Threat Hunting – Bitdefender TechZone
Explore threat hunting with Bitdefender. Discover GravityZone's capabilities for your team or leverage expert MDR services to proactively find hidden malicious activity.
Threat hunting in cybersecurity is a proactive approach where security professionals actively search for and identify previously unknown or ongoing cyber threats that have evaded existing security measures, often using digital forensics and incident response tactics. While traditional threat detection reacts to alerts, threat hunting proactively searches for hidden malicious activity by leveraging both human analysts' skills and advanced technologies to analyze data and identify patterns.
Bitdefender offers comprehensive threat hunting capabilities through two models: the GravityZone platform, which empowers your internal security team, and the Managed Detection & Response (MDR) service, which leverages Bitdefender's expertise. By understanding the distinct advantages of each, you can select the solution that best aligns with your organization's security needs.
Understanding Cyber Threat Hunting
Key characteristics include its proactive nature, being initiated by analysts rather than solely by alerts, its human-centric reliance on analyst expertise and intuition, and its threat-focused targeting of specific threat actors and tactics. It is important to distinguish threat hunting from related practices. Penetration testing evaluates security posture through simulated attacks but does not continuously monitor for ongoing threats. Alert investigation is a reactive response to triggered alerts; threat hunting searches for activity before alerts are generated.
Threat hunting is a human-driven security process that focuses on generating actionable intelligence about vulnerabilities and Tactics, Techniques, and Procedures (TTPs) that could be used against an organization. It goes beyond automated detection and simple indicators of compromise (IoC) hunting by incorporating risk assessments, vulnerability analysis, or patch status reviews. This approach allows analysts to proactively identify and mitigate potential threats from advanced actors like APTs and sophisticated ransomware, who often employ techniques designed to evade standard detection systems.
Actionable intelligence is a key focus, based on threats located on the dark net specifically targeting your environment, new industry-wide TTPs, and threats targeting specific applications or vulnerabilities. This intelligence provides context and direction for hunting activities.
Risk assessment plays a vital role in threat hunting. This includes identifying known vulnerabilities in your environment that are actively being exploited, as well as analyzing anomalous user activity that increases the likelihood of a successful attack. Examples include downloads from suspicious websites, interactions with phishing emails, and the use of unlicensed software. By focusing on actionable intelligence and risk, threat hunters can prioritize their efforts and proactively address the most critical threats.
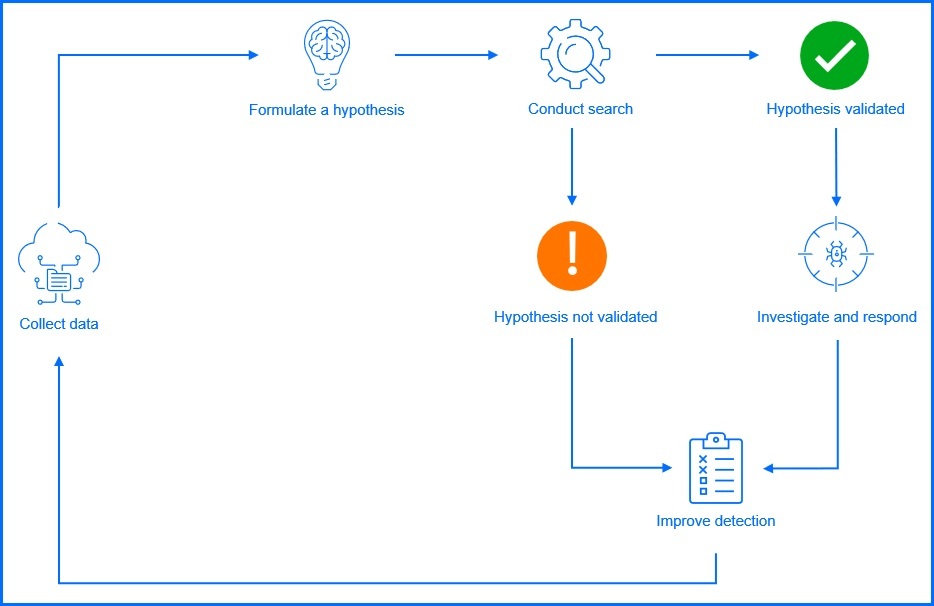 Simplified flow of Threat Hunting, an incident response without an incident. |
GravityZone Platform Support for Threat Hunting
GravityZone offers several options for implementing threat hunting within your environment.
Threat Hunting Without Data Retention Constraints
GravityZone's default threat hunting capabilities deliver efficient investigative features at no additional cost. It offers 90-day retention for alerts and incidents. The Live Search functionality, powered by Osquery, enables real-time querying of endpoint data. For example, using Osquery, a sysadmin can run the query: select name, path, cmdline from processes where name = 'powershell.exe' to look for unusual PowerShell activity.
GravityZone Live Search |
Importantly, Historical Search also enables querying historical alerts and incidents up to 30 days old. This historical access is achieved by querying data in GravityZone.
GravityZone Historical Search |
To move beyond behavioral analysis, you can use YARA rules within the GravityZone platform to create custom, content-based signatures for hunting specific malware or zero-day exploits. These finely tuned, organization-specific patterns empower your security team to identify and classify malware families or threat actors based on their internal characteristics. Once deployed, a YARA rule operates in two modes: On-access (real-time detection) and On-Demand (manual scan for proactive hunting). When a rule matches a search, you can define an automatic action to be executed, ensuring rapid isolation and containment of the threat.
GravityZone YARA rules |
Threat Hunting with Retention Requirements
For organizations needing independent control over raw telemetry collection, the GravityZone Retention Add-on offers a solution. It allows for the continuous collection and transmission of raw telemetry, separate from incident-triggered events, alongside extended retention periods for alerts and incidents. These periods can be set to 90, 180, or 365 days, providing the flexibility required for compliance and in-depth historical investigations.
GravityZone Raw Events |
Threat Hunting with an Existing SIEM
Some security teams prefer a single SIEM platform for threat hunting. For these cases, GravityZone offers two integration options. First, agents can be configured via policy to automatically forward telemetry data to your SIEM. Second, dedicated connectors enable GravityZone to forward all alerts and incidents. Both methods allow for the correlation of endpoint data from GravityZone with other security logs collected by the SIEM.
For organizations that do not already have a third-party SIEM or wish to leverage a purpose-built security architecture, the Bitdefender Security Data Lake serves as a high-performance, centralized platform for proactive threat hunting by transforming fragmented telemetry from network devices, operating systems, applications, and cloud services into actionable intelligence. This process begins with the real-time ingestion and normalization of diverse formats like JSON, NetFlow, or Syslog, allowing you to correlate suspicious activities, such as a cloud login followed by lateral movement, across previously siloed platforms.
To power your hunts, the platform utilizes Pipelines for real-time data enrichment, Anomaly Detection to identify deviations from normal activity, and Sigma Rules to identify adversary behavior, such as zero-day exploits and active APT campaigns. In the Investigations module, you can centralize all logs and evidence into a unified timeline to view the full context of an issue, accelerating both Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR).
Bitdefender MDR Threat Hunting Services
Bitdefender MDR provides a managed threat hunting service, ideal for organizations looking to outsource or augment their threat hunting capabilities. The MDR team starts by conducting threat modeling to understand your specific environment, followed by establishing a baseline of normal activity.
The quality of Bitdefender’s MDR threat hunting is significantly enhanced by its robust threat intelligence, derived from the Global Protective Network, which collects real-time data from millions of endpoints. This massive, real-time data stream is then analyzed by Bitdefender's security researchers and threat hunters. This combination of extensive real-time data and expert analysis adds context, identifies patterns, and validates the IoCs, filtering out false positives and ensuring intelligence is actionable.
Risk-based threat hunting involves proactive identification of emerging threats based on industry, location, and technology, with targeted hunt packages developed by our dedicated Cyber Threat Intelligence (CTI) team. For example, for organizations in the healthcare sector, risk-based hunting may focus on detecting techniques used by ransomware groups targeting medical data.
Targeted threat hunting involves regular (bi-weekly) analysis of endpoint data for anomalies, detection of deviations from baseline behavior in user activity, application activity, and network data, and a focus on detecting advanced threats, zero-day exploits, and insider threats. For example, a targeted hunt might involve analyzing endpoint logs for unusual living off the land commands execution or attempts to modify critical system files.
More Resources
Bitdefender Support Center: GravityZone data retention policies
Bitdefender Support Center: Raw Events types supported