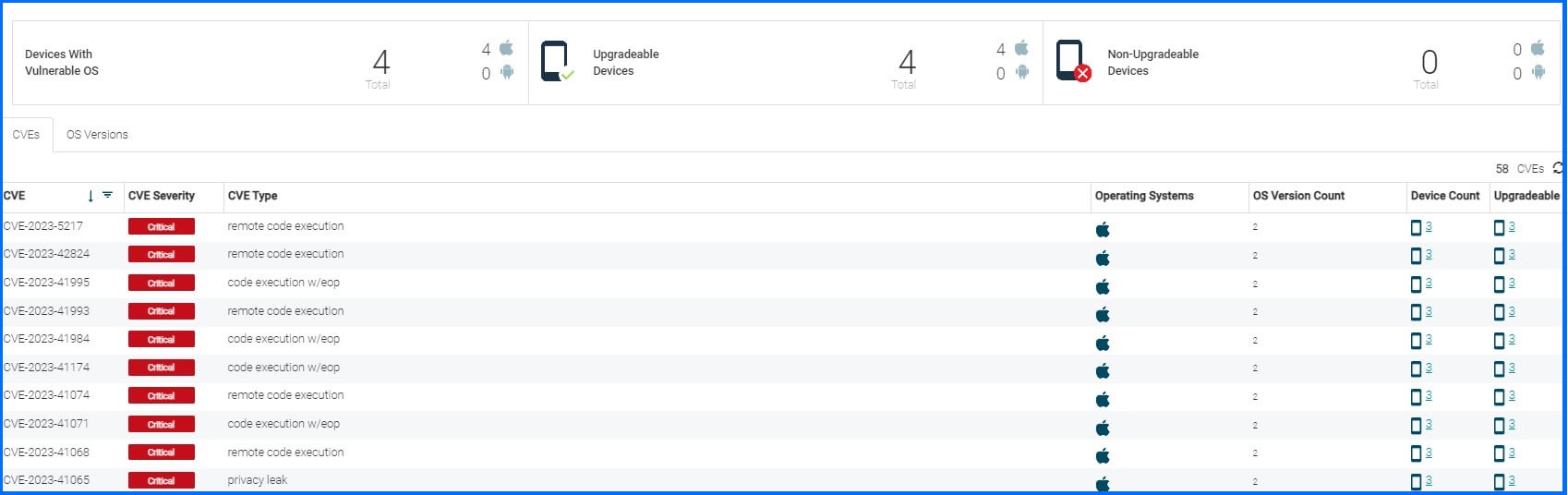
Figure 1 - OS Vulnerabilities Risk Report
Secondly, the administrator will be able to assess application risks based on secure coding and privacy practices. It involves safeguarding user data against unauthorized access, disclosure, or modification. Administrators have the flexibility to establish policies tailored to predefined characteristics. These may include actions such as transmitting contacts to a remote server or sending data off the device, encompassing user information, videos, and images, among other elements. Furthermore, secure coding must be a continuous endeavor to tackle evolving security threats and vulnerabilities. As end users, we lack the capability to directly improve the security of applications. However, administrators can enhance security through app policies, conducting scans to identify potential vulnerabilities or attempts to access vulnerable instances within applications.
Moreover, in-depth app vetting analysis provides insight into the "third-party application currently active on the device," assisting in uncovering any attempts at application tampering. As an illustration, implementing shared library cross-checks serves to prevent the replacement or modification of the library by hackers.
Administrators additionally gain a comprehensive understanding of agent tampering, indicating a compromise of the agent itself. For example, if the existing application libraries have been modified or a foreign library has been injected into the application, this can lead to unintended changes in program behavior, system instability, and potential security vulnerabilities. The injected code may be executed with the same privileges as the compromised application, posing a significant risk to the overall integrity and confidentiality of the system. Detection of this compromise is possible through the App Tampering threat policy.
GravityZone Security for Mobile incorporates a robust application vetting system that enables the identification of non-compliant applications. This feature empowers security teams to establish a repository of approved applications and their corresponding versions. It allows each business to tailor an "application compliance" policy, construct a repository of authorized app editions, and oversee endpoints accordingly. Besides the manual vetting administrators can benefit from using auto-detection of unapproved applications.
With over 180 detection points, which is a market-leading number, Security for Mobile provides an unmatched level of precision, granting unparalleled administrative control. This functionality extends to assessing applications' security and privacy aspects, ensuring adherence to regulatory standards.
Lastly, considering network risk, the administrator can identify unsecured Wi-Fi connections and recognize all reconnaissance scans. Unsecured Wi-Fi can expose sensitive data to potential attackers through MiTM (Man-in-the-Middle) attacks, where the attackers can intercept all sessions and access all the information.
Detection
GravityZone Security for Mobile employs on-device machine learning to detect both known and unknown threats. Threat detection encompasses four primary areas to safeguard users. The initial phase ensures the integrity of the device used by the user, verifying that it has not been compromised. This verification is based on the detection of factors like elevated privileges, system tampering, and rooted devices, all aimed at ensuring a secure mobile environment. It is important to highlight that certain threat alerts, such as Pegasus, disabled SELinux, Jailbreak, etc. necessitate a factory reset instead of firmware restoration. The primary reason for this lies in the fact that a factory reset solely erases user data on the device, leaving OS files untouched. This implies that malicious or modified OS files continue to exist on the device. On the other hand, factory firmware restoration not only clears user data but also replaces the OS by overwriting the previous version. All MDM solutions offer only factory reset capabilities and cannot protect a mobile device against OS tampering. Firmware restoration necessitates physical access to the device and the original OS file from the mobile device vendor.
The subsequent step entails identifying phishing sites within web browser links and links received via SMS. Additionally, administrators can configure further content categories for permitting or blocking access to specific types of content. The administrator can access over 70 categories assigned to 10 distinct groups, including Security Risk, Adult Content, Business, and more.
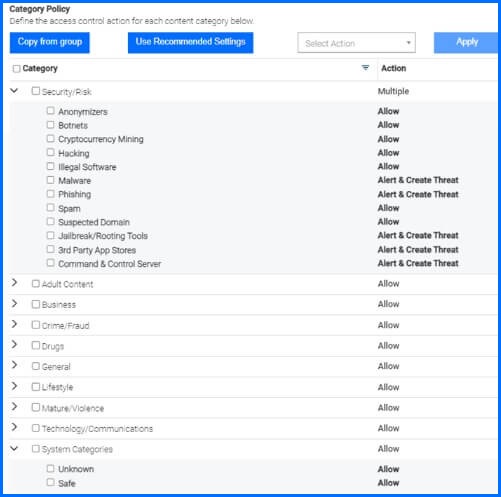
Figure 2- Access control category policy configuration
If a false positive occurs and the local engine update is pending, the administrator can set up exclusions using the custom access control list provided in the "Access Control" section under "Manage".
Of utmost importance is the ability to identify malicious applications on the mobile device, thereby protecting user data and proactively preventing potential security breaches, all while ensuring protection even in offline endpoints.
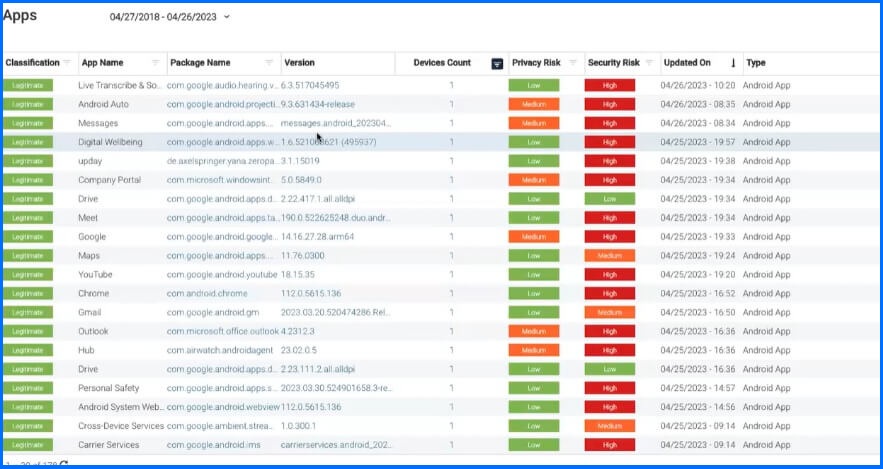
Figure 3 - Application log report
It is important to note that we do not have control over preventing users from installing applications. This capability resides on the MDM side. Our role is centred around our cybersecurity expertise, which involves monitoring and potentially blocking applications. Additionally, MTDs benefit from not being classified as MDMs, as they do not have to handle, nor do they force customers to deal with, the burdens of management and privacy regulations that come with MDMs. MDMs, by their nature, are not privacy-friendly, especially in the context of BYOD, as they obtain management rights on a device, even if they are not actively used. This is the reason why MAM solutions were developed.
Out-of-the-box Android app lists become accessible after the agent's installation. However, for iOS, due to the system architecture, integration with MDM is necessary to gather information about installed applications on mobile devices. Thanks to this integration, in some cases, applications might even be reported before they are installed. The Mobile Security console can report an application that is in the installation pending state.
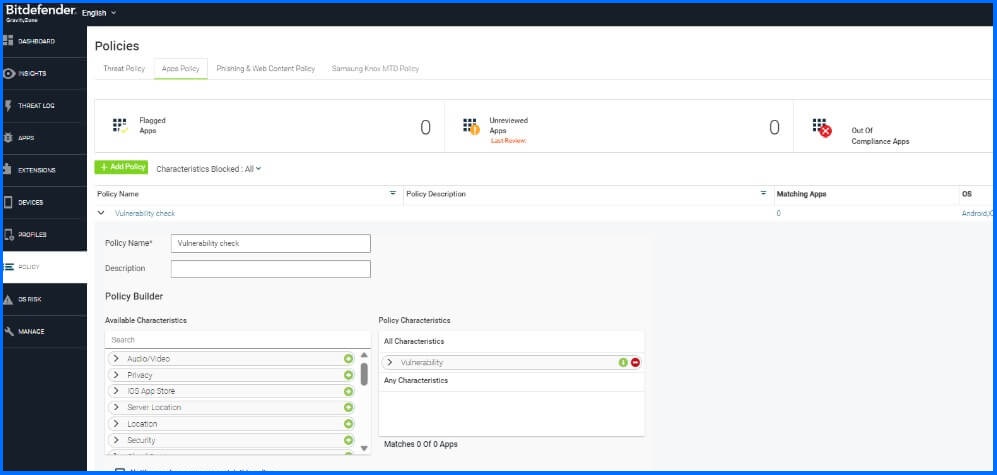
Figure 4 - Application Policy configuration
Lastly, the capacity to identify network attacks, including rogue access points and MiTM attacks, is essential to uphold data transmission integrity and ensure a robust defence against unauthorized intrusion attempts. By doing so, it effectively mitigates the risks of data theft and credential loss, while also offering enhanced visibility into potential threats.
Response
All remediation policies can be configured within GravityZone Security for Mobile. However, in some cases, additional integration with the MDM solution may be required.
Within Security for Mobile, the treatment of all phishing sites can be determined based on configuration choices, which can be executed within the "Phishing Protection and Web Content Filtering" section of the Policy configuration.
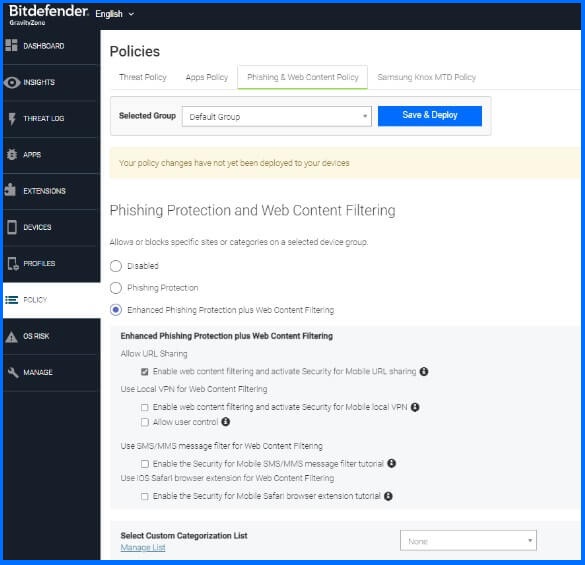
Figure 5 - Phishing protection and Web Content filtering configuration
In numerous companies, mobile devices do not possess the same level of security as traditional endpoints. Given their smaller screens and limited URL scrutiny space, users on mobile devices are inherently more susceptible to phishing tactics. This is one of the reasons why phishers frequently carry out attacks across various platforms, encompassing email, social media, and SMS. By installing GravityZone Security for Mobile, implementing phishing protection on mobile devices becomes an effective shield against multi-platform attacks, safeguarding users from falling victim to them.
Network and Device Response
Network Response relay on defined by administrator policy, where they have at their disposal various actions such as disconnecting Wi-Fi, disabling Bluetooth, or, in the case of Samsung Knox, uninstalling or disabling applications, or isolating from the network. Additionally, to notify users about future actions that have to be done administrator can configure “User alert” depending on the type of threat.
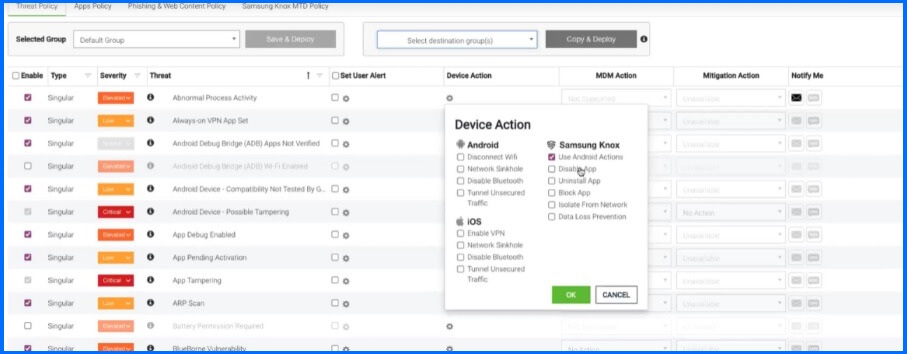
Figure 6 - Threat Policy configuration
Should administrators need to terminate access, remove applications, lock, or wipe a device for any reason, it will necessitate supplementary MDM integration.
Threat Hunting
Threat Hunting is available for Android, iOS, and Chromebook Applications. This cloud-based feature enables a comprehensive exploration of the security and privacy behaviours exhibited by all applications operational on safeguarded devices. This functionality supplies both execution and technical-level reports, facilitating thorough analysis. Moreover, it grants insight into all iterations that are analyzed by Bitdefender, not limited to those detected in the customer account. This empowers the administrators to effortlessly trace an application's history and make informed decisions pertaining to each application and its respective versions.
Forensics
Security teams can collect and analyze valuable data from mobile devices, enabling in-depth investigations into security incidents and breaches. This includes capturing information about the behaviour of apps, network connections, and system activities. This forensic data can then be used to reconstruct events, identify vulnerabilities, and determine the extent of compromise in the event of a security breach.
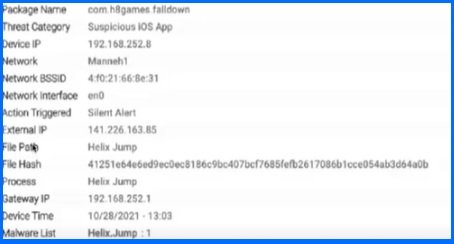
Figure 7 - Forensic details
All the reports with additional Mitre's Tactics information are available under the Threat Log section where the administrator can also define the Action for discovered threats,
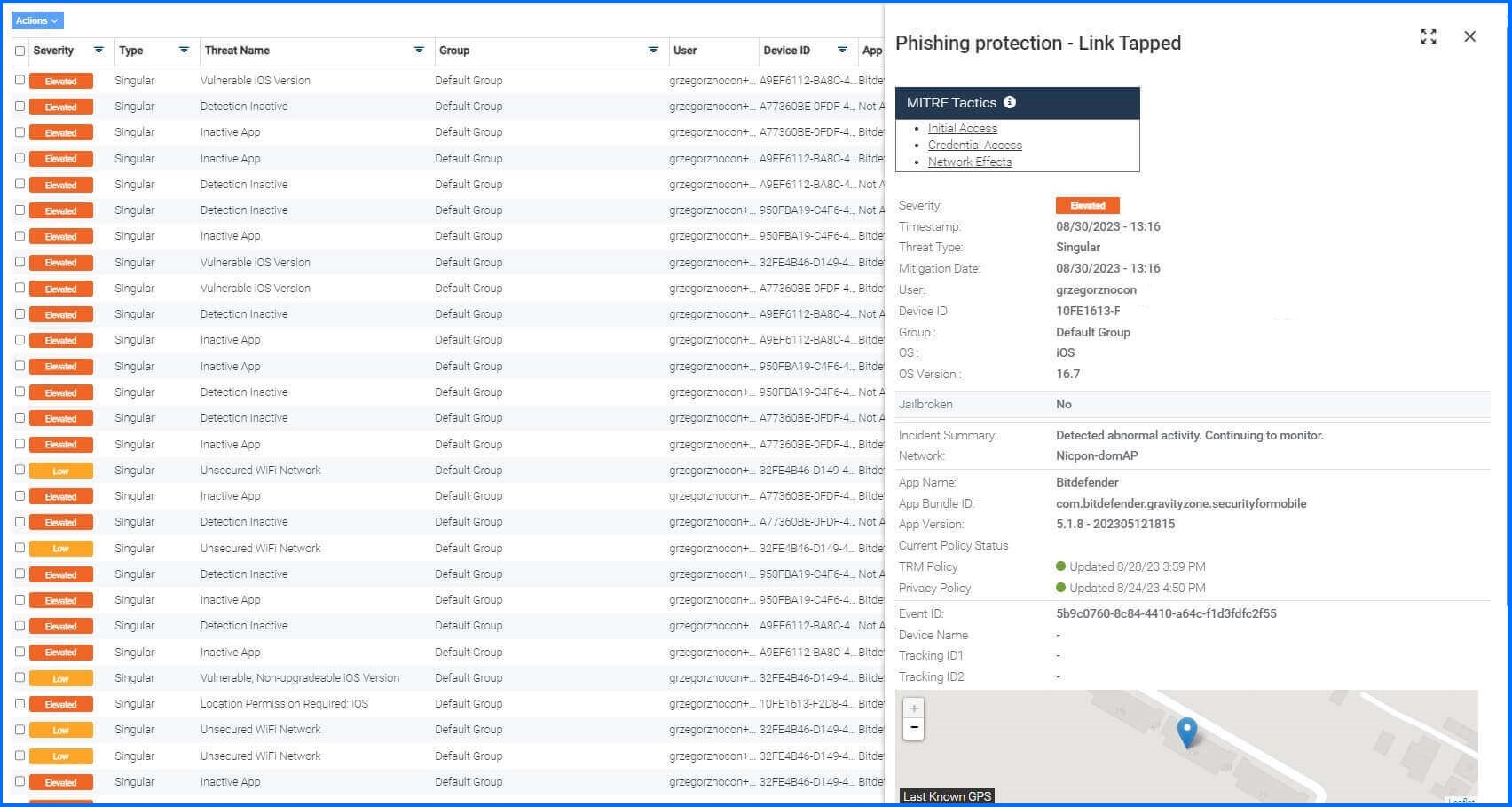
Figure 8 - Mobile Security - Threat Log details
Forensic data is contingent on the global configuration, which can be managed in the "Privacy" section under "Manage".
MDM integration
Through MDM integration, administrators gain the capability to push installations of the Bitdefender GravityZone Security for Mobile applications. This integration facilitates the synchronization of all management devices, along with their respective groups and device information, into a unified location. Note that profiles become accessible only after MDM integration.
What is worth emphasizing thanks to the integration with the MDM platform administrators can implement additional remediation actions like wiping the device or enforcing security policies like application control to enhance the protection and control over mobile devices. Additionally, the MDM platform creates an application inventory for iOS devices.
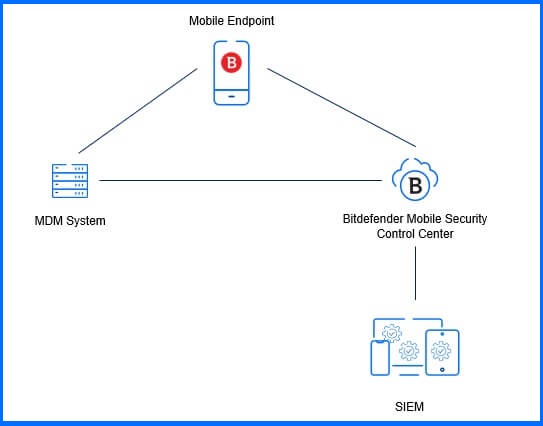
Figure 10 - Bitdefender Mobile Security integrations schema
Integration of GravityZone Security for Mobile is possible with various MDM platforms. The available capabilities for administrators vary based on the specific MDM platform. You can access the MDM capabilities matrix on ours Support Portal.
SIEM integration
Integrating mobile security with SIEM systems is crucial in today's interconnected and digital landscape. Administrators can gain visibility into mobile-specific threats, vulnerabilities, and incidents. This helps in creating a more comprehensive picture of your organization's security posture and can trigger alerts and automated responses based on predefined rules. This ensures that potential mobile security threats are promptly addressed, minimizing the risk of data breaches or unauthorized access.
Administrators can choose from predefined SIEM systems out of the box, but they are not limited to only those options. All data from Bitdefender Mobile Security can be sent in JSON format, which contains all the collected data about the device and threats. Key sections in the JSON include:
event_id
Forensics
user_info
device_id
threat
This facilitates the investigation of the incident, comprehension of its extent, and implementation of necessary measures to avert future instances. All of this information enhances the capabilities, fostering a more comprehensive and unified security stance that integrates mobile devices into the organization's overarching security strategy.
The integration instruction with solutions like AlienVault, Splunk etc. is available on our Support Portal under the link GravityZone Security for Mobile SIEM Integrations.
Dashboard console
The management console's dashboard provides a unified view of protected devices, security insights, and events, regardless of their grouping. It is divided into multiple sections, each offering an overview of inventory status and security intelligence.
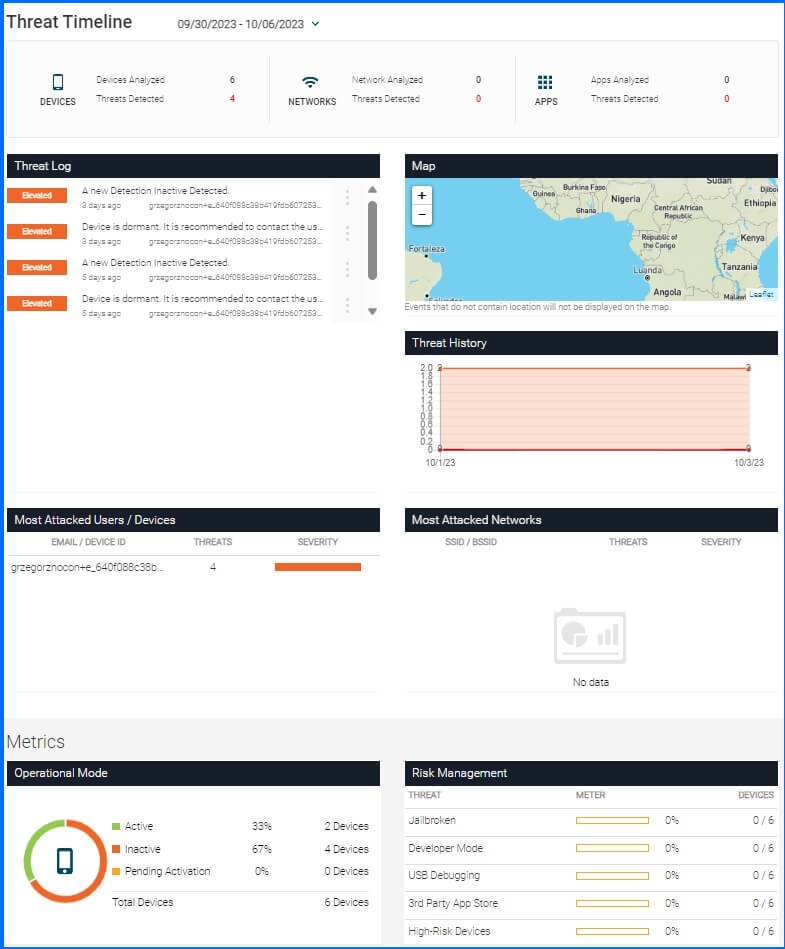
Figure 11 - Mobile Security Dashboard page
Within the Dashboard page, administrators will also discover the latest Threat Log, which serves as a repository for all ongoing security events. Administrators can perform various actions on each event, including approval, resolution, or triggering an MDM Action.
Recommended Content
To learn more about detecting threats that have evaded prevention and protection technologies we recommend reading the next article Detection.
More resources
Bitdefender GravityZone Security for Mobile official website: GravityZone Security for Mobile
Bitdefender GravityZone Security for Mobile Guided Tour: Security for Mobile Guided Tour
Discover the Mobile Security full potential with our dedicated video masterclasses: Masterclass